Table of Contents
Cloudflare DDoS Protection automatically detects and mitigates DDoS attacks at the network edge. It safeguards websites, APIs, and applications without impacting performance or availability.
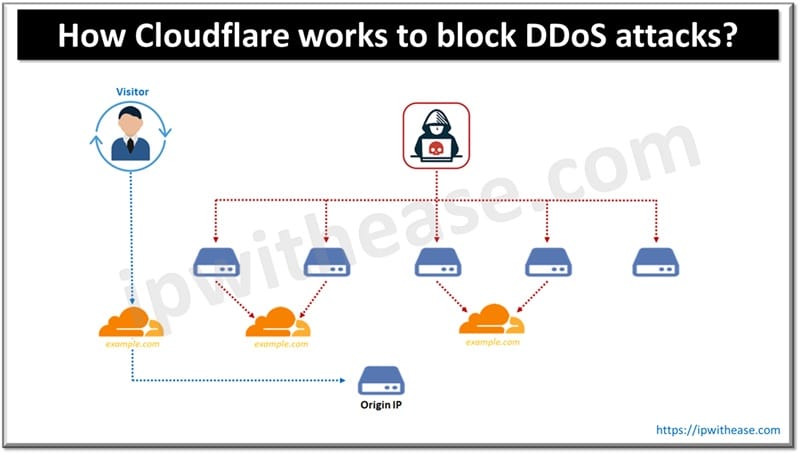
A typical denial of service or DDoS attack used by hackers commonly in cybersecurity space is overwhelming organization networks with volumes of traffic to bring your systems down and make your website URL inaccessible as servers will become overloaded and will not be able to handle legitimate user requests. The public domain name service (DNS) looks up the IP addresses which are used by the organization hosting domain and sends a volume of traffic to bring down systems.
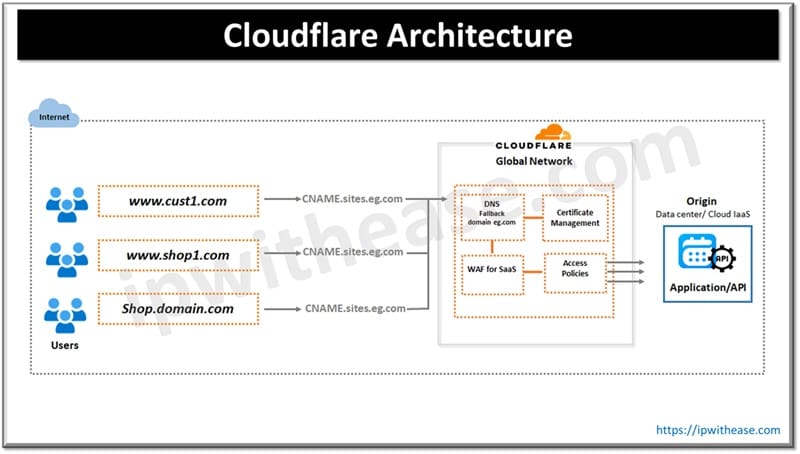
Cloudflare works like a private directory where you put Cloudflare number under your name. If anyone does a lookup of hosts in your domain the request will be forwarded to Cloudflare server which will filter the bad request and only legitimate request will go to server who will provide the services to end users.
In this article we will learn about Cloudflare, how Cloudflare works? how Cloudflare works in blocking DDoS attacks.
What is a DDoS attack?
Denial of service or DDoS attacks are very common and widely used by hackers to bring down servers worldwide. As per latest trends and research there is 358% increase in DDoS attacks compared to previous year which is actually a substantial jump which is quite concerning. A typical DDoS attack overwhelms the network with malicious traffic and servers refuse to service the legitimate access requests of end users.
DDoS attacks are carried out on network connected devices by a group of computers or bots as they are called. Hacker initiates remote instructions to ‘bots’ and ‘bots’ sends requests to target server IP – it is just like a jam on highway due to unruly traffic which causes denial of legitimate traffic to move on highway.
Cloudflare DDoS Protection
As cyberattacks are on rise and DDoS attacks are a very common tool which is widely used by hackers the work of Cloudflare has increased tremendously for its customers with its robust infrastructure blocked (20.5 million DDoS attacks) this year. Cloudflare is a large-scale network having robust security services to protect organizations, their private and public networks, users, data and applications.
Cloudflare operates worldwide across 330 countries. With 388 Tbps capacity and 13,000 network peers it is the largest global network with robust infrastructure. To peer traffic from any part of the Internet it is also connected to every Internet exchange. Cloudflare’s massive global network handles voluminous traffic which peaks at 77 hits/ per second during its peak and 57 hits / per second during normal operations. Cloudflare detects and blocks 209 billion cyberthreats every day on an average.
Cloudflare is a zero trust, least privileged enterprise network. Network broadcast range for (TCP/UDP) both for (IPv4 and IPv6) traffic in its anycast networking is supported. Shortest path availability over the Internet for Cloudflare servers is ensured by using BGP in traffic inspection. During DDoS attacks, high bandwidth capacity and request distribution across numerous Cloudflare servers ensures network stability and availability for Cloudflare customers.
The Quicksilver service of Cloudflare is responsible to perform services related to server updates, access policies establishment, rate limiting, firewall rules etc. The Cloudflare network uses its own key management system to ensure keys are secure during rest and transit.
Cloudflare Categories
Cloudflare design its own servers and have two categories of systems
- Private core servers – this is the control plane holding all customer configuration, data and logging information.
- Public edge servers – on edge server internet and private traffic terminates and inspected before getting routed to its destination.
Every server in Cloudflare network runs identical hardware and software stack. The edge servers run Linux OS tailored for speed and scalability. Each server runs all Cloudflare products and services used by its customers for securing their network and applications.
Using Cloudflare Effectively
But remember that signing Cloudflare is not enough to protect the network. If attackers know the IP address it can always send traffic directly as the server is available on the Internet and the attacker can bypass Cloudflare network.
Let’s look at certain tips and configurations which provide protection against bypassing Cloudflare DDoS protection.
- Keep all subdomains on Cloudflare – In Cloudflare where ‘direct’ subdomain is added automatically. Rename this ‘direct’ subdomain to something else which can’t be easily guessed or removable. Hackers can use subdomain names to look up IP addresses.
- Wildcard subdomains – wildcard subdomains are not proxied and should be removed from Cloudflare DDoS protection. As hacker can use wildcard subdomain name to look up IP address
- Reviewing DNS records – DNS records should not refer or mention IP address check SPX and TXT records thoroughly.
- Do not host mail or other services on a web server – if the mail server is hosted on a web server, a hacker can get an IP address from outgoing mail.
- Outbound connection initiation on user action – attacker can set up a web site to monitor or use a public service monitoring service to get IP which connects to a unique URL.
- Information disclosure vulnerabilities – keep your web server updated with all latest patches against known information disclosure vulnerabilities
- Change origin IP address configured on Cloudflare – DNS records historical records might contain original IP address before you signed up for Cloudflare and hacker can get IP address from archived record.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj