Table of Contents
We can’t imagine businesses running without and IT network infrastructure in modern times. The ability to collect, distribute and analyze information quickly as much as possible is only viable with a robust Network infrastructure in place.
Network management and its security controls are important to ensure security policy is implemented, compliance requirements are met and management of access control in networks can be performed. It is essential to ensure devices attached to a network are secure.
Primary goal of Network Access control (NAC) systems is to defend perimeter of organization network inclusive of both in house physical infrastructure and any cloud-based systems which are integrated together.
Today we will learn more in detail about what is network access control, why it is used, its components and so on.
Network Access Control (NAC)
Network Access control (NAC) is a network solution which allows only authenticated, compliant endpoint devices can access the resources of network and infrastructure. The devices which are connected to the said network its activities are monitored and controlled in Network Access control (NAC). With Network Access control (NAC) systems the security of organizations can be improved by enforcing devices complying with organization security policy can only be connected to network, restrict data that users can access and apply anti-threat applications such as firewalls, Antivirus software, etc.
Network endpoints impose threats and enormous enterprise resources are wasted in combating increasing threats related to virus, worms, and spyware. Increase in proliferation of devices which require network connectivity such as mobiles, tablets, laptops, PDAs etc.
Network access control (NAC) simply identify who you are? Should determine what you can access?
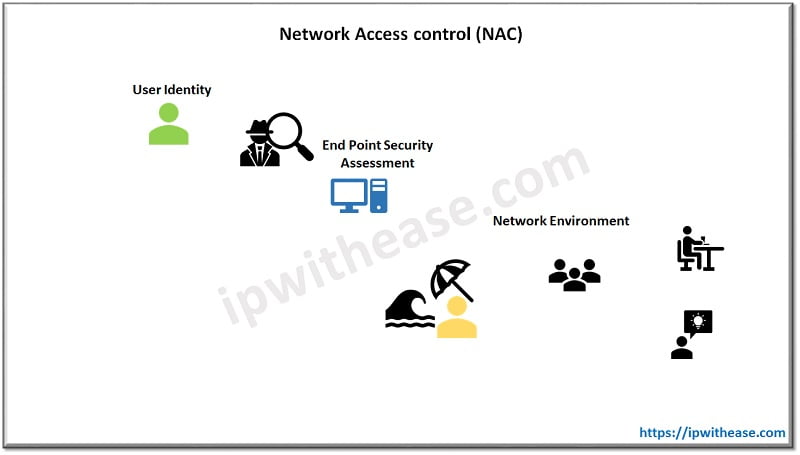
A typical network access control (NAC) comprises of two major elements namely Restricted access and Network boundary protection.
Restricted Access
It is focused towards user authentication and authorization controls responsible for authentication and identification of users. The Network Access control (NAC) is responsible for storing organization access policies which are applied to every submitted request. This done via a two-step process – authentication and authorization , if either of them fails the access request is not processed and blocked to ensure safety of network this is also known as ‘zero trust security’. While doing authentication user supplies its credentials to verify its identity using username/password or a biometric authentication like voice or finger recognition which is verified against local access policies configured in the network to allow / disallow access.
Network boundary protection
It refers to perimeter protection or perimeter Defense. These are tools and techniques which are used to manage, control, and protect the information which is stored, processed, and transmitted inside / outside network boundaries. Firewalls provide network boundary protection by segregating public Internet and private Internet which can function at multiple layers of network. Intrusion detection and Intrusion prevention systems detect / fix /prevent network anomalies and can detect the attacks so that preventive actions can be taken before systems get compromised. Firewalls, Antivirus software, controller interfaces, Intrusion detection and Intrusion prevention systems are all Network boundary protection tools.
Steps to Implement – Network Access Control (NAC)
The implementation of Network Access control (NAC) is to be planned depending on the topology of organization network. The main steps in solution deployment involves below stages:
- Gather data – the first hand information about endpoints in the network is to be collected. This should include every device, server, piece of equipment which interfaces with digital resources.
- Identity management – Management of user identities within the organization approach to determine authentication and authorization requirements.
- Apply permissions – every user be it employee, vendor, partner it needs to be integrated with Network access control (NAC) system so that its access level and activity can be tracked.
- Update as required – Permissions policies may require update from time to time and it needs to be implemented as controls for Network access control (NAC) system.
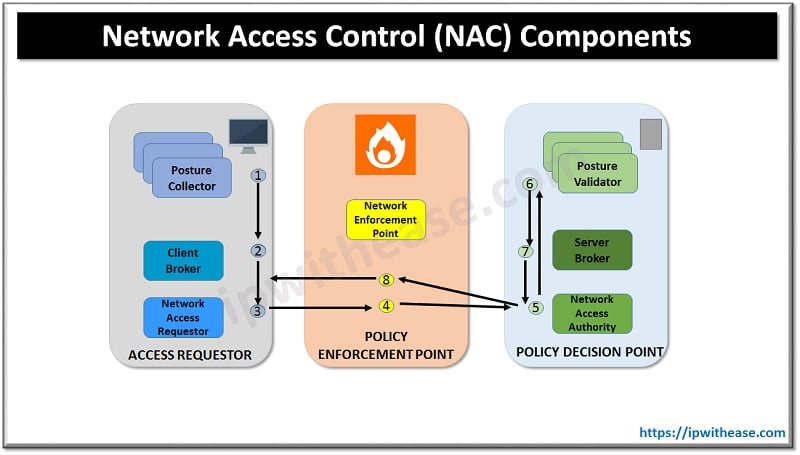
How Network Access Control (NAC) works?
- Access requestors could be Laptops , PDAs, VoIP phones, Desktops Printers etc.
- Posture Collector collects security status information of the end point
- Client broker consolidates endpoint data from posture collector and sends it to Network access requestor
- The Policy enforcement point receives the authentication and security assessment data and sends it to policy decision point.
- The network access authority receives data from access requestor , user authenticity is validated with authentication database to verify credentials
- Posture collector checks the information from corresponding collector and decision is communicated to server broker
- The server broker consolidates posture validator input into single policy answer
- The network access authority sends the corresponding answer and instructions to policy collector
Continue Reading:
Microsegmentation vs Zero trust
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj