Table of Contents
Introduction to FlexVPN
Virtual private networks (VPNs) are mode to provide low cost and secure communications between sites while improving productivity with extending corporate networks to remote users. (Remote access VPNs). Major network provider Cisco supports a variety of VPN types and most of them require different configurations, show commands, and debugging commands. Each VPN type also supports different features. FlexVPN solution is introduced by Cisco to simplify VPN deployments and covers all VPN types such as Site to site VPN, Hub and spoke VPN (including spoke to spoke traffic) and remote access.
Today we look more in detail about Flex VPN, learn about its architecture, features, advantages, quick facts etc.
What is Flex VPN?
Flex VPN is a framework to configure IPSec VPNs on Cisco devices it was created for simplification of deployment of VPN solutions of all types of VPNs except GETVPN. FlexVPN is based on IKEv2 and not supported on IKEv1. It integrates different configuration parameters into one style hence also termed as unified Overlay VPN. Since it is based on IKEV2 which has some myriad benefits over IKEv1 some of them are listed here:
- Dead peer detection and network address translation traversal – Internet Key exchange version 2 (IKEV2) provides built in support for dead peer detection (DPD) and network address translation traversal (NAT-T).
- Certificate URLs – certificates can be referenced via a URL and hash instead of being sent within IKEv2 packets to avoid fragmentation.
- Denial of service attack resilience (Anti-DOS) – IKEv2 does not process a request until it identifies the requester, which addresses to some extent the denial-of-service issues as were in IKEv1 which can be spoofed to perform extensive cryptographic processing (expensive in nature) from false locations.
- EAP support – IKEv2 allows use of extensible Authentication protocol (EAP) support for authentication
- Multiple crypto engines – one engine can handle IPV4 traffic and another engine can handle IPV6 traffic or one engine can handle both IPV4 and IPV6 traffic.
- Reliability and state management (Windowing) – uses sequence numbers and acknowledgments to provide reliable and error free processing and logistics and shared state management.
- IKEv2 Suite-B support – are set of cryptographic algorithms promulgated by national security agency as part of cryptographic modernization program. Suite-B for internet key exchange and IPSec is defined under RFC-4869. The components of Suite-B are as under:
- Advanced encryption standard (AES) – 128- and 256-bit keys are configured in IKEv2. For data traffic AES should be used in Galois counter mode (GCM) configured in IPSec transform set.
- Elliptic curve digital signature algorithm (ECDSA) – configured in IKEv2 profile.
- Secure hashing algorithm 2 (SHA-256 and SHA-384) configured in IKEv2 proposal and IPSec transform set.
Features of Flex VPN
- It supports interpretability
- It support dynamic routing
- It supports IPSec routing
- Failover mechanism is simple and also source-based failover is supported
- Offers full AAA management
Configuration Components – Flex VPN
The following IKEv2 /IPSec configuration components are required for Flex VPN
| Components | Description of components |
| IKEv2 proposal | ●It is mandatory ●Defines encryption, integrity algorithm, DH group used for protection in negotiation of IKEv2 SA ●Can specify more than one entry for each option ●Do not contain authentication method and SA lifetime in proposal |
| IKEv2 policy | ●It is mandatory ●Match peers and associates the IKEv2 proposal by binding the previously create IKEv2 proposal to select during negotiation with the defined VPN peer |
| IKEv2 Keyring | ●Mandate only if using PSK authentication ●Used to define pre-shared keys |
| IKEv2 Profile | ●It is mandatory ●Define local/remote IKEv2 identities ●Define local/remote authentication type ●Define IKEv2 keyring while using PSK or PKI Trustpoint (if using certificate authentication) |
| IPSec Transform Set | ●Acceptable security protocols and algorithms for IPSec SA |
| IPSec Profile | ●References the IPSec Transform Set if NOT default ●References the IKEv2 Profile if NOT default ●IPSec Profile attached to the Tunnel interface |
Smart Defaults – Flex VPN
The Flex VPN configuration can be minimized using smart defaults of IKEv2 which provide default values for all components excluding IKEv2 profile and Keyring (In case PSK is used). Smart defaults can be modified based on need, and will only be displayed in the running-config if using command ‘Show running-config all’ , can be disabled by using ‘no’ before command. All defaults can be deactivated, modified or restored.
| Description | Show command | Default values |
| transform set | Show crypto ipsec transform -set default | crypto ipsec transform-set default esp-aes 128 esp-sha-hmac |
| IPSec Profile | show crypto ipsec profile default | crypto ipsec profile default set transform-set default set ikev2-profile default |
| IKEv2 Proposal | show crypto ikev2 proposal default | crypto ikev2 proposal default encryption aes-cbc-256 aes-cbc-192 aes-cbc-128 integrity sha512 sha384 sha256 sha1 md5 group 52 |
| IKEv2 Policy | show crypto ikev2 policy default | crypto ikev2 policy default match fvrf any proposal default |
| IKEv2 Authorization Policy | show crypto ikev2 authorization policy default | crypto ikev2 authorization policy default route set interface route accept any |
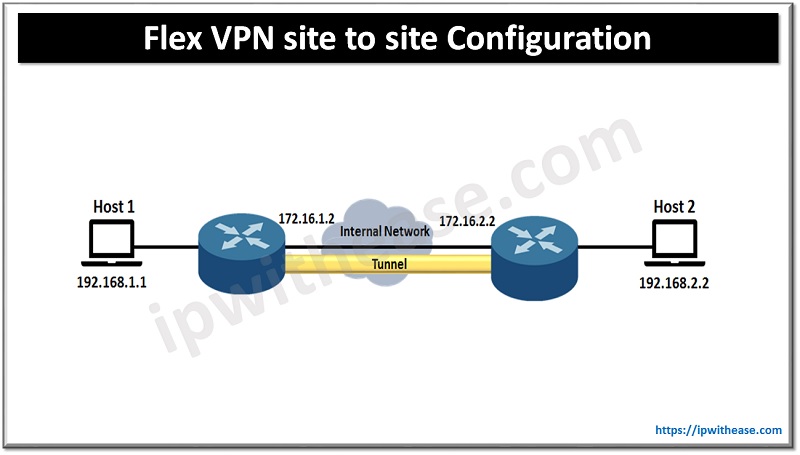
Flex VPN site to site Configuration
Configuration sample for Site-to-Site VPN:
Branch 1
hostname branch1
!
crypto ikev2 keyring KR
peer branch2
address 172.16.2.2
pre-shared-key local cisco123
pre-shared-key remote 123cisco
!
crypto ikev2 profile default
match identity remote address 172.16.2.2 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local KR
!
interface Loopback0
ip address 192.168.1.1 255.255.255.0
!
interface Tunnel0
ip address 10.10.0.1 255.255.255.252
tunnel source FastEthernet0/0
tunnel destination 172.16.2.2
tunnel protection ipsec profile default !Continue Reading:
Introduction to GETVPN: Group Encrypted Transport VPN
GETVPN vs DMVPN: Understand the difference
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj