Table of Contents
Introduction
Cyber attacks are becoming increasingly common (as well as sophisticated), and businesses need to tighten their defenses from data exfiltration or financial harm. To implement the safeguard system, a Security Operations Analyst helps organizations identify their vulnerabilities, monitor their threats, and respond to security incidents in real-time.
But how do Security Operations Analysts detect and stop cyber attacks? What tools and tactics do they employ? This guide will look into what their key responsibilities are and how they help businesses remain secure in an increasingly digital world.
The Role of a Security Operations Analyst
The role of a Security Operations Analyst (SOC Analyst) includes:
- Monitoring IT networks and systems for suspicious activities such as hacking attempts and unauthorized access
- Analyzing security threats and responding to incidents promptly
- Investigating vulnerabilities and mitigating risks
- Implementing cybersecurity best practices to prevent future attacks
They are the backbone of the IT department, providing private security that protects companies from cyber threats while ensuring compliance with industry regulations.
Real-Time Monitoring-Based Cyber Threat Detection
Cybercriminals employ various methods, including phishing, ransomware, and malware, to take advantage of vulnerabilities in a company’s security system. Security Operations Analysts use real-time monitoring tools to catch suspicious behavior before it becomes an all-out attack.
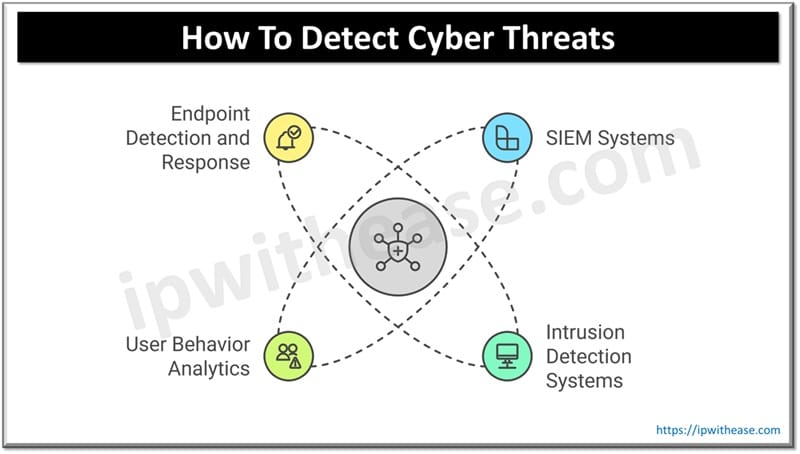
How They Detect Threats
✔ SIEM (Security Information and Event Management) Systems — Combine and review security logs from various sources.
✔ Intrusion detection systems (IDS) – Monitoring for any threat activity on your network.
✔ User Behavior Analytics (UBA) – Identify suspicious login attempts or access.
✔ True Endpoint Detection and Response(EDR)– Puts you on alert about suspicious actions on computers and mobile devices.
With these tools, Security Operations Analysts can detect anomalies and respond quickly enough to prevent security breaches.
Forensics and Analysis of Security Events
Upon detection of a possible threat, the Security Operations Analyst executes an investigation to find out the source of the attack, the type of malware or exploit used, the extent of the damage or data compromise, and how to contain and eliminate the threat
Some Common Cyber Attacks That They Analyze
- Phishing Attacks – Make fake emails to try to trick employees and use other fake passwords.
- Ransomware — Malicious software that encrypts files and requests payment.
- DDoS Attacks – Flood a site with traffic until it becomes unusable.
- Insider Threats – Data is leaked by employees or contractors either intentionally or accidentally.
SOC Analysts review security incidents to discover patterns and enhance defense systems to prevent attacks in the future.
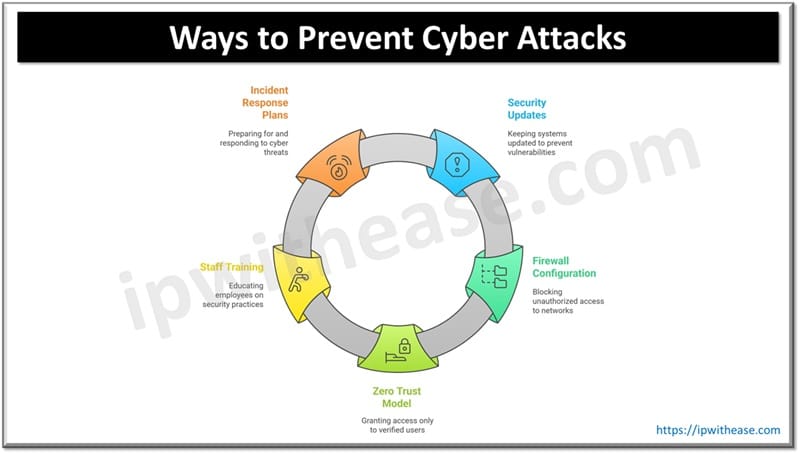
Ways to Prevent Cyber Attacks
To avoid problems, cybersecurity experts stress prevention. All Security Operations Analysts do not merely respond to threats; they implement security protocols to prevent cyberattacks from occurring.
Key Prevention Strategies:
- Regular Security Updates & Patch Management – Keeping everything updated.
- Firewall & Network Security Configuration – Denying unverified entries.
- Zero Trust Security Model – Granting access only to verified end-users.
- Staff Training & Phishing Awareness – Teaching employees about security.
- Incident Response Plans – Ensure you are prepared enough before a cyber threat affects your business.
This ensures that businesses have the tools in place to avoid experiencing any potential breaches.
Managing Security Breaches in a Timely & Efficient Manner
Cyber attacks can occur despite taking all precautions. Security Operations Analysts are indispensable in incident response and recovery by doing:
- Determining the extent of the breach – What systems and data were impacted?
- Containing the threat — Isolating compromised devices to contain the fallout.
- Removing malware or security threats – Cleanup, Restoring affected systems — safely resuming business operations
- Post-incident review — Analysing the breach so it never happens again
Quickly responding to security incidents allows businesses to decrease downtime, limit financial loss, and keep customer data safe.
Employing AI & Automation for Enhanced Threat Detection
Cybercriminals are becoming smarter, and so are Security Operations Analysts. They use AI-powered cybersecurity tools to help detect and respond to threats faster than ever.
How Is AI Improving Cybersecurity?
✔ Threat Intelligence Platforms – Using AI to Predict and Detect Potential Cyber Threats.
✔ Automated Response System — Automatically contain and mitigate security threats in minutes.
✔ Machine Learning Algorithms – Spot suspicious patterns and avoid fraud.
✔ Dark Web Monitoring – Spot leaked credentials before those credentials can be used against you.
They can also work synergistically to transform the security posture to be more adaptive to stay ahead of cybercriminals and improve the overall effectiveness of security.
Cyber Security Compliance & Risk Management
Businesses must comply with data protection laws to prevent potential legal actions and fines. Security Operations Analyst is in compliance with:
- GDPR (General Data Protection Regulation) — Safeguard user information across Europe.
- HIPAA (Health Insurance Portability and Accountability Act) – Protects healthcare data.
- ISO 27001 — Global cybersecurity standards for data security
- PCI DSS (Payment Card Industry Data Security Standard) – Protects Online Transactions
This helps businesses to mitigate legal risks and build trust with their customers.
Every Business Should Have a Security Operations Analyst
Cyber threats are changing, and businesses, big and small, are always in danger. Without Security Operations Analysts, organizations are left to contend with:
- Data breaches — Leakage of sensitive consumer and financial data.
- Financial Losses – Cyber attacks can cost businesses millions of dollars per year.
- Reputational Damage – Customers never trust companies with bad security.
- Regulatory Fines – Violation of the security laws results in fines.
A Security Operations Analyst can provide round-the-clock monitoring, rapid detection of threats, and proactive measures to keep a business safe and secure.
Final Thoughts
Cybersecurity is no longer an option, but rather a necessity. Working in the field of Security Operations Analysts, you provide organizations with strong cyber threat detection, analysis, prevention, and response to help defend against attacks.
Key Takeaways:
- SOC Analysts are responsible for monitoring IT systems to detect cyber threats.
- They investigate security incidents and prevent breaches.
- Proactive security measures help to reduce vulnerabilities.
- Following the regulations keeps things legal and your data secure.
No matter whether big or small, every business should have a cybersecurity army. This is why you should invest in Security Operations Analysts to protect your data, brand, and business continuity.
Are you making sure your business is secure from cyber threats? Begin the process of constructing a robust security system.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.