Table of Contents
Introduction: Cloud Workload Protection Platform (CWPP)
The term Cloud Workload Protection Platform (CWPP) is used to describe the process of maintaining workloads that are been transferred across different cloud environments securely. It is therefore mandatory the entire workload to be functional for any kind of cloud based application without introducing any security risks.
Gartner firstly defined CWPP as a technology solution “Primarily used to secure server workloads in public cloud infrastructure as service environments”. In simple words CWPPs provides the ability to public cloud providers and customers workloads to remain secure when they pass through their domain.
On the other hand, workload security protection becomes very complicated in hybrid data center infrastructures that involves physical, on premises hardware and public cloud architecture provided as a service (IaaS). The main reason is because workloads pass among different vendors and hosts, therefore the responsibility for protection has to be shared.
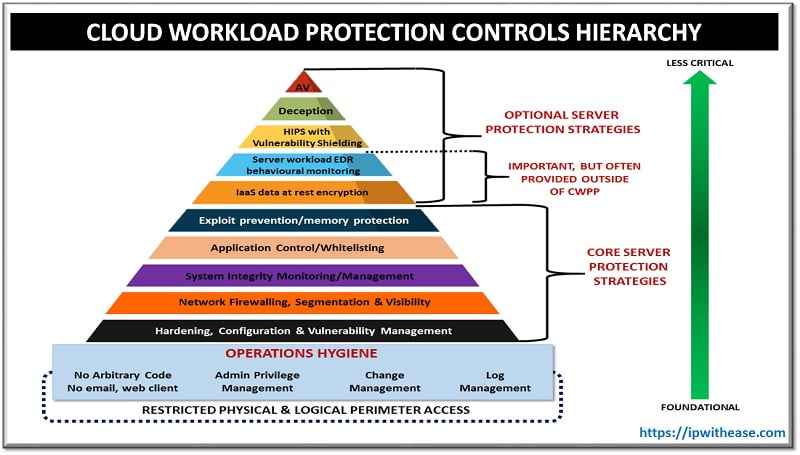
Methods of Cloud Workload Protection Platform (CWPP)
There are two main methods used in order to protect workloads with CWPP. They are briefly described below:
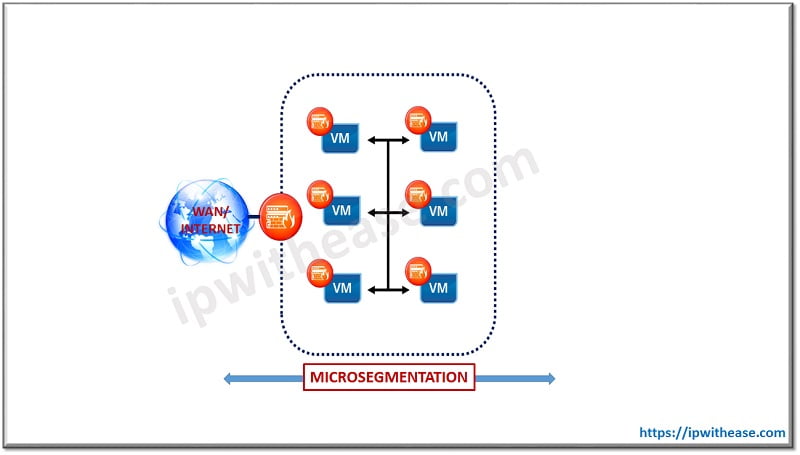
- Micro Segmentation: The most effective way to protect workloads is by implementing a network security technique called micro segmentation. In this method, the first task is to divide the data centers into distinct security segments down to the individual workload level.
Then the second part of the process is the definition of security controls for each segment. The result is the replacement of physical firewalls by network virtualization technologies, allowing micro segmentation to introduce security policies that isolate and protect individual workloads.
In this way, malware is prevented from migrating from one server to another within the environment.
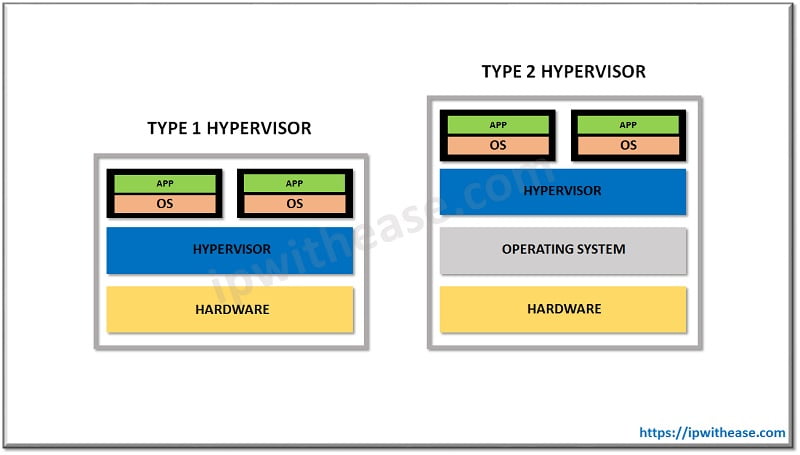
- Bare Metal Hypervisor: Another very effective method that provides additional workload protection is Bare Metal Hypervisor (Type 1 Hypervisor). With the term Hypervisor we define a type of virtualization software that supports the creation and management of virtual machines by separating computer’s software and hardware.
The first phase of this method is the installation of Bare Metal Hypervisor directly on the hardware of a physical machine. Then the Hypervisor will create virtual machines that will be isolated from each other. The result is increased security because workloads will be unaffected from an attack.
Advantages of Cloud Workload Protection Platform (CWPP)
The implementation of Cloud Workload Protection Platform technologies have the following three advantages:
- Reduced Complexity: Due to the fact that CWPP targets security for Cloud Native Conditions, it provides a simpler and cost efficient approach compared with legacy tools. As a guideline, CWPP technology provides the security value as expected even when running inside a container or VM where organizations don’t control the lower levels of the technology stacks.
- Consistency: The second advantage of implementing CWPP is consistency. It is very relevant to the usage of the cloud by most organizations. As microservices architecture result to a lifespan decrease of each workload, a reduction of visibility over the long term occurs as well. Another benefit of CWPP implementation is a consistent view, without any limitation on numbers and location of the workloads.
- Portability: The third advantage of CWWP is portability, most products that foster security regardless of location of a workload or the type. For example, a workload running an on-premises hypervisor today is moved to an IaaS provider tomorrow. Also a container running on an engine in a dedicated IaaS today moving into AWS Fargate or Azure Container Instances tomorrow.
Conclusion
In this article, a detailed guideline of CWPP implementations and scope of this technology has been addressed. An expert analysis of which methods are mainly used in the cyber community industry have also been defined.
The most three effective advantages have been presented and hopefully on the future cloud security will result in a more stable and affordable environment of simple users.
Cloud service providers addressing the unique requirements of the enterprise market should pay close attention to the various currently needs and reduce prices to the public.
Public investments should arise from government funding opportunities for scientists and engineers to research in depth for increased security mechanisms and facilities to deal with cloud attacks.
Continue Reading:
Microsegmentation vs Zero trust
Cymulate: Breach & Attack Simulation
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj