As enterprises are moving their workloads on cloud, securing them becomes of paramount importance. As per Gartner forecast worldwide public cloud penetration would increase by 18.4% in 2021. As organizations’ IT spending is geared more towards the cloud, they are facing more regulations, a high rate of data loss, and a surge in attacks on their cloud applications. To address these challenges more focus is required to have clear visibility and security for their software as a service (SaaS), platform as a service (PaaS) and infrastructure as a service (IaaS) clouds.
Today we look more into details of two options which are growing in adoption to secure cloud environments – CSPM and CWPP and understand how they work, their purpose, features, and usage.
CSPM (Cloud Security Posture Management)
Cloud Security Posture Management (CSPM) secures workloads from the outside by assessment of secure and compliant configurations of cloud platforms control plane. CSPM provides tools to support compliance monitoring, integration with DevOps processes, incident response, risk assessments and risk visualization.
It identifies unknown or excessive risks across an organization’s entire cloud enterprise, including cloud services for computing, storage, identity and access management and offers continuous compliance monitoring, configuration drift prevention, and security operations centre breach investigations.
Organization specific custom policies can be created to define the desired state of configuration for cloud infrastructure; which can use CSPM to monitor the policies. It enables enterprises to detect and address configuration issues, automatically checks cloud environments against compliance and security violations and enables automated steps to fix them.
CSPM Characteristics
- Get a single pane of glass view for all accounts on AWS, Azure, GCP and Oracle
- Cost management and resource organization
- Cloud migrations, backup and recovery
- Effective management of perpetual shift to cloud infrastructure
- Compliance based on range of standards such as CIS, NIST, HIPPA etc. and security concerns tied to misconfiguration problems
CSPM Use cases
- Constant visibility and enforcement of security controls across in multi cloud environments
- Cloud workload and services discovery and identification
- Threat detection and alerts prioritization
- Risk management, risk visualization and prioritization in cloud environments
- Continuous compliance monitoring against industry and geography specific regulations
CWPP (Cloud Workload Protection Program)
CWPP is a workload centric security protection solution for any type of workloads, inclusive of physical servers, virtual servers, containers, and serverless workloads. It furnishes a single pane of glass for visibility and protection across on premises and cloud environments.
CWPP has eight layers of control and having capabilities as under:
- Configuration, hardening, and vulnerability management including scanning of vulnerabilities before software being pushed into production environments
- Network firewalls, visibility, and Microsegmentation
- System integrity checking and assurance
- Application control and allow listing
- Memory protection and protection from exploits
- Threat detection and response, behavioural monitoring
- Vulnerability shielding with host-based monitoring
- Anti-malware scans
CWPP Characteristics
- Ability to identify vulnerabilities earlier in process
- Detection of exploits and active threats
- Greater context and investigation capabilities in incident resolution
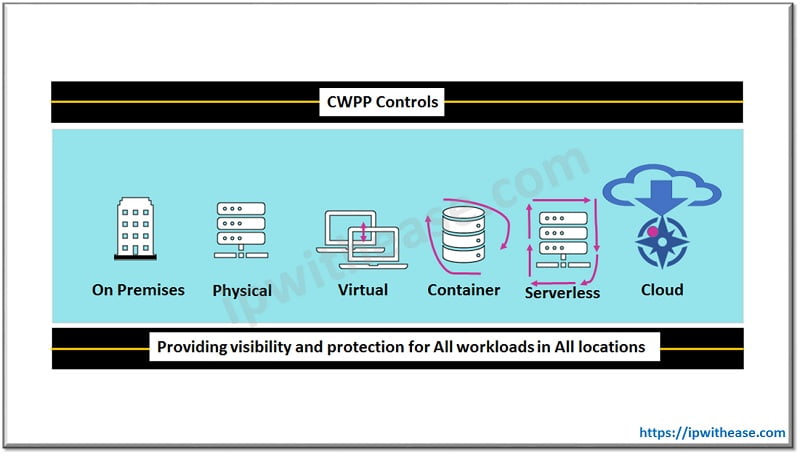
CWPP Use cases
- Discovery and inventory of workloads across diverse environment
- Assurance of System integrity and Applications whitelisting in Virtual machines
- Behavioural monitoring of workloads and threat detection and prevention capabilities
- Container and Kubernetes protection
- Serverless protection
Comparison Table: CSPM vs CWPP
Below table summarizes the differences between the two:
PARAMETER | CSPM | CWPP |
| Definition | Solution for assessment of cloud environment against best practises and security violations and provides steps required for their remediation often using automation | Host centric solution which target the unique requirements of server’s workload protection in hybrid data centres |
| Visibility | Constant visibility and enforcement of security controls across multi cloud deployments | Maintaining inventory of workloads and discovery |
| Data Protection | Identification and discovery of cloud workloads and services | Applications whitelisting and assurance of integrity |
| Threat Protection | Alert prioritization and threat detection | Workload behaviour monitoring and threat detections |
| Policies | Cloud risk management, risk visualization and risk prioritization | Container and Kubernetes protection |
| Data Sovereignty | Continuous compliance monitoring as per industry and geography specific regulations like GDPR, FISMA etc | Serverless Protection |
| Providers | MacAfee, Microsoft, Netskope, Obsidian, OpsCompass, Orca security | Palo Alto Networks, Deep security, Check Point, Symantec Data Center Security |
| Products | Accurics, Amazon web services, Bitglass, BMC, Cipher cloud, CloudPassage | Kaspersky, Prisma Cloud, Trend Micro, CloudGuard IaaS, Symantec |
Download the compariosn table: CSPM vs CWPP
Conclusion
If goal is to protect data and applications on IaaS/PaaS then you probably need CWPP. If the requirement is to assess and comply with configuration best practices of IaaS/PaaS, then CSPM would be a better choice.
Continue Reading:
What is Cloud Workload Protection Platform (CWPP)?
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj