What are Hash Functions?
What are Hash Functions?
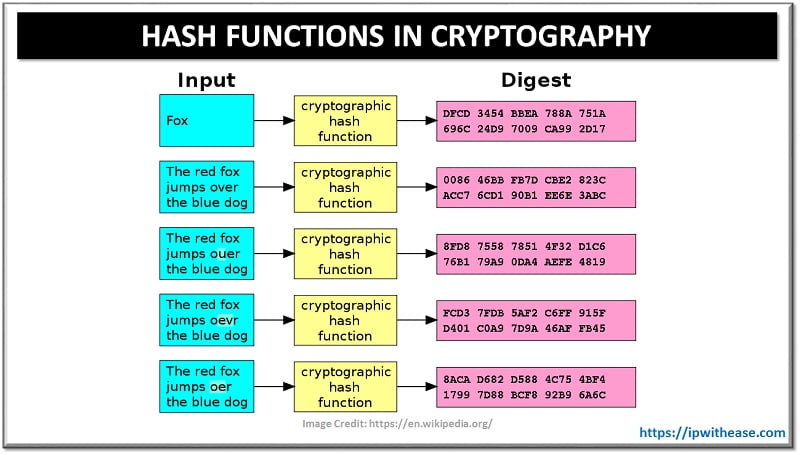
The hash function is an algorithm that, with mathematical functions of different data lengths, produces a specific fixed-length value. It is a one-way function, and since there is no relation between both the text being interpreted and the summary value, it is difficult to derive the actual data from the summary value received. The same meaning for the same data is produced in the hash process, but the value provided by the hash function often varies when there is a minor shift. Digest functions are typically used in fields such as data integrity authentication, password storage, digital signature, message verification code, etc. Blockchain implementations, which are common today, are another field of use.
Cryptographic hash functions create a particular length of output (e.g. 20 bytes) independent of the size of the input they obtain. The manufactured output is unique to the input given. For the same source, the same output still arises, and the output of 2 distinct inputs cannot be the same as each other. “message digest”, “hash”, “checksum” and “digital fingerprint” can be considered the output of the cryptographic hash function. In high-level protection software, they are favored for that purpose.
Usage areas are wide, but they are mainly used for data validation purposes in Cryptography since the working principle of hash functions greatly align with mining technology. Let’s now look at general usage areas of hash functions:
- Instead of retaining user passwords in web apps, the most commonplace of use might be to download and save Hashes in the database. The hash of the user’s password during site authentication is collected and stored in the username database. The hash of the user’s password is taken and contrasted with the stored hash after signing into the site. The same hash means that during authentication, the password provided by the user and the password provided throughout login are the same, and login is permitted.
- As a second and still effective area of use, cryptographic hash functions allow us to understand when the validity of the data we change in data exchanges on the internet is compromised.
- Another use case is to compare big files in situations where the CPU is expensive to compare their content. E.g., by using their Hash, we can easily detect multiplexed picture and video files on our device. We might claim that files with the same Hash are reproduced if we take the Hash of all files once and also save them with the file path.
- Today, popular Blockchain apps are another area of use (Bitcoin, Ethereum, etc.). Hash’s are commonly used in blockchain implementations since “Proof-of-work” can be presented with the most apparent feature to consider.
Why Does Hashing Functions Matter?
It has a wide variety of applications, including conventional hash functions, searches of records, broad analysis of files, and management of data. From the other direction, in information technology systems, such as message authentication and electronic fingerprinting, cryptographic hash functions are commonly utilized. Cryptographic hash functions are a crucial component of the mining process leading up to Bitcoin and play a role in creating new addresses and keys as well.
Mining
For Bitcoin mining, several measures involve hash functions, including checking balance, connecting inputs and outputs of payments, and hashing transfers within a block to form the Merkle Tree. But one of the key reasons the Bitcoin network is safe is that before they can find a feasible solution to the next block, miners need to do a lot of hashing.
Encryption vs Hashing
Encryption is a two-way function where, using an encryption key, information is encrypted and then decoded using a decryption key. The information is encrypted in a way that it can be read-only by approved parties. It is used to discourage unauthorized users from accessing a file’s data by making it unreadable. Most of our ordinary user security and authentication tools are based on encryption protocols such as Two Factor Authentication, SSL security protocols Virtual Private Networks whether enterprise-level or options including going for safe free VPNs. Because encryption aims to safely transfer data (i.e., maintain the security of data).
While on the other hand, the purpose of hashing is to validate data (i.e., protect data integrity). Hashing is a one-way feature where an input data or a string of text produces a unique message digest. It is the method of mapping it to a fixed size output using hash functions on data. It is identical to a checksum which is used to validate the consistency of the file and is useful for comparing an entered value to a stored value without having to interpret the original value.
Continue Reading:
How does a Browser verify an SSL Certificate?
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.

 What are Hash Functions?
What are Hash Functions?