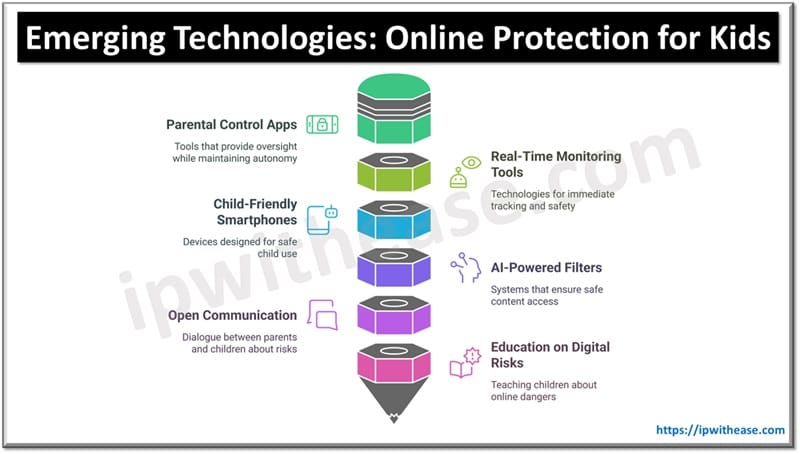
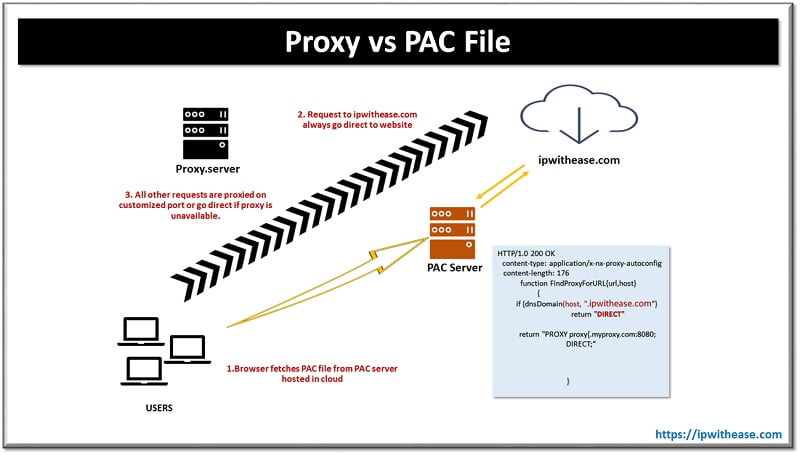
Table of Contents
Nowadays, with everything being digital, cybersecurity is more crucial than ever. As technology advances, so do cybercriminals’ tactics. Staying ahead of these evolving cybersecurity threats can feel like a full-time job. But don’t worry, we’re here to break it down for you and provide some practical steps to protect yourself and your business.

The Changing Face of Cybersecurity Threats
Remember when a strong password was all you needed to keep your data safe? Those days are long gone. Cyber threats of today are complex, varied, and ever-evolving. Let’s examine a few of the most urgent issues:
Ransomware 2.0
Ransomware isn’t new, but it’s getting smarter. These days, cybercriminals do more than merely encrypting your data and demanding money. They’re now threatening to leak sensitive information if you don’t pay. This double extortion tactic puts added pressure on victims to comply.
AI-Powered Attacks
Artificial Intelligence isn’t just for the good guys. Hackers use AI to create more convincing phishing emails, bypass security systems, and even mimic voice patterns for vishing (voice phishing) attacks.
IoT Vulnerabilities
As our homes and offices become more competent, they become more vulnerable. Hackers could use any connected gadget as a point of entry. The Internet of Things (IoT) presents a vast attack surface, from smart thermostats to industrial sensors.
Supply Chain Attacks
Why hack one company when you can compromise its entire supply chain? That’s the thinking behind the rise in supply chain attacks. Cybercriminals can access hundreds or thousands of organizations by infiltrating a single vendor.
The Human Element
Human error remains one of the most significant vulnerabilities despite all the high-tech threats. Social engineering tactics are becoming more sophisticated, targeting our natural tendencies to trust and help others.
“We’ve seen a significant uptick in ATO fraud investigation cases,” reports a cybersecurity expert. “Account Takeover (ATO) fraud often starts with a simple phishing email or a convincing phone call. Individuals and businesses must stay vigilant and educated.”
Protecting Yourself in the Digital Age
Now that we’ve covered the threats let’s discuss what you can do to protect yourself and your business.
Update, Update, Update
It might seem obvious, but keeping your software and systems up to date is one of the most effective ways to protect against cyber threats. Those annoying update notifications? They often contain critical security patches.
Multi-Factor Authentication (MFA)
Passwords alone aren’t enough anymore. Implementing MFA adds an extra layer of security by requiring a second verification form, like a fingerprint or a code sent to your phone.
Employee Training
Your team is your first line of defense. Regular cybersecurity training can help employees spot phishing attempts, understand the importance of strong passwords, and follow best practices for data protection.
Zero Trust Architecture
The old castle-and-moat approach to cybersecurity is outdated. By default, Zero Trust operates on the assumption that nobody, whether inside or outside the network, should be trusted. This model requires verification from everyone trying to access resources in your network.
Emerging Technologies in Cybersecurity
The tools to combat threats are evolving as the threats themselves evolve. Some cutting-edge technologies that are shaping the future of cybersecurity are:
- Blockchain: Beyond cryptocurrencies, blockchain technology is being used to create more secure, decentralized data storage and verification systems.
- Quantum Computing: While still in its infancy, quantum computing has the potential to revolutionize encryption and threat detection.
- Behavioral Biometrics: This technology analyzes patterns in human activity, like typing speed or mouse movements, to verify a user’s identity.
Creating a Cybersecurity Culture
Protecting your digital assets isn’t just about technology – it’s about creating a culture of security awareness. Here are some tips to foster this culture in your organization:
- Lead by example: Executives and managers should promote good cybersecurity practices.
- Make it relevant: Show employees how cybersecurity relates to their roles and responsibilities.
- Reward good behavior: Recognize and reward employees who spot potential threats or follow best practices.
- Regular check-ins: Schedule periodic cybersecurity meetings or updates to keep the topic fresh in everyone’s minds.
The Role of Government and Industry
Cybersecurity isn’t just an individual or organizational responsibility – it’s a global concern. Governments and industries worldwide are stepping up their efforts to combat cyber threats:
Regulations and Compliance
From GDPR in Europe to CCPA in California, new regulations are being implemented to protect consumer data and hold companies accountable for their cybersecurity practices.
Public-Private Partnerships
Governments increasingly collaborate with private sector cybersecurity firms to share threat intelligence and develop better defense strategies.
International Cooperation
Cybercrime doesn’t respect borders, so international cooperation is crucial. Organizations like Interpol and Europol are working to coordinate cybercrime investigations across countries.
The Future of Cybersecurity
As we look ahead, it’s clear that the cybersecurity landscape will continue to evolve. Here are some trends to watch:
- Increased focus on privacy-enhancing technologies
- Growth of the cybersecurity insurance market
- Rise of automated security systems powered by AI and machine learning
- Greater emphasis on cybersecurity in education and workforce development
Your Role in the Cybersecurity Ecosystem
Wondering what you can do to contribute to cybersecurity? The reality is that each person has a part to play in maintaining cybersecurity. Consider these straightforward actions you can implement today:
- Use strong and unique passwords
- Share information online cautiously
- Regular updates of software and operating systems
- Reputable VPN for public Wi-Fi connectivity
- Regular backup of important data
Remember, cybersecurity is a journey, not a destination. It requires ongoing vigilance and adaptation. However, staying informed and following best practices can significantly reduce your risk of falling victim to cyber threats.
As we navigate this ever-changing digital landscape, staying curious and learning is essential. The threats may be evolving, but so are our abilities to defend against them. By working together – individuals, businesses, and governments – we can create a safer digital world for everyone.
So, the next time you read about a new cyber threat, don’t panic. Take a deep breath, review your security measures, and remember that knowledge is power. You’ve got this!
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.