Table of Contents
Network security plays a crucial role in securing the digital workspace of organizations. Zero trust network architectures, network access control, VPN etc. are solutions geared towards protection of an organization network and its assets. They sound similar as the purpose is the same to protect the network but having different sets of capabilities.
In today’s article we understand the difference between ZTNA (Zero trust network architecture) and NAC (Network access control) i.e. ZTNA vs NAC, their key characterizes, how both work and use cases.
What is ZTNA
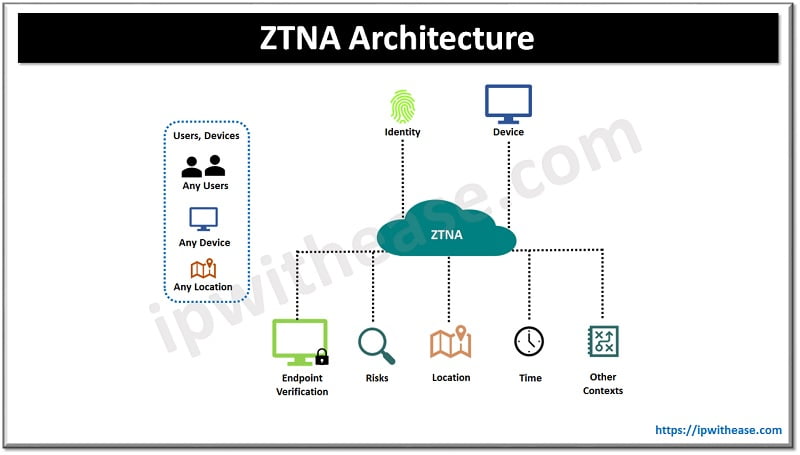
Zero trust network architecture of ZTNA is a modern approach towards network security; it relies on a basic principle ‘Never trust always verify’ approach. ZTNA model, sometimes referred as framework controls access to applications and assets, resources considering they are accessible from anywhere. The zero-trust approach relies on a trust principle where the user or device is granted specific access as per the need. ZTNA operates on explicit authorization.
ZTNA is built on three core principles as under:
- Identity Centric – It is designed around user identity and not the IP address and requires authentication before being granting access to network.
- Zero Trust – It works on principle of least privileges using micro-segmentation and makes unauthorized resources invisible.
- Cloud Centric – It is designed to operate on cloud and provide security which key characteristic is scalability.
Limitations of ZTNA
- Complexity in implementation
- Potential for latency issues
- Challenges to maintain user and device information accurately
- Integration with legacy systems is challenging as not all assets are designed to operate with ZTNA system
- Risk of data exfiltration due to lack of complete visibility or control over data
- Accurate assessment of user context and device posture can be tough
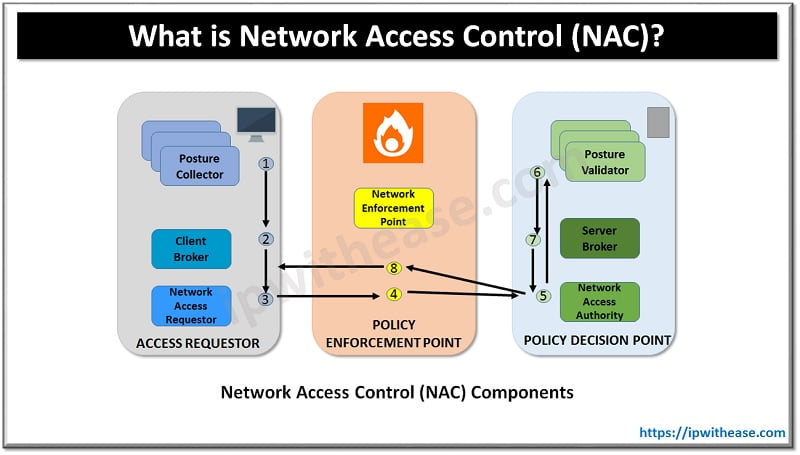
What is NAC
Network access control or NAC is quite similar to VPN and provides a solution when most of the people are in office. They restrict access to endpoint systems based on organization policies and perform authentication and authorization before access grant. But NAC has limitations like it can’t do segmentation and is meant to protect on premises devices only. Once access is granted to the user the NAC role is negligible. NAC can’t provide fine-grained least privilege access and rely on existing network segmentation or VLANs.
Limitations of NAC
- Can’t provide fine-grained least privilege access and rely on existing network segmentation
- Limited ability in making access decisions based on user context
- Secure and private, encrypted communication channel is not provided between services and clients
- Scalability and management is complex as more devices are added into the network
- Do not support cloud security
ZTNA vs NAC
Lets explore the differences between the two:
Network Segmentation
- ZTNA provides network segmentation with software defined security perimeter on every part of the corporate network and prevents lateral movement within the network.
- NAC does not support segmentation and hence it relies on existing segmentation available on the network (layer 2 and layer 3 VLANs). All users and devices lying on the same network segments will have the same access privileges and rights.
Enforcement Point
- ZTNA operates at layer 4 and above of the OSI model and provides higher granularity in terms of per user and per device access based on contextual elements. Applications are treated separately from the network.
- NAC operates at lower layers of OSI model – layer 2 and layer 3 so NAC can identify and authenticate device or user and grant them some level of access at network layer 2 and 3 which is VLAN and subnets.
Authorization
- Provides explicit authorization as based on ‘Never trust always verify’ philosophy.
- Provides implicit authorization as based on ‘trust but verify’ philosophy
Service Based
- ZTNA is purely meant for the cloud and does not require an endpoint agent . its cloud-centric nature lets it implement fine-grained least privileges access. It is also suitable for BYOD (Bring your own device) devices protection.
- NAC is agent-based technology that requires installation of agents on all devices in the network. NAC protects devices only on existing network segmentation or VLANs and is not viable for cloud-based networks where devices and firewall rules constantly change.
Comparison Table: ZTNA vs NAC
Below table summarizes the difference between the two:
| Feature | ZTNA (Zero Trust Network Access) | NAC (Network Access Control) |
| Security Model | Zero Trust (Never Trust, Always Verify) | Perimeter-based (Trust but Verify) |
| Access Approach | Least privilege access to applications | Device-based access to the network |
| Scope | User and application-centric | Network-centric |
| Access Control | Based on identity, device posture, and context | Based on device authentication and policies |
| Deployment Model | Cloud-first, remote-friendly | On-premises, LAN/WAN-based |
| Visibility | Focused on users and applications | Focused on devices and endpoints |
| Protection Against | Insider threats, lateral movement, remote access risks | Unauthorized network access, rogue devices |
| Authentication | Continuous verification (multi-factor authentication, device compliance) | Typically, one-time authentication at entry |
| Access Mechanism | Secure tunnels to applications (without exposing the network) | Full network access once authenticated |
| User Experience | Seamless, remote-friendly | Can be intrusive, requiring agent installation |
| Threat Mitigation | Prevents lateral movement and over-permissioned access | Controls which devices can connect but may not limit internal movement |
| Best For | Remote and hybrid workforces, cloud environments | Enterprise networks, corporate offices |
| Challenges | Requires integration with identity and security solutions | Difficult to scale for remote work, complex setup |
| Examples | Zscaler ZTNA, Netskope, Palo Alto Prisma | Cisco ISE, Aruba ClearPass, Fortinet NAC |
Download the Comparison Table: ZTNA vs NAC
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj