Table of Contents
In a modern distributed ecosystem, simply trusting traffic inside a network perimeter is no longer sufficient. Developers and architects now must treat every request, whether from a user, another service, or an internal system, as potentially hostile. Many teams exploring modern api security adopt zero trust principles early, but successfully applying those principles to microservices and APIs requires careful design and layered enforcement.
Below is a guide to evolving your API architecture under zero trust, with practical patterns, pitfalls, and implementation advice applicable to real-world microservices environments.
Why Zero Trust Matters in Microservices
Traditional security models assumed that once inside the network boundary, a system was implicitly trusted. But microservices break that model apart: services talk to each other across internal networks, often across hybrid or multi-cloud environments. Trusting internal traffic blindly exposes your system to lateral attacks.
NIST’s SP 800-207 describes zero trust as shifting from perimeter security to identity- and policy-based controls: access is never implicit, and every interaction is authenticated and authorized. In microservices, this means enforcing trust at the service-to-service level, regardless of network location.
With zero trust, your APIs and microservices become more resilient to breaches: a compromise in one component does not open the floodgates to your entire system.
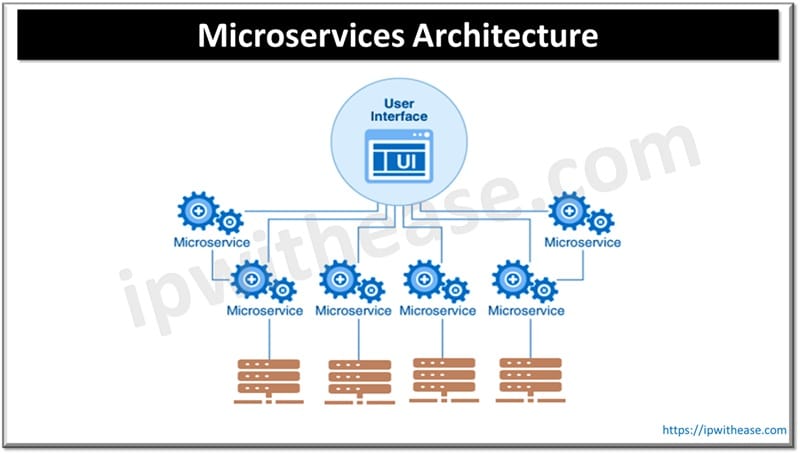
Core Principles for Zero Trust in API / Microservices
When adapting zero trust to microservices, keep these core principles in mind:
1. Never Trust, Always Verify
Every request, even internal ones, must present valid identity credentials. Use tokens (e.g. JWTs), mutual TLS (mTLS), or signed credentials to validate both client and server identities.
2. Least Privilege Access
Services should only be allowed the minimum permissions needed to perform their function. Fine-grained access policies restrict escalation or misuse of endpoints.
3. Dynamic, Contextual Authorization
Decisions should not be binary but context-aware: consider identity, device health, time, or request metadata. For example, an internal service calling a payment API from an unknown host might be treated with more caution.
4. Microsegmentation / Zero Trust Zones
Partition services into zones or segments, such that a breach in one zone cannot freely traverse to others. Enforce policies at service mesh proxies or gateways to control traffic flows.
5. Continuous Monitoring & Auditing
Log, monitor, and inspect every API call. Unusual patterns or deviations should trigger alerts or additional scrutiny. Audit trails are a fundamental requirement for trustworthiness.
The OWASP Zero Trust Architecture cheat sheet provides a useful checklist and phased approach for implementing these controls.
Design Patterns & Implementation Techniques

Below are patterns and strategies that help enforce zero trust in a microservices-based API architecture:
API Gateway as Policy Enforcer
Front all outbound and inbound traffic through an API gateway. It can centralize authentication, authorization, rate limiting, and enrichment of context. Ensure it verifies identity before forwarding requests.
Nordic APIs recommends combining strict authentication, authorization, logging, and rate limits at the gateway to prevent abuse.
Sidecar Proxies / Service Mesh
Deploy sidecar proxies (e.g. Envoy, Istio) alongside each microservice. These proxies mediate all service-to-service traffic, enforcing mTLS, policy checks, and telemetry without requiring each service to reimplement security logic.
Token Forwarding and Propagation
When a user-level JWT is accepted by one service, that service can forward the token, or mint short-lived scoped tokens, to downstream services. The forwarded token must be validated at each hop. Avoid blind trust of upstream headers.
Attribute-Based Access Control (ABAC)
Control access using attributes (e.g. “role = billing_service”, “environment = production”) rather than static roles. Many modern zero trust frameworks (including upcoming NIST SP 800-204) emphasize attribute-based controls for microservices contexts.
Secret Management & Credential Rotation
Use a centralized secrets manager (e.g., HashiCorp Vault, AWS Secrets Manager) to issue credentials dynamically. Rotate keys and revoke them quickly. Never bake secrets into images or source code.
Defense in Depth
Layer your security: the API gateway, sidecar proxy, application logic, data encryption, and individual policy checks should all reinforce each other. If one layer is bypassed, others must still protect critical resources.
Scaling Zero Trust Over Time
Introducing zero trust to a mature monolith is daunting; it’s more manageable to phase it in incrementally. Consider:
- Start with external APIs: Apply zero trust first to externally-facing endpoints.
- Move to internal services: Gradually expand policy enforcement deeper into internal dependencies.
- Adopt observability early: Telemetry and monitoring should already be in place before strict enforcement.
- Test failure scenarios: Ensure fallback modes don’t open backdoors.
- Use advisory mode: Run policy enforcement in monitor-only mode initially to identify friction points.
Organizations that build zero trust incrementally reduce risk and avoid breaking production.
Common Challenges & Mitigations
- Performance Overhead: mTLS, token validation, and proxy checks add latency. Mitigate by caching, hardware acceleration, and efficient crypto algorithms.
- Legacy / Third-Party Services: Some components may not support modern identity methods. Use API adapters or sidecar wrappers to bridge the gap.
- Policy Explosion: Fine-grained policies can become unmanageable. Use policy templating, inheritance, and policy-as-code tools (e.g. OPA).
- Identity Management Complexity: Managing identities for both users and services is non-trivial. Use robust identity providers (IDPs) and automation.
- Cultural and Organizational Buy-in: Engineers may resist stricter checks. Emphasize the security and resilience benefits, not just compliance.
Why Zero Trust Pays Off
If implemented correctly, zero trust in microservices architecture brings significant advantages:
- Reduced blast radius: A compromised component doesn’t necessarily expose the entire system.
- Stronger compliance posture: Many regulations require granular access control and auditing.
- Resilience in hybrid / multi-cloud environments: Because policies don’t rely on network location, you can scale outwards securely.
- Operational confidence: Observability, consistent identity management, and policy-driven controls reduce firefighting.
Zero trust isn’t optional – it’s foundational for scaling secure microservices.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.