User Datagram Protocol (UDP)
This is a transport layer protocol used primarily for low-latency and loss tolerating connections. Defined by RFC 768 It provides a best-effort datagram service to an End host. let’s discuss the UDP and UDP Structure in more detail.
In contrast to TCP, UDP just sends the packets with no packet acknowledgements which leads to much lower bandwidth overhead and latency. But packets can be lost or received out of order as a result, owing to the different paths individual packets traverse between sender and receiver.
Related- TCP vs UDP
UDP provides a procedure for the source host to send messages to the destination host with a minimum of protocol mechanism. UDP is transaction-oriented, and delivery and duplicate protection are not guaranteed.
UDP uses a simple transmission model but does not employ handshaking dialogues for reliability, ordering and data integrity. The protocol assumes that error checking and correction is not required, thus avoiding processing at the network interface level.
UDP is widely used in video conferencing and real-time computer games. The protocol permits individual packets to be dropped and UDP packets to be received in a different order than that in which they were sent, allowing for better performance.
Related- NETSTAT – TCP/UDP Active Connection Display Tool
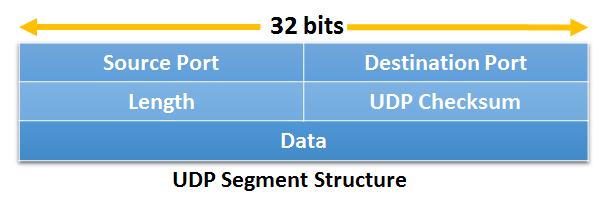
UDP HEADER STRUCTURE (UDP Structure)
The UDP header consists of four fields each of 2 bytes in length –
- Source Port (16 bits) – This field identifies the sender’s port. Cleared to zero if not used.
- Destination Port (16 bits) – This field identifies the receiver’s port.
- Length (16 bits) – The length in bytes of the UDP header and the encapsulated data. The minimum value for this field is 8.
- Checksum (16 bits) – The checksum field may be used for error-checking of the header and data. This field is optional in IPv4, and mandatory in IPv6. The field carries all-zeros if unused. Needed with zero bytes at the end to make a multiple of two bytes. If the checksum is cleared to zero, then the checksum is disabled. If the computed checksum is zero, then this field must be set to 0xFFFF
Related- How To Forward UDP Broadcast On Cisco Routers
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj