Table of Contents
If your organization uses CI/CD pipelines for software development, you’re moving quickly to write code, build your applications, and deploy the software. However, DevOps speed doesn’t do you any good without AppSec, which is imperative for a well-secured and functional app. To make sure AppSec is included during the software development lifecycle, apply application security tools to your pipeline.
The Role of the CI/CD Pipeline
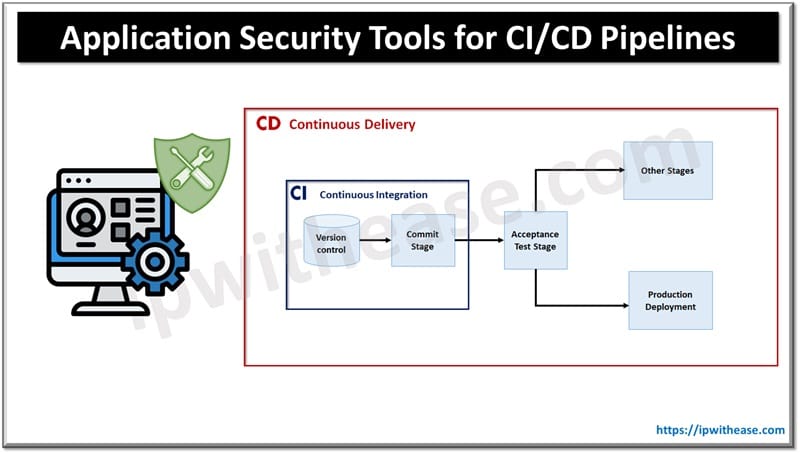
The continuous integration and continuous deployment pipeline, more briefly known as the CI/CD pipeline, is the automated process by which new software or new updates are pushed out to users. The goal is to streamline the DevOps process. When a developer has begun building the software, the CI/CD pipeline provides automated testing for bugs and other issues in the code.
During development, continuous integration (CI) is used to keep developers on the same page. When team members make changes, these changes are transmitted back to a central location often known as the “trunk” where they are merged with the rest of the code. When you’re working on a shared document in a Google application, changes that you make update for everyone else in real time.
Just as this prevents multiple people from trying to remove a comma in the same sentence, CI prevents confusion between developers and prevents issues in the code that stem from uncommunicated changes. If you integrate tools, automated testing kicks in as soon as the changes are merged to ensure nothing has been broken.
Continuous deployment involves the automated process of releasing the software (or updates) to the users. This significantly shortens the time between code writing and release. Although releasing code so quickly can sometimes be risky, this is mitigated by the automated bug and AppSec testing built into the CI/CD pipeline. This is a vital component of the pipeline.
Next-Gen AppSec Tools
Integration and automated security testing are critical for a smooth, fast deployment. For best results, AppSec must be included during development. To have an effective CI/CD pipeline, security cannot be an afterthought and must be considered during design.
Also, choose tools that are best equipped to provide the most accurate vulnerability detection and protection. Technological advances have made it easier than ever for attackers to launch highly sophisticated attacks, so your tools have to be able to keep up.
Advanced application security tools that you may consider:
- Containerization. Packaging your software into containers keeps the software (and thus its vulnerabilities) isolated. As a result, weaknesses in the infrastructure running the software do not create vulnerabilities in the software itself.
- AI. To combat the threats that are, in some cases, using AI to slip past your defenses, consider defensive AI. Implement tools that are AI-driven, which will detect more subtle attacks and prevent infiltration with greater precision than traditional tools.
- Automated Application Security Testing. High volumes of threats make manual testing next to impossible, so you should be implementing automated monitoring, testing, and authentication tools. Finding known vulnerabilities within your application’s code is imperative for staying ahead of potential attackers.
- Web Application Firewall. Implementing a WAF will reduce the number of attacks that make it through to your application’s code. This is the first line of defense that detects and blocks attacks by identifying unusual activity.
- Runtime Application Self-Protection. If an attacker successfully infiltrates your security environment and accesses your app, it’s likely that your app will begin behaving differently than it is supposed to. RASP monitors application behavior and will block it when necessary.
- Software Composition Analysis. SCA scans any third-party code or application building blocks your developers are using for vulnerabilities.
- SAST/DAST/IAST. Static, dynamic, and interactive application security testing tools look for errors in code (SAST) and runtime issues (DAST and IAST). Between the three of them, they ensure that there aren’t any glaring issues with your code before deployment.
- MAST. Mobile application security testing searches for mobile-specific threats. Mobile devices frequently interact with different Wi-Fi networks, for example, and MAST is helpful for determining whether a network connection poses a threat.
This is not an exhaustive list, but tools like these and others are ways to effectively reduce vulnerabilities during app development. Your team should aim to eliminate as many weaknesses as possible during the integration and security testing phases of the CI/CD pipeline. Once your software is deployed, it is open to attack.
Building DevSecOps with Shift-Left Security
You really want to take care of as many vulnerabilities as you can before your software goes live, but as a rule, earlier is better. If you can address the vulnerabilities during initial code writing and early development, your security will ultimately be better. This earlier approach is called shift-left security.
Addressing security earlier in the software development lifecycle will reduce the cost and impact of vulnerabilities. Catching them early means developers can change the code more quickly. Waiting to fix problematic code will cause components of your software to be built on that faulty code, which means more will have to be redone to address the issue.
If your software makes it past deployment without a fix, there is a significant risk of exploitation that could lead to lost revenue and fines for noncompliance with privacy regulations and standards. Neglecting to secure your software will almost certainly cost you, and it will cost you more if you put off addressing the issue.
By using automated, next-gen AppSec tools during the DevOps process, you can address most issues with your software right away. Development cycles for software are constantly getting shorter, and to keep up, you need to have a smoothly running CI/CD pipeline that is fully integrated with automated security tools and vulnerability testing. If you set that up well and ensure that security is considered at all phases of development, you can release a superior product at a lower cost.
Continue Reading:–
Difference between Continuous Integration and Continuous Delivery
DAST – Dynamic Application Security Testing
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.