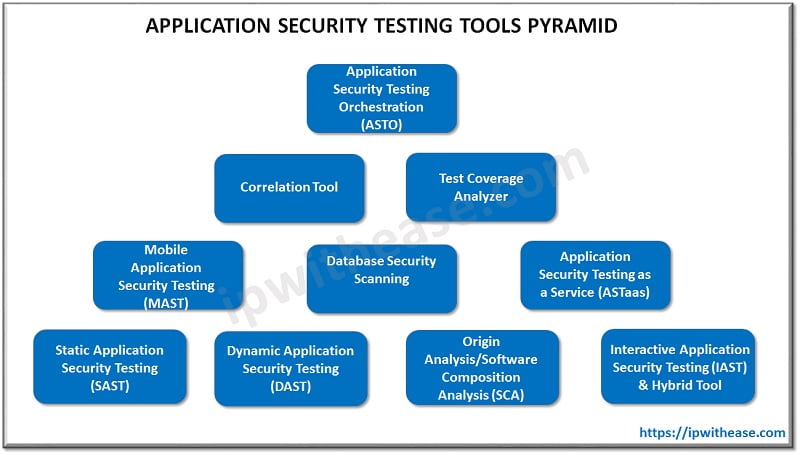
Application security testing (AST) is used to automate the testing, analyses and reporting of security vulnerabilities. It is an essential part of the software development. Below are the types Application security testing approaches –
- Static Application Security Testing (SAST) is a white-box security testing that analyzes source code from the inside.
- Dynamic Application Security Testing (DAST) is a black-box security testing that analyzes source code in application from the outside.
- Interactive Application Security Testing (IAST) works from within an application code to detect and report issues while the application is running.
- Software Composition Analysis (SCA) scans code to provide visibility into open source software components, including license compliance and security vulnerabilities.
DAST – Dynamic Application Security Testing
In this article, we will have a detailed discussion on DAST tool. DAST tool finds vulnerabilities in a real-time application by injecting malicious payloads to identify and detect attacks like SQL injections or cross-site scripting (XSS).
Features of DAST:
- Black box security testing.
- Requires a running application.
- Detects vulnerabilities towards the end of the SDLC.
- Expensive to fix vulnerabilities.
- Can discover run-time and environment-related issues.
- Detects vulnerabilities in apps like web applications and web services.
Components of DAST:
The two key components of DAST are –
- A crawler element to pass through the application and discover as many URLs as possible.
- A detection component to execute the multiple requests against each URL including attack payloads.
How do DAST tools work?
DAST tools enables the review of a web application by testing all the points. DAST simulates malicious user behavior and emulates random actions which can be completed by complex test cases or interactions with third-party systems like email registration validation or an SMS validation code. DAST intercepts calls including web cryptography API, keychain, network, file system, SQL, as well as content providers, broadcast receivers and URL handlers etc. All will be intercepted, collected, probed and checked for vulnerabilities to determine the attack.
Key benefits of DAST:
- Flexibility
- Coverage
- Consistency
- Enablement
- Scalability
- Comprehensiveness
DAST Detects:
- Input/output validation: (e.g. cross-site scripting and SQL injections).
- Server configuration mistakes.
- Authentication issues in user login.
Vulnerabilities in Applications DAST can address:
- Cross-site scripting
- SQL injection
- Path disclosure
- Denial-of-service
- Code execution
- Memory corruption
- Cross-site request forgery
- Information disclosure
- Arbitrary file
- Local file inclusion
- Remote file inclusion
- Buffer overflow
- Other (PHP injection, JavaScript injection, etc.)
Pros of DAST
- Platform agnostic
- Penetration testing utility
- Independent of the application
- Immediately finds vulnerabilities that could be exploited
- It does not require to access the source code
- Technology independent
- Low false positives
- Identifies configuration issues
Cons of DAST
- Poor security risk coverage
- Unclear vulnerability reporting
- Lack of zero-days support
- Slow
- Lack of continuous support
- Lack of DevSecOps support
- Not adapted to modern technologies
- It does not find the exact location of a vulnerability in the code
- Test can be time-consuming
- Not highly scalable
- No code visibility
- Slow scans
Why is DAST Important?
DAST has an important role in identification of vulnerabilities in an application during production. DAST software tests the HTTP and HTML interfaces of application. Running a DAST test helps to find those vulnerabilities before an attacker does. For example, a DAST solution can detect SQL injection attacks that attempt to disrupt the database of a web application with fake SQL code. Since attackers are launching more and more attacks at the application layer, therefore it becomes a business necessity to implement a DAST application testing.
DAST Tools
- Appknox is a dynamic DAST solution that can find the vulnerabilities in running applications. It is designed to flag vulnerabilities that are commonly used in like Man in the Middle Attacks (MiTM).
- Veracode Dynamic Analysis is a DAST solution that enhance automation and easy to deploy.
- Netsparker is a DAST solution that provides deep vulnerability scanning for any web application. It detects vulnerabilities with zero false positives. Netsparker can find SQL Injection, Reflected XSS, Local File Inclusion, Invalidated Redirect, Remote File Inclusion and Old Backup Files.
Three ways to use DAST:
- DAST can test vulnerabilities in the software development life cycle (SDLC).
- In collaboration with DevOps, DAST identifies the problem and DevOps fixes it.
- In combination with other tests as part of a comprehensive approach to web security.
Conclusion
A Dynamic Application Security Testing (DAST) analysis is specifically designed to detect conditions indicative of a security vulnerability in an application while in its running state.
Continue Reading:
White Box Testing vs Black Box Testing: A Detailed Analysis
Managed Security Service Provider (MSSP) – Cyber Security
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj