Table of Contents
GRE over IPsec and IPsec over GRE are the different ways of securing data packets within a tunnel. GRE is a tunneling protocol, and IPsec provides security through encryption and authentication. In GRE over IPsec, GRE tunnel is itself protected by IPsec, encrypting the entire encapsulated traffic. On the other hand, in IPsec over GRE only the payload is encrypted within the GRE tunnel, leaving the GRE header and routing protocols unencrypted.
What is GRE?
Generic Routing Encapsulation (GRE) is a Cisco developed tunneling protocol. It is a simple IP packet encapsulation protocol. Generic Routing Encapsulation is used when IP packets need to be transported from one network to another network, without being notified as IP packets by any intermediate routers.
GRE lets two end users to share data that they wouldn’t be able to share over the public network. It supports any OSI Layer 3 protocol. It utilizes Protocol 47. GRE tunnels support encapsulation for both unicast and multicast packets. GRE can carry IPv6 and multicast traffic between networks. However, GRE tunnels are not considered a secure protocol because it lacks encryption of Payloads.
What is IPsec?
IPSEC stands for Internet Protocol Security. It is an Internet Engineering Task Force (IETF) suite of protocols between two communication points across the Internet Protocol network that provide data authentication, data integrity, and confidentiality. IPsec is mostly used to set up VPNs, and works by encrypting IP packets, along with authenticating the source where the packets come from.
Related – GRE VS IPSEC
We have to establish an IPsec tunnel between two IPsec peers before we protect any IP packets. We use protocol called IKE (Internet Key Exchange) to establish an IPsec tunnel.
IKE consists of 2 phases in order to build an IPsec tunnel. They are:
- IKE Phase 1
- IKE Phase 2
IKE Phase 1
The major purpose of IKE phase 1 is to create a secure tunnel so that we it can be used for IKE phase 2. The following steps are done in IKE phase 1
- Negotiation
- DH Key exchange
- Authentication
IKE Phase 2
The IKE phase 2 is used to protect the user data. Quick mode is built in IKE phase 2 tunnel. In IKE phase 2 tunnel negotiation will be done on the following things.
- IPsec protocol
- Encapsulation mode
- Encryption
- Authentication
- Life time
- DH Exchange (Optional)
IKE construct the tunnels but it doesn’t authenticate or encrypt user data. For this we use two other protocols:
- AH (Authentication Header)
- ESP (Encapsulating Security Payload)
Both protocols AH and ESP supports authentication and integrity but ESP supports encryption also. Because of this reason, ESP is the most commonly used protocol nowadays.
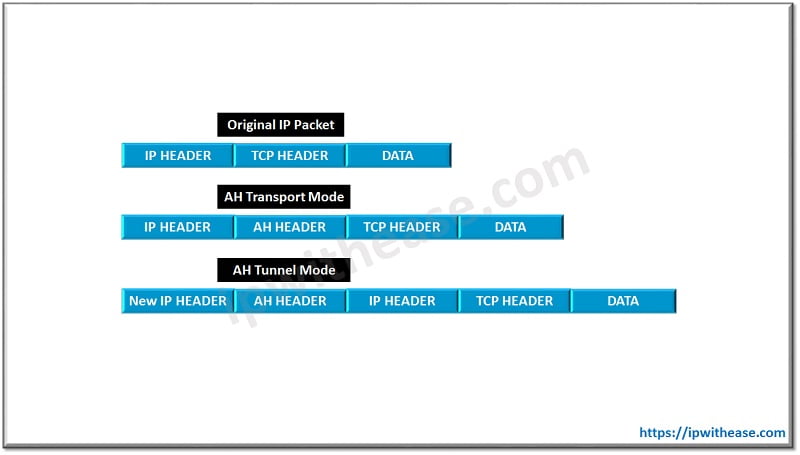
The above two protocols support two modes. They are
- Tunnel Mode
- Transport Mode
One of the main difference between the two modes is that original IP header is used in the Transport mode and new IP header is used in the Tunnel mode.
The whole process of IPsec is done in five steps. They are as follows
- Initiation
- IKE Phase 1
- IKE Phase 2
- Data Transfer
- Termination
Related – GRE vs L2TP
GRE over IPsec
As we know that GRE is an encapsulation protocol and it can’t encrypt the data, so we take the help of IPsec for getting the encryption job done. GRE over IPsec can be configured in two modes.
- GRE IPsec Tunnel Mode
- GRE IPsec Transport Mode
GRE IPsec Tunnel Mode
In GRE IPsec Tunnel Mode the entire GRE packet is encapsulated, encrypted and protected inside the IPsec packet. A significant overhead is added to the packet in the GRE IPsec tunnel mode because of which usable free space for our payload is decreased and may lead to more fragmentation when transmitting data over a GRE IPsec Tunnel.
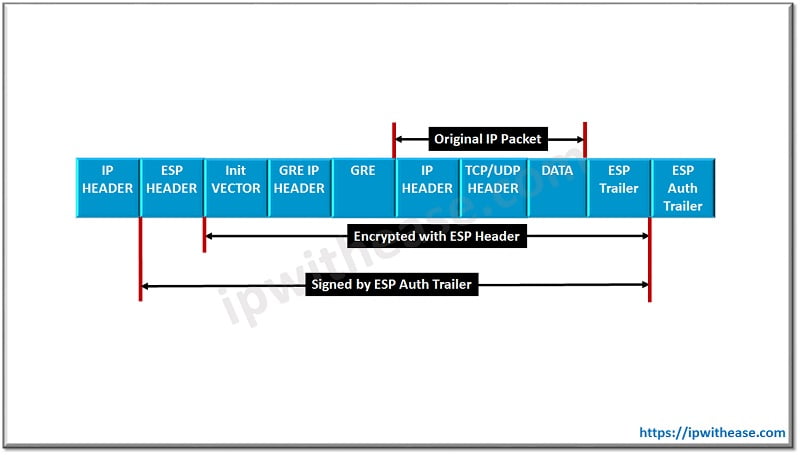
The above packet structure shows GRE over IPsec in tunnel mode.
GRE IPsec Transport Mode
In GRE IPsec transport mode, the GRE packet is encapsulated and encrypted inside the IPsec packet, but the GRE IP Header is placed at the front and it is not encrypted the same way as it is in Tunnel mode. Transport mode is not a default configuration and It must be configured using the following command under the IPsec transform set:
R1 (cfg-crypto-trans) # mode transportGRE IPsec transport mode is not possible to use if the crypto tunnel passes a device using Network Address Translation (NAT) or Port Address Translation (PAT). In that case, Tunnel mode is used. GRE IPsec transport mode cannot be used if the GRE tunnel endpoints and Crypto tunnel endpoints are different.
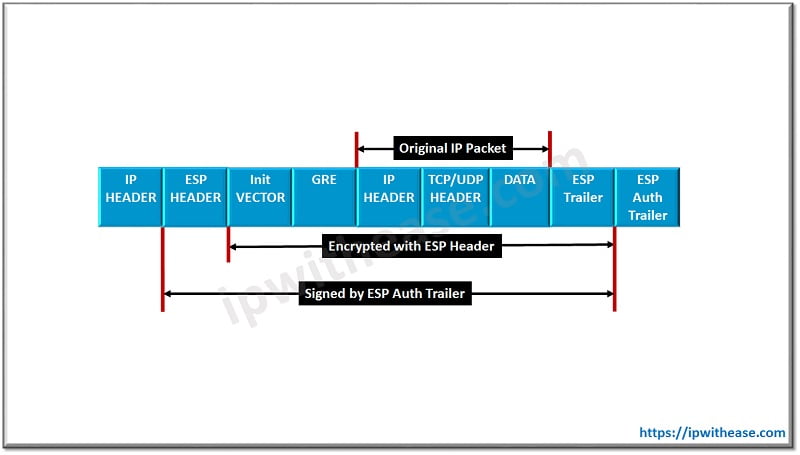
The above packet structure shows GRE over IPsec in transport mode.
IPsec Over GRE
In IPsec over GRE the packets that have been encapsulated using IPSec are encapsulated by GRE. In IPsec over GRE IPsec encryption is done on tunnel interfaces. The end user systems detects data flows which need to be encrypted on tunnel interfaces. An ACL is set to match data flows between two user network segments. Packets which are matched with the ACL are encapsulated into IPSec packets and then into GRE packets before they are sent over the tunnel. Packets which are not matching with the ACL are directly sent over the GRE tunnel without IPsec encapsulating. IPsec over GRE removes the additional overhead of encrypting the GRE header.
Comparison: GRE over IPsec vs IPsec over GRE
| GRE OVER IPSec | IPSec OVER GRE |
|---|---|
| Additional overhead is added to packets by encrypting the GRE Header | Removes the additional overhead of encrypting the GRE header. |
| IP multicast and non-IP protocols are supported | IP multicast and non-IP protocols are not supported |
| Supports dynamic IGP routing protocols over the VPN tunnel | Does not support dynamic IGP routing protocols over the VPN tunnel |
| All primary and backup point-to-point GRE over IPSec tunnels are pre-established, so that in the event failure scenario a new tunnel need not to be established. | No backup point to point tunnels are established to overcome the event failure scenario. |
Download the difference table GRE over IPsec vs IPsec over GRE
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj