Table of Contents
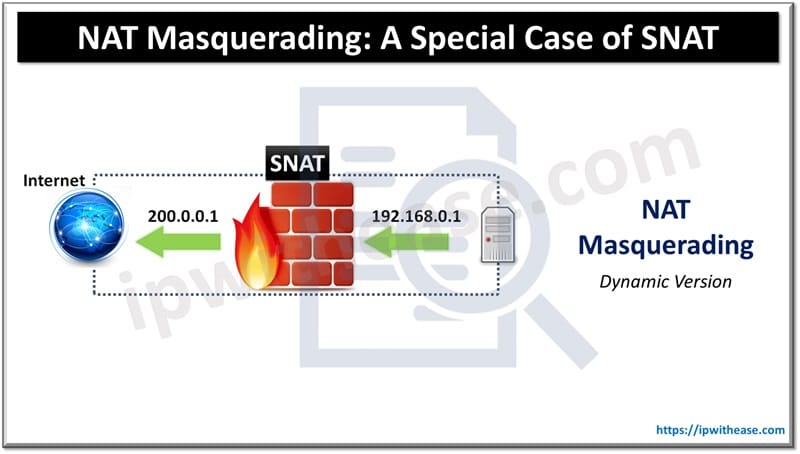
NAT masquerading is considered a special case of Source Network Address Translation (SNAT). While both involve translating the source IP address of outgoing packets, there are some key differences that make NAT masquerading unique.
Differences Between SNAT and NAT Masquerading
- SNAT (General):
- In general SNAT, a private IP address (or a range of IP addresses) is manually translated to a specific public IP address or a pool of public IPs.
- SNAT typically requires predefined mapping between internal private IP addresses and external public IP addresses.
- It is often used in enterprise environments with multiple public IP addresses or more static configurations.
- NAT Masquerading (Special Case):
- NAT masquerading is a dynamic version of SNAT where all outgoing traffic from internal devices is translated to the single public IP address of the NAT device (often dynamically assigned by ISPs in consumer networks).
- NAT masquerading typically doesn’t require manual configuration of specific public IP addresses. The router or firewall uses its public IP and dynamically handles port translation (PAT).
- This is commonly used in environments where the external IP address is dynamically assigned, such as in home networks or small businesses.
- It’s efficient for networks with fewer public IP addresses, allowing multiple devices to access the internet using a single IP.
Comparison Table
Below table summarizes the differences between both terms:
| Feature | SNAT (Source NAT) | NAT Masquerading |
| Purpose | Translates the source IP address of outgoing traffic to a specific IP address. | Translates the source IP address to the IP of the interface from which the traffic is leaving. |
| Use Case | Typically used when a server or group of hosts need a fixed public IP for outbound traffic. | Commonly used in scenarios where the outbound IP may vary, such as in home or small business routers with dynamic IP addresses. |
| Configuration | Static mapping between internal IP and a specific external IP. | Dynamic mapping where the external IP is automatically the interface’s IP. |
| Flexibility | More granular control over the translated IP, allowing specific IP assignments. | Simplified configuration, ideal for environments with changing IP addresses. |
| Scalability | Can be more scalable as it can support many internal IPs translating to one or more fixed IPs. | Easier to set up in small networks but might be less flexible for larger deployments. |
| Example Scenario | Enterprise environments with dedicated public IP addresses for certain services. | Home or small business environments where the ISP assigns a dynamic IP address. |
| Configuration Complexity | Requires specifying the external IP address explicitly in the configuration. | Minimal configuration as the external IP is the same as the interface IP. |
| Behavior on IP Address Change | Static external IP remains fixed regardless of interface IP change. | The external IP changes if the interface IP changes (often with dynamic IP from ISPs). |
To Summarize
SNAT is a broader concept where a source IP is translated to a specific external IP or pool of IPs. NAT masquerading is a form of SNAT where all devices on a private network are dynamically translated to a single public IP, typically with dynamic port address translation (PAT). Thus, NAT masquerading is essentially a simplified, more dynamic form of SNAT, commonly used in consumer-level networking setups.
Related FAQs
Q.1 What are the main uses of NAT masquerading?
NAT masquerading is primarily used in situations where an organization or network wants to enable internet access for devices within a private network that lacks unique public IPs. It’s common in home and office networks and helps in conserving public IPs while maintaining internet connectivity.
Q.2 How does NAT masquerading differ from other NAT types?
Unlike static NAT, which maps one private IP address to a single public IP, NAT masquerading dynamically maps multiple private IP addresses to a single public IP address. This is ideal for networks with many internal devices needing internet access without individual public IP addresses.
Q.3 What are the security benefits and risks of NAT masquerading?
NAT masquerading hides internal IP addresses, which can provide a layer of security by obscuring network structure. However, it’s not a full security measure because it does not filter or inspect traffic. To enhance security, NAT masquerading is often combined with a firewall for more robust protection against unauthorized access.
Q.4 How can I troubleshoot connectivity issues with NAT masquerading?
Common troubleshooting steps include checking the NAT configuration for errors, ensuring the public IP is reachable, and verifying firewall rules that might block or interfere with the masqueraded traffic. Additionally, checking logs for NAT translation issues can reveal whether the problem lies in translation or other network components.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj