Table of Contents
In today’s digital world, cyber security tests are essential to ensure the safety of your organization’s sensitive data and systems. Cyber security tests help identify vulnerabilities and weaknesses before attackers can exploit them. Conducting regular tests is key.
This article will guide you on how to conduct effective cyber security tests to protect your organization.
Read on!
Understand the Need for Cyber Security Tests
Cyber security tests identify security gaps in your systems. They help protect your organization from cyberattacks. Regular tests keep your network safe from new threats. The tests will help you detect vulnerabilities early.
They ensure compliance with security standards. A strong security posture boosts customer trust. Tests show you where your defense is weak. Understanding these needs is the first step.
Plan Your Cyber Security Test
Planning is essential for an effective test. Know what systems you want to test. Determine the test scope clearly. Establish timelines for the tests. Set goals for each test to measure success.
Understand what you hope to discover. Ensure you have the right tools. Planning minimizes errors during testing.
Choose the Right Security Tester
A skilled security tester is important. A security tester will guide you through the process. They should be experienced in handling real-world threats. Look for testers with good communication skills.
They must also be familiar with the latest security tools. A professional will work within your organization’s needs. They should be trustworthy and reliable. Find someone with the proper certifications.
Conduct a Vulnerability Assessment
A vulnerability assessment helps identify weaknesses. This can be done using automated tools. The process checks for potential entry points in your network. It reveals where attackers could exploit systems.
Review the results to prioritize the fixes. Identify critical vulnerabilities first. Patch these weaknesses quickly to prevent attacks. Regular vulnerability scans are a must.
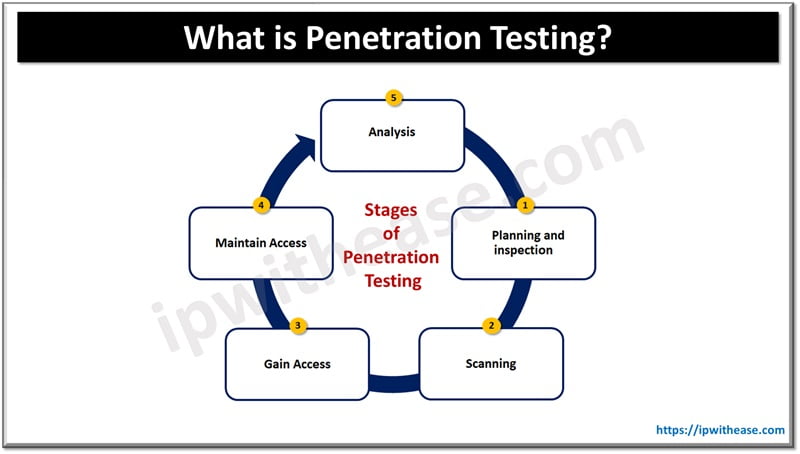
Perform Penetration Testing Steps
Penetration testing steps simulate real-world attacks. Test your systems as if you were a hacker. Start with reconnaissance to gather information. Then, attempt to exploit identified vulnerabilities.
Penetration tests also check system resilience. A good penetration test will test both internal and external threats. Record all findings in detail. After the test, fix the weaknesses found.
Test Web Applications with Web Application Pentesting
Web application pentesting focuses on web security. It checks if attackers can exploit web applications. Look for vulnerabilities in coding and configurations. A thorough test reviews user inputs and security settings.
It also checks for data protection flaws. Test how the application behaves under pressure. Identify any threats that could damage the app. Regular tests keep your applications secure.
Evaluate Your Network Security
Network security is a critical part of cyber security tests. Focus on:
- firewalls
- routers
- switches
Make sure the network is well-configured. Monitor for unauthorized access and data leaks. Assess internal and external network traffic. Conduct tests regularly to avoid unknown threats. Review network protocols and ensure encryption. A secure network supports overall system security.
Conduct a Social Engineering Test
Social engineering tests help identify human weaknesses. Attackers often trick employees into giving up access. Test how staff respond to phishing and baiting tactics. Create mock phishing emails and observe responses.
Train your team based on these tests. Ensure everyone is aware of the risks. Social engineering testing helps build better security awareness. It is essential for reducing human error in security.
Perform a Risk Assessment
A risk assessment helps prioritize security risks. Assess the probability of each threat. Understand the impact of potential security breaches. Focus on high-risk areas first.
Weigh the cost of mitigation against the potential damage. Risk assessments guide your overall security strategy. Address the most critical threats quickly. This helps focus efforts on where they’re most needed.
Implement Regular Security Audits
Security audits ensure continuous protection. Regular audits help you stay updated. Audit your systems, processes, and policies frequently. Check for compliance with industry standards.
Review employee behavior and access logs. Find any areas that need improvement. Audits identify vulnerabilities that tests may miss. This proactive step strengthens your security framework.
Collaborate with Penetration Testing Companies
Penetration testing companies offer expert help. They bring advanced tools and expertise to your tests. They can simulate complex cyberattacks. Working with professionals saves time and effort.
These companies follow best practices to test systems. Their in-depth analysis uncovers hidden weaknesses. Partner with experts for thorough testing. Consider their services for specialized needs.
Review Test Results and Create an Action Plan
After tests, review the results in detail. Identify what went wrong during the tests. Create an action plan to fix vulnerabilities. Prioritize fixing the most critical weaknesses.
Communicate the results with your team. Plan how to address the problems found. Regular follow-up is necessary to track progress. Updating security measures based on results is crucial.
Train Your Team Based on Test Findings
Training your team is vital to secure your organization. After testing, educate your employees on security best practices. Share test results and highlight important lessons. Conduct workshops on avoiding cyber threats.
Ensure employees understand phishing and malware risks. Provide ongoing training to maintain awareness. Secure employees help build a strong defense. Regular training improves your organization’s overall security.
Use Automation Tools for Continuous Testing
Automation tools help streamline cyber security tests. They allow you to run tests continuously. These tools scan for vulnerabilities regularly without manual intervention. Automation saves time and ensures consistent testing.
Set up automated scans to detect new threats. Use tools that integrate with your existing systems. Automation also helps prioritize risks quickly. It supports faster response times to emerging vulnerabilities.
Monitor and Update Security Measures Regularly
Security is an ongoing process, not a one-time test. Regularly monitor your systems for any new threats. Update your security measures to keep up with evolving attacks. Patching and updates should be done promptly.
Review security settings and policies periodically. Continuously improve your defense mechanisms. Stay informed about new vulnerabilities in the market. Ongoing monitoring ensures your security remains robust.
Conduct Effective Cyber Security Tests for Your Organization
Conducting cyber security tests is vital to ensure your organization’s systems stay protected. Regular information security assessments and web application pentesting help maintain robust security. Collaborating with penetration testing companies can provide valuable insights.
Always prioritize fixing weaknesses and train your team for ongoing security. By following these steps, your organization will be better prepared to face emerging threats.
To read more, visit our blog page. We do have more topics!
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.