Table of Contents
The document offers an overview of Meraki MX64 and MX65 security appliances, highlighting their specifications, features, and performance metrics like firewall throughput, VPN capabilities, and port configurations, crucial for assessing their suitability for network setups. The Meraki MX is an enterprise security & SD-WAN appliance designed for distributed deployments that require remote administration and security and routing features. It is ideal for network administrators who demand both ease of deployment and advanced feature set.
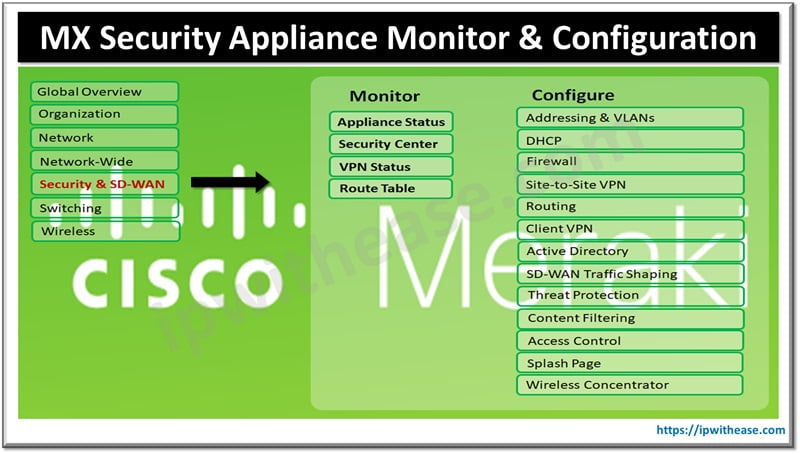
MX Security Appliance Monitoring
Appliance Status
Appliance status page is accessible through Security & SD-WAN then Monitor, Then Appliance status option. Below information is accessible from the Status page.
- General Information about Hostname, MAC address and Model name and location address, WAN IP Primary and Secondary WAN and DNS name and Serial Number, TAGS and Notes, License Information.
- Firmware details like current version and up to date information of firmware.
- Warm Spare option if HA is configured.
- Configuration status information if it is up to date.
- MX device ports status with green colour.
- Live data like utilization of data traffic in graphical representation and historical data of last two hours, one day, last week, last month.
- Uplink information like configuration of WAN and live data of uplink traffic in graphs and historical data of latency and packet loss toward Google DNS.
- DHCP configuration information if configured.
- Location live map on google maps.
- Public IP address of WAN interfaces.
- Hostname of the appliance.
- Detail regarding DHCP leases, as well as a table showing the number of used and available addresses per DHCP subnet.
- Network usage graph of the last two hours, day, week, or month.
- A graphical representation showing what ports are currently active on the appliance
- Historical appliance connectivity and usage data.
Live Tools
Live tools allow network administrators to troubleshoot and debug operational issues remotely.
- Ping WAN appliance from the Meraki Cloud or Ping a specified destination based on hostname, IP, or MAC address.
- Reboot WAN appliance option to reboot the WAN appliance remotely.
- Blink LEDs test to identify which WAN appliance in the Dashboard corresponds to a particular physical WAN appliance. This tool is very useful if we have multiple appliances or need to identify an appliance remotely for an on-site technician.
- Dashboard Throughput tool to run a throughput test between the WAN appliance and meraki.com.
- Traceroute tool test to identify latency and traffic path and troubleshoot potential routing issues by performing a traceroute to the specified host from specified uplink.
- MTR tool is enhanced traceroute test to see packet loss statistics and more for each hop along the way to a specified host.
- Run the DNS lookup tool to test the DNS settings of the WAN appliance by attempting to resolve the specified hostname using the configured DNS servers.
- ARP table test to look at table IP and MAC and VLAN in network.
- Test Umbrella Connectivity test to verify connectivity toward Umbrella.
Security Center
The Security Center provides a centralized view for security filtering events. This includes both IDS/IPS and malware events.
VPN Status
VPN Status depicts overview of VPN Participants and overview of connectivity and uptime graph and latency graph with Site-to-Site peers and Non-Meraki peers.
Route Table
This table has information of Subnet, Name of route, VLAN, Next Hop.
Related: Introduction to Cisco Meraki Family
MX Security Appliance Configuration
MX Addressing and VLANs
Appliance settings are accessible through the Security & SD-WAN > Configure > Addressing & VLANs page and include deployment settings for routed or passthrough / VPN Concentrator mode, client tracking methods, subnet and VLAN configuration, Static LAN routes, and Dynamic DNS settings.
DHCP Services
The Meraki MX appliance provides a fully-featured DHCP service. You can enable and configure the DHCP service on each VLAN individually, or for the whole network if VLANs are not enabled. This is done on the Security Appliance > Configure > DHCP page. The configuration options include:
Networks and Routing
- Border Gateway Protocol (BGP): All MX security appliances support the ability to communicate AutoVPN route information using BGP. This guide introduces key concepts, how BGP is implemented on MX appliances, and how to configure BGP.
- IPv6 Support on MX Security & SD-WAN Platforms – LAN: The document outlines IPv6 support on MX Security SD-WAN platforms LAN, covering configuration, limitations, and troubleshooting. It emphasizes enabling IPv6 functionality alongside IPv4 for seamless network operation.
- IPv6 Support on MX Security & SD-WAN Platforms – Routing: The document discusses IPv6 support on MX Security & SD-WAN Platforms with a focus on routing configurations. It covers IPv6 static routing, OSPFv3, and BGP configurations, highlighting considerations for seamless integration with existing IPv4 routing protocols.
- IPv6 Support on MX Security & SD-WAN Platforms – WAN: The document details IPv6 support on MX Security & SD-WAN Platforms’ WAN interfaces, including configuration steps and considerations. It covers IPv6 addressing, routing, and firewall settings to ensure proper functionality and integration with existing IPv4 networks.
NAT and Port Forwarding
Port Forwarding and NAT Rules on the MX: Servers behind a firewall often need to be accessible from the Internet. You can accomplish this by implementing Port Forwarding, 1:1 NAT (Network Address Translation), or 1 to Many NAT on the MX Security Appliance. This article discusses when it is appropriate to configure each one and their limitations.
Client VPN
- Client VPN Load Sharing: The document explains how to configure load sharing for Client VPN on Meraki MX devices, allowing the distribution of VPN traffic across multiple WAN links to optimize performance and ensure reliability, with detailed steps provided for setup and configuration.
- Advanced Malware Protection (AMP): Advanced Malware Protection (AMP) is an industry-leading anti-malware technology from SourceFIRE, integrated into MX Security Appliances.
- Configuring Active Directory: Active Directory (AD) integration allows you to restrict access to the network and enforce Group Policies based on membership in Active Directory groups on MX appliance.
Firewall and Traffic Shaping
- Connection Monitoring for WAN Failover: The document explains connection monitoring for WAN failover on Meraki MX devices, detailing how to configure monitoring settings, monitor IP addresses, and set up email alerts for WAN link failures, offering insights into ensuring reliable network connectivity and seamless failover in case of primary link failures.
- IPv6 Support on MX Security & SD-WAN Platforms – Security: The document details how to set up IPv6 firewall rules on MX Security & SD-WAN platforms, including inbound, outbound, and VPN traffic, and briefly mentions security features like Advanced Malware Protection and Threat Grid analysis.
- IP Source Address Spoofing Protection: The MX Security Appliance implements several forms of traffic verification to detect and prevent forms of IP spoofing. These are similar in nature to unicast reverse path forwarding in loose mode.
- MX Firewall Settings: The firewall settings page in the Meraki Dashboard is accessible via Security Appliance > Configure > Firewall. On this page you can configure Layer 3 and Layer 7 outbound firewall rules, publicly available appliance services, port forwarding, 1:1 NAT mappings, and 1 to Many NAT mappings.
- Network Objects Configuration Guide: The document provides a guide on configuring network objects in Meraki MX, including IP addresses, subnets, and port ranges, to simplify firewall rules and traffic shaping policies. It explains how to create, manage, and apply these objects effectively within the Meraki dashboard for enhanced network security and performance.
SD-WAN and Traffic Shaping
The MX appliance includes an integrated Layer 7 packet inspection engine, enabling you to set QoS policies, load balancing, and prioritization based on traffic types and applications.
Threat Protection
Threat protection consists of the Source fire® SNORT® intrusion detection engine and AMP anti-malware technology.
Content Filtering
Content filtering allows to block websites based on organizational policies. Feature of Block or whitelist individual websites for additional customization. For example, if you block the “Chat” category this also blocks gmail.com and facebook.com because both websites also offer chat functionality.
- Content Filtering Troubleshooting: The MX includes Content Filtering using Cisco Talos Intelligence, enabling URL classification based on content and security threats. Cisco Talos is among the world’s most extensive commercial threat intelligence groups, offering their expertise to protect Cisco customers and products from current and evolving cyber threats.
Access Control
Access Control Page is available from Security & SD-WAN > Configure > Access Control. It is used to configure Access Control settings such as Under VLAN or Wi-Fi SSID, we have three options under Splash page > None (Direct Access) user can access the network as soon as they are associated. Second option is Click-through, Users must view and acknowledge your splash page before being allowed on the network. Next and last option is Sign-on with Radius Server.
Wireless
MX and Z-Series Wireless Settings: To enable 802.11 wireless networking on your device, click Security & SD-WAN/Teleworker Gateway > Configure > Wireless settings and toggle the SSID status to Enabled. You will need to choose a name for each SSID, a VLAN assignment (if VLANs are enabled on your appliance) and the wireless authentication method.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj