Google ADs
 ANSWERS @https://ipwithease.com/shop/
ANSWERS @https://ipwithease.com/shop/
- What are the main modes (in terms of network design) in which a SRX firewall can be integrated into a network? Explain briefly.
- You are working as a network architect for your enterprise. Recently you have noticing an increased number of threats from particular network segments, and just to provide sufficient security you have decided to add SRX firewalls into the existing network. One of the main challenges in integration of SRX into existing network. And your CTO has strictly not allowed to change any existing IP addressing and routing infrastructure. How can you proceed with such a challenge?
- How many type of interface modes exist in transparent mode of SRX?
- As a network Security Engineer you have worked on many legacy stateful traditional firewalls. On many occasions you heard incidents where traffic is being blocked by firewalls due to asymmetric routing flow. Can you explain what is exactly asymmetric routing?
- What is the default mode of SRX interfaces if it is configured in Transparent Mode?
- You have design your network for SRX in multiple locations for securing your LAN networks. As per requirement, you had to deploy the SRX in Transport mode, and we know there are no layer 3 interfaces in SRX. Now you have a challenge to make SRX communicate with other devices in network for management and reporting purpose on IP connectivity. How can you overcome this challenge?
- In Transport mode design, SRX firewall behaves just likes any layer 2 switch. This capability is good in terms of deploying SRX where we are not supposed to make extending design changes, however adding a new layer 2 device can have potential issues in network and SRX must be responsible to keep the traffic flow always. What is the most common issues you can run into in such cases?
- In routed mode, SRX is supposed to check and route the network traffic to its proper destination. However, in order to make things simpler and faster for processing, how does SRX perform this?
- You have been troubleshooting a network issue in which you suspect routing loop in the network and traffic is being black holed. You are going from each hop to check the destination for the impacted network. Once on SRX how can you test that SRX is not black holing any traffic and all routing on SRX is working fine?
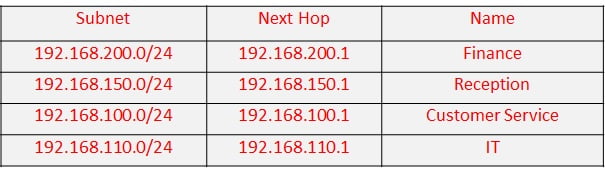
- You are working on a large enterprise, and receive an urgent request to add new routes into the SRX for reaching new LAN subnets. Since this is an urgent requirement, you do not have time to design routing protocol and route policy for it. What is the quickest way to do it?

- You are assigned to design a new network including security appliances as SRX. On routing design, you are not sure which type of routing you must use, however you must know from the design requirements that what type of routing is needed in which design scenarios. Briefly explain what are the routing types and their design considerations?
- SRX is a powerful firewall, equipped with all latest features in network security domain. However, it is also a very strong layer 3 routing device. As a layer 3 device, it supports all major types of routing protocols of IEEE standard. Briefly explain these different types of routing protocols supported by SRX?
- In any network, we always need to propagate and manipulate different routes. In order to do that we need a strong feature to do it easily on any layer 3 device. In Junos what kind of feature is available to manipulate routing, route propagation, redistribution and advertisements?
- As a network security engineer, you must understand the growing demand and capability of enhanced security features. Juniper has very good solution to extend the network security and that feature is called SDSN. What are the main components of Juniper Software Define Secure Network solution?
- Every routing policy main basic unit is “TERM” and term has multiple basic elements configureable which defines the complete routing policy and its purpose. Can you name those elements and their functions?
- Your network has Internet Edge connectivity with ISP, and to secure your network from any threats and attacks from internet you have placed the SRX firewall inline with ISP. In order to do that you are required to have BGP peering with ISP. Now that you have setup BGP peering, which troubleshooting command will confirm if the routes being received from uplink YOU’RE YOUR uplink peering IP of ISP is 58.27.2.1?
- In Juniper SRX, you have very complex and old design, where both static routing as well as dynamic routing is in use. In dynamic routing you have RIP and OSPF for specific networks. As network security engineer, you must know which routes are preferred over which ones in such cases, so that you can easily decide in future to use what kind of routing for the requirement. Briefly explain these route types’ preferences?
- You have layer 3 device like Juniper SRX, and you want to keep the routing tables of different networks totally separate so that they have no overlapping or conflict at all. Such a challenge can be achieved by using which feature in JUNOS routing platforms?
- As a network security designer, you must know that chassis redundancy is one of the key components in any network design. Similarly, in firewall design and deployment a single chassis firewall is not a reliable solution to provide in any network. Juniper offers “High Availability” feature in terms of chassis redundancy. Can you name the exact term used by Juniper in such designs?
- As an implementation engineer, you are given a task to deploy an SRX chassis cluster between 2 SRX appliances. As an expert security engineer you must know the type links you must connect in order to make cluster up and running. Briefly explain what type of links are required in SRX HA cluster.
- In High Availability cluster configurations, name the two parameters or IDs which are must to mention, for the cluster to work properly?
- You have specific requirements from your company’s CTO and that is to make sure you split half of the company’s departments to use SRX NODE 0 as their gateway and other half to use SRX NODE 1 as their gateway. You know already that how to setup a HA Cluster of SRX pair, and already done that. Now explain how will your load share these departments as per your CTO request?
- Under which configuration stanza you can apply screen-options in Junos SRX platforms?
- As a network operations engineer, you must know how the chassis cluster ensures redundancy on physical interface level. You have setup successfully the chassis cluster and interfaces are also configured. What feature is needed to ensure that these interfaces connected on SRX firewall will provide redundancy in case of any node i.e. SRX failure?
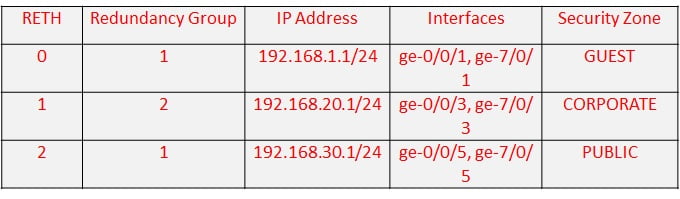
- What are the main steps of configuring the RETH interfaces and making sure that they are properly redundant? Mention all main steps?
- What are the main advantages of Juniper SDSN solution?
- Which redundancy-group number cannot be used and why?
- You are newly employed Network Implementation Engineer and below is the list of parameters given to you to deploy a chassis cluster. Now you are supposed to make full configurations for these requirements. Total Reth count = 3

- As network security operations engineer, your role is always to verify the status of network devices. In case of SRX cluster, if you receive any complaint, and you are suspecting an issue with chassis cluster or its failure to switchover to backup; what basic troubleshooting commands you must check first to ensure that everything is working fine on chassis cluster?
- You have fresh SRX and you wish to make it part of a cluster with cluster ID 1 and make this node as Node 0. Using single command how can it be done?
- You are using SRX firewalls in cluster, and need to ensure that during a failure of particular RE from one firewall, the traffic must not be interrupted and dynamic routing should have all active routes available. How can you achieve such a capability?
- You have to connect multiple braches between your offices using SRX, and for that you will use IPSEC site-to-site vpn. What options you can use to secure the key exchange between the multiple sites?
- You have been using UTM i.e. Universal Threat Management feature of SRX firewalls, to mitigate and handle the threats and attacks UTM acts on many fronts. In case a harmful packet is received then briefly explain what actions can UTM perform?
- You can run SRX in different modes for IPS/IDS deployment, but in high end series you most likely go for inline tap mode or dedicated mode. Can you explain the basic difference between inline tap mode and dedicated mode of IPS/IDS deployment on SRX?
- SRX one of the main unique selling points is that it offers UTM solution i.e. a complete Threat management system where you have bundle of features. Can you point out some of the main features of Unified Thereat management umbrella?
- In what situations you would require NAT PROXY ARP to be configured as a must?
- You are designing new security network for your enterprise. For that you have decided to use SRX chassis clusters in different sites to protect the enterprise resources in local area networks. Before deploying chassis clusters, you came across other requirements to ensure that Ethernet links must also be secured. What industry standard technology would accomplish that?
- You are working on a new project where you need to integrate the SRX in lined with an existing network. The SRX is supposed to be integrated between LAN and Internet Gateway. To keep things simple, you need to deploy this in such a way that incoming traffic from LAN interface is forwarded directly to WAN interfaces i.e. Internet Gateway. Without using Transport mode or routed mode, how can you achieve this challenge?
- Briefly explain all the steps which you must take in order to successfully make a secure wire between two SRX interfaces?
- You are given below task to configured SRX and make its two interfaces to be part of secure-wire. Below are the details of this task. Make the proper configurations for it?

- SRX is a next generation firewall, with IPS capabilities, briefly explain the difference between IPS and IDS and why we must need IPS in our network security solutions.
- As per your corporation’s new security policy, you have to deploy IPS on all firewalls immediately. What are the main steps to deploy IPS feature in SRX?
- How can you describe in very short way the main difference between ESP and AH?
- You are working in a Security Operations Center i.e. SOC and one of the main firewall is SRX. You suspect some incident, and wish to see the IPS/IDS status of the firewall, which troubleshooting commands will do that?
- What are the main modes of IPS/IDS deployment in SRX series and where these modes fit in?
- Juniper has always been ahead in delivering latest technology as per market demand. Juniper has solution called SDSN, which is composed of many components to provide various features in network security and management? Can you brief about this solution?
- You are working as network security engineer and your company main HR policy has demanded to cut down the social media usage for the employees, they however want to block some of the websites and rest of the internet access must be available. Which SRX firewall feature can easily accomplish this task?
- You are working on enterprise network security section of your company. And you have been always very proactive in updating the IPS attack database. What exactly will happen if the new attack database does not contain the entry that was already in use on SRX?
- You are working on your SRX and wish to see all sort of statistics as well as data related to AppTrack. Which most common command will you run to get as much data as possible?
- To manage permissions for access to resources in your network, you have decided to use Active Directory. In order to run it successfully, you must understand first what are the key parameters? Kindly elaborate
- Data Integrity is main feature we need in terms of VPN usage i.e. IPSec VPNs. Name the protocols which ensures data integrity?
- Using SRX security feature UTM, you wish to achieve content filtering. Name few of the common types of content filtering?
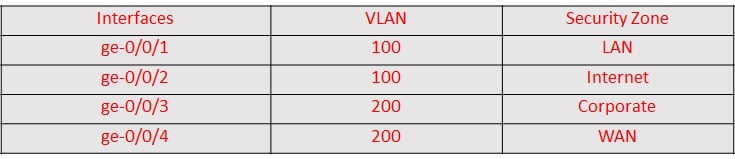
- You are running SRX in mixed mode, with layer 2 and layer 3 interfaces. There is a requirement to configure one security zone named “CORP” which belongs to executives, part of one layer 2 interface and one layer 3 interface. This needs to be accomplished urgently, what will happen when you configure and commit it?
- What is the default IPS deployment mode of SRX?
- You are using Junos Security director for many features but mainly logging and reporting. You must know the different types of supported browsers it can run smoothly so that there is absolutely no glitch or time outs. Can you name all those supported web browsers Junos is 100% compatible with?
- You have just deployed a firewall filter allowing all traffic except few TCP ports from internet ingress interface. As a network engineer you must know that the firewall filter is processed from top term to last. Explain what is by default the last rule set by JUNOS at the end of any firewall filter?
- As a network engineer you are assigned with a very important task to rate limit all the incoming web traffic from http and https to 100 Mbps. Configurations for this task should be combination of Policer and Firewall Filter. Interface connected towards internet is ge-0/0/0/1.
- Your manager has recently audited the network security and found that many corporate and guest users are able to telnet to the SRX devices. In order to harden the network security, you are supposed to give management access of telnet and ssh to only selected network i.e. network team (Subnet = 10.1.1.1/28). Make the necessary configurations to accomplish this task.
- What type of zones exist in Junos SRX and briefly explain all of them?
- You want to see which traffic is allowed to go to Junos platform itself. It is not meant to transit the Junos device. Example of such traffic can be telnet to junos SRX, or SNMP messages to see the overall platform health or to transfer some file into the directory of SRX etc. What kind of traffic is called while working on Junos Platforms?
- You are using site to site IPsec VPN between two branches, what are the two modes you may choose from in IKE Phase 1?
- You have huge daily tasks of adding and modifying security policies in SRX devices. One of the most important thing you must understand is how to re order the security policy, as policy is inspected from top to bottom. Which command can do it?
- In normal circumstances, you should not allow ping between different zones, however there is an issue and you need to allow ping traffic between your zone GUEST and CORP. Make a policy to do so?
- You have configured a NAT to access some services across the SRX network, otherwise through normal routing table are not accessible. There is still some issue and you need to ensure that all the checks are done, can you brief about which checks you must perform?
- You have a special server which requires access to its dedicated special port, to use it frequently it is good practice to make a custom application. How can you make it for TCP PORT number 8900?
- Your enterprise has a new policy to allow internet for its employees only on weekdays from 9:00 AM till 5:00 PM. You also need to log and check the stats of this policy. You are now supposed to implement this policy on your firewalls, make a quick configuration for this policy?
- You have one global policy for internet access in you network. There is always a threat from internet for DOS attack, so you need to make sure to see session logs for analysis later about the destination of attack or source. How can you achieve this in your policy?
- You have three main security zones and wish to track those for logging and reporting purposes. Make sure you have such tracking capability configured on zones. Mention the set of commands to achieve this?
- SRX firewall is one of the important elements of network, and mostly are exposed to internet. You need to always proactive is seeing if anyone making attempts to gain the access of SRX. Which command can be used to view it?
- In a large enterprise, you always have many users allowed to log into network devices. There are implementation, integration and operations teams. In order to appropriately design the access and authorization process, which common external authentication methods can be used?
- Why we have screen option in security appliances? And name some which are useful in stopping the attacks?
- In Junos SRX firewall, NAT process occurs at exactly which step?
- Describe briefly the main flow process of SRX firewall? You should know how SRX process packets and at which stage what processing is being done?
- SRX hardware, NPU, SPU and CP are some of key components. Describe the packet flow wrt SRX hardware process flow?
- NAT has been the most important part of any network, infact now dedicated firewalls are integrated into the large SP and Telecom networks to perform NAT. This is your job to monitor the smooth flow of NAT operation on SRX firewall. Mention the important commands, you have to use frequently to see NAT operations and translations in real time?
- An SRX device is having multiple overlapping rules for IDP. You need to understand which rules will be processed or take precedence first in such scenario?
- You have to ensure your IDP policy is up to date and services are being secured. However some traffic which is going to be always legitimate and not required for any IDP inspection. What feature will you use in such case?
- Give the main steps you may go through to apply and setup a defined IDP policy?
- You must very well know the requirements to setting up SRX chassis cluster. One of those is to connect the control and data planes. Can you brief about the interfaces used for connecting the control and data planes for implementing the chassis cluster?
- As chassis cluster is successfully established, and there is a failure in one chassis. How does cluster ensure that there is no service outage and all the services from one chassis in cluster and seamlessly shifted to other?
- Using chassis cluster setup, you have configured IP monitoring. What is default value of threshold is for IP monitoring in chassis cluster setup?
- You are working as lead network security engineer and you main job is to analyze weekly and monthly main logs and events for your network devices. You have SRX chassis cluster and wish to analyze its logs and related events for analysis or troubleshooting purposes. Which file you should get?
- You have to quickly troubleshoot issues related to physical connectivity in chassis cluster. How can you quickly view the chassis cluster RETH interfaces and their child interfaces?
- Which UTM features on SRX Firewall require licensing and which not?
- Explain briefly the main difference between a UTM policy and a regular Security policy?
- During your normal working hours, you got noticed that users are experiencing spam content frequently. You have been using SRX as UTM and you are utilizing its anti SPAM feature to control the influx of spam in your organization. Which commands you may run in your SRX devices to check the status of spam control?
- You are customizing the security policies in your SRX, and for good performance need to keep HTTP web traffic whitelisted and therefore need bypass it from anti-virus scanning. How can this be achieved?
- Web filtering lets you manage Internet usage by preventing access to inappropriate Web content. Can you mention the main web filtering solutions?
- Which web filtering methods can easily be used without any extra licensing?
- You are supposed to deploy a log collector for your network management requirements, and for that what would be the requirement to deploy it in Junos Space?
- You need to make sure you understand when to use global security policy instead of regular one. Can you identify the key point of global security policy?
- You have been running SRX chassis cluster and recently is issue came up where convergence is not happening as expected during a failover. Now you need to make sure the failover scenario must occur during event of critical interface going down. How can you accomplish this task?
- An IPSEC VPN needs to be setup between multiple branches. For security parameters what are your options for ESP protocols?
- There are multiple policies types in SRX, some are zone based global policies and default policy. Which policy will be processed or inspected at the last and which will be the first one to be inspected?
- In order to setup management access for your Junos devices you should use which specific type of Zones?
- You have an internal server with application listening on TCP port 9000, and now you want external users to get its access using HTTP regular port i.e. 80. One way of achieving this task is by using destination NAT to translate port 80 to port 9000. IS there any other way of doing the same?
- SRX performs fast when there is an existing flow as it does not have to go through all the checks again. However still it needs to check the packet if this is part of an existing flow or not. How can SRX verify on basis of fields in packet whether it belongs to an existing flow or not?
- You have a running chassis cluster with Node0 and Node1. Currently Node0 is primary node, but for some reason Node0 needs to be restarted to get rid of some issue in hardware. This will make Node 1 as primary node. How can this be performed assuming RG is 1?
- You want to make sure of your policies on specific times of the week, and for easily doing so you need to know what Junos feature has the capability of doing it?
- When attacking a network or a corporation, hackers have to go through a reconnaissance attack to gather as much data and network information as possible, to later use it for launching the attack. Can you name some of the techniques used of reconnaissance attacks?
ANSWERS @https://ipwithease.com/shop/
Check our new website https://networkinterview.com For Free Video Courses, TechBlog, Mindmaps, Cheatsheets and much more.
ABOUT THE AUTHOR

Founder of AAR TECHNOSOLUTIONS, Rashmi is an evangelist for IT and technology. With more than 12 years in the IT ecosystem, she has been supporting multi domain functions across IT & consultancy services, in addition to Technical content making.
You can learn more about her on her linkedin profile – Rashmi Bhardwaj

 ANSWERS @
ANSWERS @