Communication in the networking world or Internet happens using a commonly used stack TCP/IP. Protocols available at transport layer are Transmission control protocol (TCP) and user datagram protocol (UDP). Limitation of both protocols is however, they are not encrypted hence subjected to breaches in the form of eavesdropping, forgery and tampering by malicious attack actors. To fulfil this gap TLS and DTLS are used which ensure encryption to secure communication between hosts.
Today we look more in detail about TLS and DTLS protocols, their key features, advantages and the differences.
TLS Protocol
TLS operates on top of the TCP layer but below the application layer. It provides secure transport connection between applications such as web server and browser. It establishes connection by agreeing on algorithms, sharing secrets and performing authentication. It uses symmetric encryption and data integrity to transfer application data. The session is established using a handshake protocol. TLS has several versions TLS 1.0, 1.1, 1.2 and 1.3.
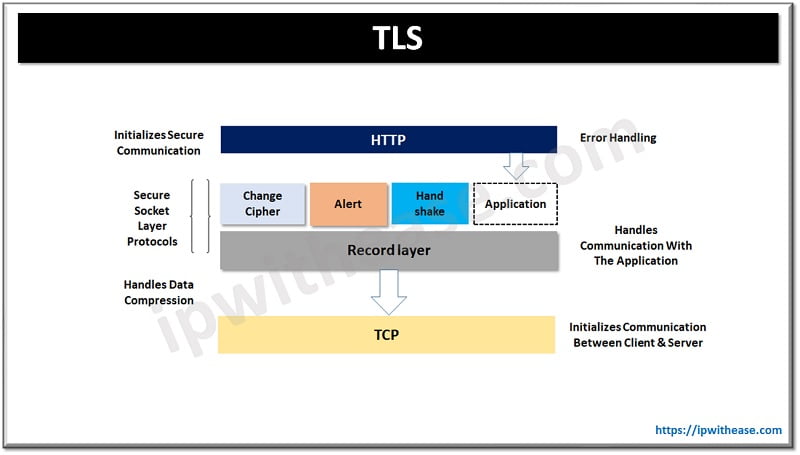
Features of TLS protocol
- TLS provides authentication, encryption, and integrity.
- It gives logging and auditing functions which are built into the protocol.
- It gives granular control over what can be transmitted or received on an encrypted session.
Use cases of TLS protocol
- Email encryption
- Network access
- Single sign-on devices
- Signing and encrypting documents and code
DTLS Protocol
Datagram Transport Layer Security (DTLS) is defined in RFC 6347 (V1.2). It is a session layer communication protocol designed to protect data privacy. It was designed to deliver authenticated and encrypted application data with low latency as it uses User datagram protocol to establish low latency connections between applications on the Internet. It is useful for time sensitive communications like VoIP, DNS lookup, and video or audio playback.
DTLS is meant to prevent data packages from getting lost or arriving in incorrect order. It uses a simple retransmission timer to prevent this with each endpoint continue to retransmit its last message until reply is received.
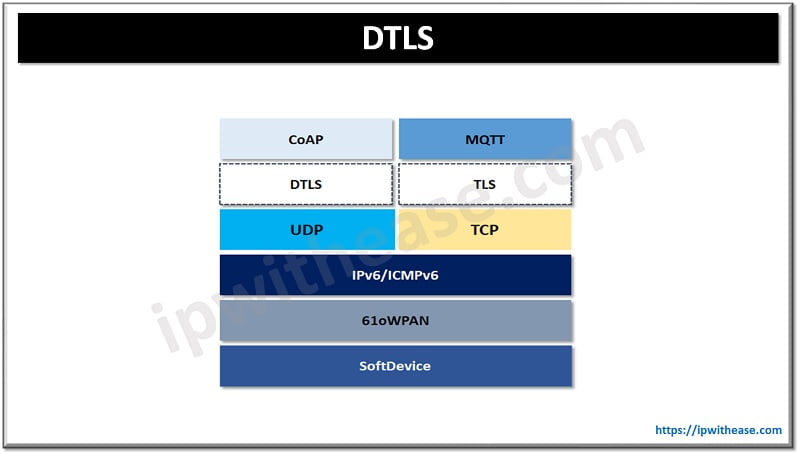
Features of DTLS protocol
- Especially built to handle unreliable transport layers and does not suffer from delays which occur in streaming protocols.
- It provides secure communication while protecting application communication without the exchange being overheard or intercepted.
- It provides end to end security by using cookie exchange technique in which when client sends its ClientHello, the server responds with HelloVerifyRequest message having opaque cookie which client need to send back to confirm fake IP address is not used.
Use cases of DTLS
- Ideally suited for delay sensitive applications using datagram transport
- Used in VoIP by combining RTP (Secure Real-time Transport Protocol) to authorize the remote party and secure sensitive data
- Used in online gaming especially for multiplayer online games where low latency is crucial
- Streaming audio and video for conferencing
Comparison: TLS vs DTLS Protocol
Below table summarizes the differences between the two types of protocols:
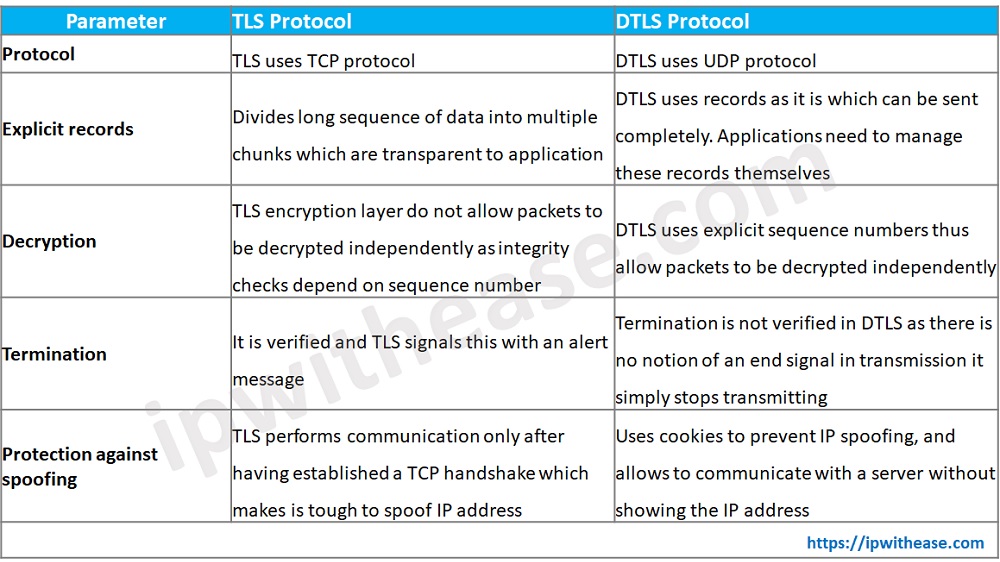
Download the comparison table: DTLS vs TLS
Continue Reading:
SSL vs TLS: What is the difference?
What is Datagram Transport Layer Security (DTLS)?
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj