NAC vs Endpoint Security: A Comparative Overview
Securing an organization’s network and its endpoints is crucial in today’s digital world due to the sheer number of cyber threats we experience. On this path, Network Access Control (NAC) and Endpoint Security stand as two crucial pillars. While these two network security solutions are different, they do work in synergy. NAC primarily focuses on regulating and controlling access to your network, while Endpoint Security is dedicated to safeguarding individual devices like computers, smartphones, and servers.
Our goal in this article is to explain the differences between NAC solutions and endpoint security, highlight how they can work together, and how they help immensely in building a strong security posture.
Key Features and Focus of NAC Solutions
Network access control solutions and endpoint security technology need to be distinguished from one another as they serve somewhat different purposes. That said, both are key components for well-managed network resources.
Network access control (NAC) revolves around the practice of regulating the devices connected to your network to ensure only authorized users are able to view business resources. You can think of NAC solutions as a gatekeeper, operating as a network control mechanism. These solutions usually employ authentication protocols such as 802.1X to verify access attempts before granting the request. This proactive approach prevents unauthorized users and malware attacks on network devices.
On the other hand, endpoint security policies focus on protecting the personal devices connected to the corporate network. It protects devices from malware attacks, virus infections, and other malicious cyber attacks. It uses existing security controls such as intrusion detection systems, firewalls, and antivirus software. Endpoint security ensures that each connected device adheres to security policies, monitors them for security risks, and promptly notifies security teams in case of an emerging threat.
While these two solutions differ in what they protect specifically and how they operate, they both work to ensure secure access to business resources. NAC solution provides the basis for secure network traffic and blocks access when there is suspicious activity, endpoint security policies fortify all endpoint devices and authenticate users to protect them against security threats.
Key Features and Focus of Endpoint Security Solutions
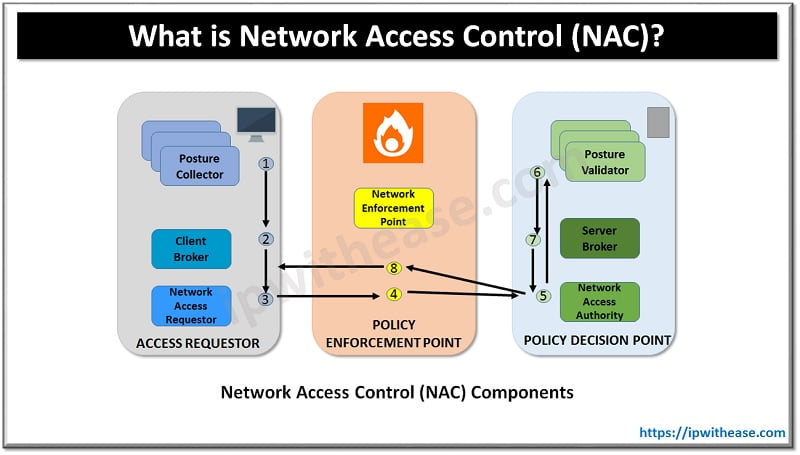
Network Access Control (NAC) solutions are designed with a primary focus on controlling access to company networks. These solutions offer a range of key features and functionalities that are essential for effective network security:
Access control
NAC solutions enforce access control policies based on user devices, identity, and compliance with security regulations. They then authenticate these users with mechanisms like 802.X1 to verify user credentials and grant access based on user privileges.
Endpoint assessment
Effective network access control tools perform comprehensive endpoint assessments to evaluate the security posture of connecting devices. This assessment checks for up-to-date antivirus software, OS patches, and other security measures. Non-compliant devices can be quarantined or given restricted access until they meet the necessary criteria.
Guest Networking
NAC allows you to provide limited access to guests or business partners while also enforcing a certain level of security control. Therefore, you can still work with external actors such as contractors without sacrificing your network security.
Policy Enforcement
NAC systems enable organizations to establish and enforce security policies consistently across all connected devices. This helps maintain cohesive security throughout the network. Access policies also help organizations limit the exposure of sensitive data.
How NAC and Endpoint Security Complement Each Other
Protecting individual devices, or endpoints, inside your network environment is the focus of endpoint security. These solutions provide a selection of fundamental capabilities and protection against specific cybersecurity threats:
Antivirus and Antimalware
Endpoint security tools always monitor devices for potential malware and virus infections to ensure computer security. They also regularly update their threat databases to stay ahead of emerging security risks and remove any malware they may detect.
Data Loss Prevention (DLP)
DLP monitors and controls data transfers to protect sensitive data. The main role of DLP solutions is to protect devices against potential data leaks and ensure the confidentiality of sensitive information on a private network.
Endpoint Encryption
Endpoint security tools often involve encryption capabilities to secure the communication between the data center and the user’s own device. Encryption protects this communication by rendering the data unreadable to outside sources.
Patch Management
Keeping an operating system up to date is crucial to ensure it’s protected against potential threats. Endpoint security prioritizes patch management to stay ahead of the malicious actors and keep all software updated with the latest security patches they have.
Real-World Scenarios: Combining NAC and Endpoint Security
Wellington College decided to implement NAC solutions to protect their private network as they had over 1,000 students with 2 or 3 devices each. They said that now they are able to get devices online faster than ever and posture checking is facilitated drastically thanks to NAC. This decision was due to a network-wide issue they had after the students came back from the summer break.
Due to a Conficker worm infection they experienced on one student device, they also implemented endpoint security policies which enabled them to take measures against such incidents and prevent them from further spreading into the connected devices in their network.
Challenges and Considerations in NAC and Endpoint Security Integration
While there are many advantages to integrating Network Access Control (NAC) with Endpoint Security, there are also difficulties that businesses must overcome. Assuring interoperability between NAC and Endpoint Security solutions from various manufacturers is a crucial factor. Furthermore, finding the ideal balance between user ease and security might be difficult. The difficulties of implementing and sustaining these linked systems must also be managed by organizations. Adapting to changing cyber threats and enforcing security policies, particularly in BYOD (Bring Your Own Device) environments, are continuous problems. A smooth and reliable security posture must be achieved by effectively addressing these factors.
Conclusion: Achieving Comprehensive Security with NAC and Endpoint Protection
(NAC) network access control solutions are designed to protect any corporate or private network against unauthorized access and provide secure access to internal resources even from remote locations. Endpoint security, on the other hand, has the sole purpose of protecting an individual device against the specific threats targeting them such as malware or viruses. Therefore, these two approaches are significantly different in terms of their functions.
That’s why one of these is not the alternative to the other. You need to use both of them in your network to have a bulletproof cybersecurity technology that acknowledges the risks targeting the business network as a whole, and the attacks directed toward endpoint devices that can compromise sensitive data.
Continue Reading:
What is Network Access Control (NAC) ?
BYOD Could Be Putting Your Company’s Security at Risk
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.