Business and trading have never been easier, and technology is the reason for that! There are so many channels, apps, sites, and more that have made business more convenient and accessible. But the fact is that this increased level of digitization comes with its downsides and disadvantages.
Your first worry should be ensuring your online security and privacy, especially if you are an avid internet user. There are various strategies to maintain strong internet security like using a top-grade VPN service as recommended by VPNRanks.
Cyberattacks and hacks on businesses and their channels have never been more common, so they recommend using VPNs for your business operations. If you run a business, you understand the sensitivity of business data. The safety of business data can mean the difference between a successful business and an unsuccessful one.
In this blog, we will learn more about the different kinds of cyberattacks that businesses can face and what you can do to prevent them.
5 Types of Cyberattacks to Protect Your Business From
Before we talk more about the different kinds of cyberattacks, we will discuss what exactly constitutes a cyberattack:
What is a Cyberattack?
A cyberattack is defined as an unauthorized person gaining access to a digital system through unscrupulous/illegal means. This person is known as a hacker/cyberattacker/threat actor.
Cyberattacks lead to negative effects, such as data loss, server malfunction, data manipulation, and even financial loss as a consequence. To fight cyberattacks, cybersecurity is used. As a result, the world of cybersecurity, or ‘cybersec’ as it’s known, has been snowballing.
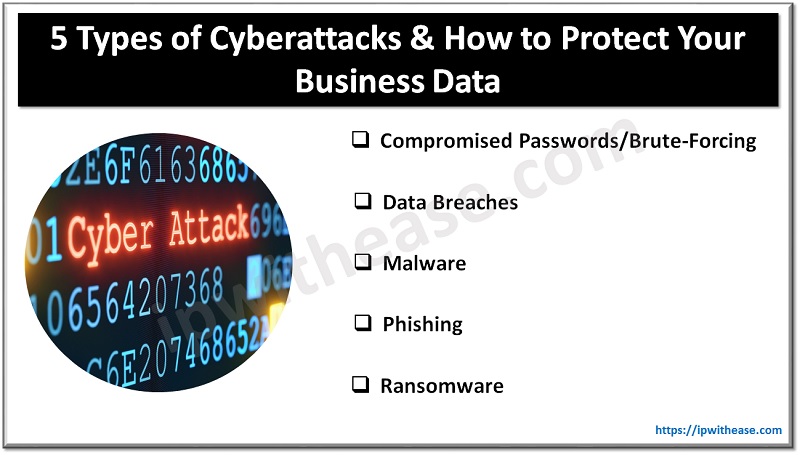
Different Types of Cyberattacks
1. Compromised Passwords/Brute-Forcing
There are two main types of password attacks that businesses can face. Fake websites are quite common. They fool people into accessing those websites and rope them into using their private passwords on those fake websites.
These websites then capture these passwords and supply them to the hacker, who will then use them to access important accounts.
The best way to prevent this from happening is to avoid clicking on random links and instead choose to use authentic links to access your websites.
Another technique that hackers use is brute-forcing passwords with dictionary attacks. This technique is a bit outdated, but the reality is that it can still work if you are using a weak password. So instead, create a strong password made of numbers, alphabets, special characters, and even case sensitivity.
2. Data Breaches
As the name suggests, the primary purpose of a data breach is to access data stored on the company’s servers. Data breaches are quite a common form of cyberattack, and they only happen when there is some sort of vulnerability in the cybersecurity framework of the company.
There is a reason why big companies like Google, Facebook, and the like release timely security updates. Cybersecurity threats are constantly evolving, and you have to have a constantly updating security framework to keep up with these threats.

3. Malware
Malware is one of the most common types of cyberattacks. The most common purpose of malware is to steal your data or to slow down your system. It is usually installed on your system when you click on unknown links. However, malware can also become a tunnel into your system that can lead to data breaches.
The easiest way to avoid malware is to use antivirus software. Reliable antivirus software can prevent a lot of malware from getting into your system. In addition, antivirus software such as Avast or Norton has massive antivirus identification databases that are always evolving to stop all malware threats.
4. Phishing
Phishing is one of the oldest tricks in the book for hackers. Phishing is done mainly through emails. These emails are disguised as alerts, password warnings, or any other kind of clickbait that will get you to open the email and click the link. These days messages (SMS) and phone calls are also involved.
Phishing is thankfully easily avoidable, as it is quite easy to spot. Phishing emails are usually identifiable by the bad grammar in their emails or the alerts in the email being too obvious to spot.
5. Ransomware
Ransomware is one of the more tedious forms of cyberattacks. It is quite similar to malware, but the one thing that separates it from malware is that once it enters your system, it encrypts or locks your files, and then it alerts you that you need to pay money to unlock your files or get your files back.
In many cases, ransomware also deletes your files and asks for money to give them back, but then they take your money and don’t give it back to you. Antivirus software is recommended for ransomware, too, as it can detect the most popular ransomware forms quite easily.
You can also use VPNs like ExpressVPN to encrypt your data traffic and hide from such attacks. In addition, VPNs like ExpressVPN also detect basic malware forms and inform you in advance.
Wrapping Up
Cyberattacks are unavoidable. There will always be hackers looking to take advantage of your business. But with the guidelines mentioned above, you can ensure you avoid cyberattacks as much as possible.
Continue Reading:
WannaCry Ransomware Fully Explained
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.