Table of Contents
An SMB with a robust cybersecurity strategy is a powerful signal of client trust. These strategies must be ready to face any digital security challenge head-on. Such readiness depends on integrating the latest cybersecurity measures for authentication, employee training, data backups, disaster recovery, and more.
All businesses large and small would benefit from conducting a cybersecurity audit. This step is an excellent starting point, helping teams identify areas of improvement, opportunities for automated integrations, and more secure data management.
Discover the latest 2026 cybersecurity trends for smart businesses.
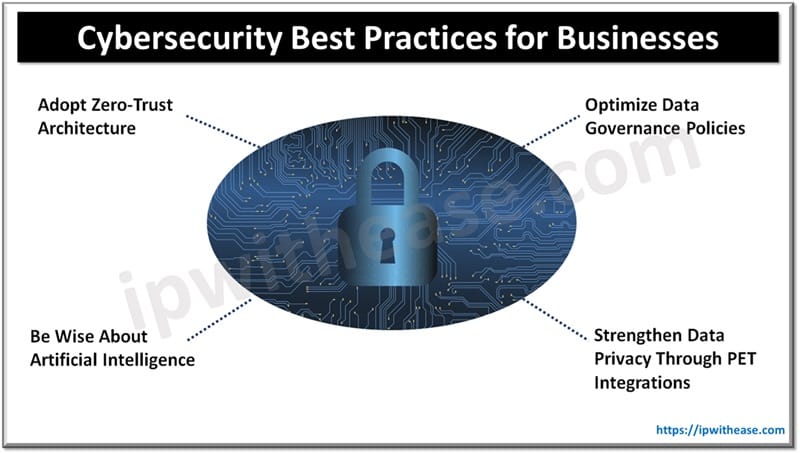
1. Adopt Zero-Trust Architecture
One of the most talked-about cybersecurity innovations in the past year is zero-trust architecture. The philosophy of a zero-trust framework is simple; don’t trust, authenticate. This mindset is necessary for integrating multi-factor authentication, another cybersecurity trend that’s quickly being adopted.
ZTA-built cybersecurity systems continuously verify identities and program permissions to ensure no internal or external threats slip through the cracks.
ZTA is more valuable than ever in the age of remote and hybrid work.
While these work models benefit businesses in several ways, they also increase the risk of lateral movement attacks which allow cyber criminals to access remote devices more easily to retrieve sensitive application data. Businesses should optimize zero-trust strategies by enforcing strict remote device policies that ensure employees only work from secure devices provided by the company.
This philosophy is also an opportunity to consider new secure app integrations to safeguard such crucial processes as invoicing. For example, business owners in the construction sector should prioritize secure remodeling estimating app technology to ensure trust and streamline workflow.
2. Be Wise About Artificial Intelligence
A comprehensive cybersecurity approach requires both human expertise and AI integration.
AI-powered cybersecurity tools help IT teams:
- Detect issues even faster
- Monitor systems more efficiently
- Alert IT teams to potential issues
- Retrieve and interpret security data insights faster
- Improve productivity (creating room for more IT innovation)
However, on the flip side, IT teams must be mindful and ready to confront AI-driven cyberattacks from external sources. There’s also the growing internal threat of shadow AI use on company networks. Shadow AI refers to any AI-powered tools that aren’t approved by the company.
3. Optimize Data Governance Policies
The previous point of shadow AI speaks to the value of implementing strict data governance policies. Companies can strictly prohibit the use of any AI tools and devices not issued or approved by the company. Data governance also ensures that companies are compliant with the latest data privacy regulations.
Data management teams require stringent governance guidelines to protect sensitive data. Secure data classification practices ensure data is properly stored and labeled, providing a more comprehensive look for cybersecurity audits.
Classification makes it easier to assign risk scores to data categories. These scores help IT teams apply the required cybersecurity protections for each category.
Good data governance is supported by ongoing security training. Companies should mandate continuous training on the latest cybersecurity policies, including certification. Automated integrations can also alert IT teams when certifications are about to expire to avoid compliance issues.
4. Strengthen Data Privacy Through PET Integrations
The point on data governance is relevant to another hot topic in cybersecurity, privacy-enhancing technology, also known as PET. These secure applications are designed to safeguard data while making it accessible to approved users. PET technologies make data accessible without exposing sensitive information to the wrong parties.
For example, homomorphic encryption PET tools allow companies to analyze encrypted information without decrypting the data. End-to-end encryption is a widely accepted PET protocol that encrypts all communication avenues. Differential privacy is another valuable tool that allows companies to extract valuable insights from sensitive data without the risk of exposing consumer accounts.
Prioritize Resilient Cybersecurity In 2026
Are your systems, networks, and devices equipped with the latest integrations in cybersecurity? Take note of the above strategies as you audit and secure your company for a new age of digital security. Ensure your staff is trained and ready to face and prevent any security hurdles.
Build your knowledge base with the help of IP With Ease, your source for technology education, tutorials, expert Q&As, and the latest trends.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.