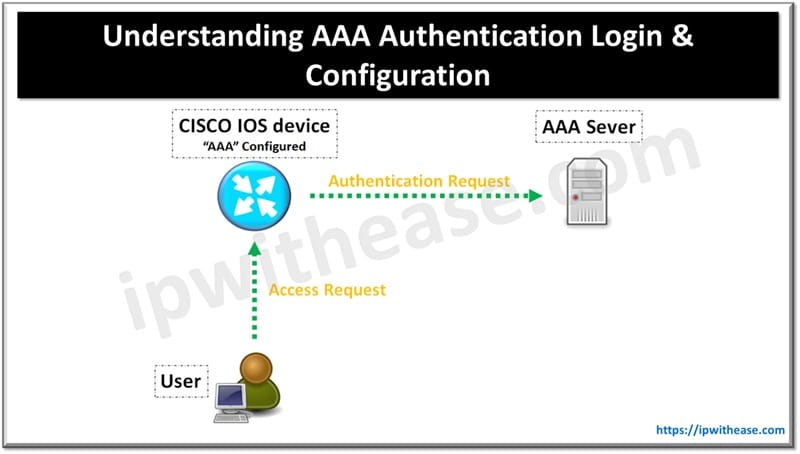
Table of Contents
In today’s digital world, protecting the network infrastructure against cyber threats has become more important than ever. More and more companies depend on internet-based activities, and witness increased numbers and complexity of network attacks. Among several tools organizations use to enhance their security posture, unlimited residential proxies help hide a network’s identity and enable safe management of web traffic.
However, proxies are just one tool comprising an extensive strategy plan needed to guard against various risks, such as ransomware, phishing scams, and malware. This post will examine some common cybersecurity threats businesses face and explore how companies can protect their networks against a constantly changing threat landscape.

Understanding the Risk Environment
IT professionals are becoming increasingly worried about the complexity of cybersecurity threats. As technologies advance, cyber criminals come up with new strategies and that presents even more challenges for organisations that need to keep up with the constantly changing environment and develop firm defensive mechanisms ready to face any kind of cyber threats.
Most Common Network Threats and Vulnerabilities
There are many types of cyber threats, but some popular ones include:
- Malware is malicious software designed to harm or cause damage to any computer, server, client or computer network.
- Ransomware – a type of malware that locks or encrypts data, making it inaccessible to the legitimate user. Later a ransom is being requested in order to restore access.
- Phishing scams trick users into providing sensitive information, such as passwords or credit card numbers, by pretending to be a trustworthy entity in electronic communications.
Another significant threat is presented by Distributed Denial of Service (DDoS) attacks, where multiple systems flood a targeted system’s bandwidth or resources on one or more web servers. This may make an entire corporate network inaccessible, even if temporarily, and disrupt normal business processes.
While companies can and should add an additional layer of security and hide their network’s online identity by using unlimited residential proxies, they would be required to develop a more complex defense strategy. Proxies must be part of a broader security strategy that addresses the full spectrum of potential vulnerabilities.
How Vulnerabilities Are Exploited
Attackers are constantly scanning networks for exploitable vulnerabilities. These can be as simple as out-of-date hardware/software or unsecured network configurations and some security gaps that were left unsecured. Once identified, cybercriminals can use these flaws to gain unauthorized access, steal sensitive information, and disrupt services.
For example, hackers often use open Wi-Fi networks through which they intercept data in transit. These also include weakly secured endpoints like unpatched computers or mobile devices easily accessible to malicious intruders. Companies need to continuously identify, manage, and mitigate them by constantly monitoring and updating their security policies.
By thoroughly comprehending the threat landscape, organizations can better prepare themselves for any strategies aimed at them and efficiently combat these threats. The following sections will discuss specific security measures businesses can employ to reinforce their networks against the typical range of risks outlined above.
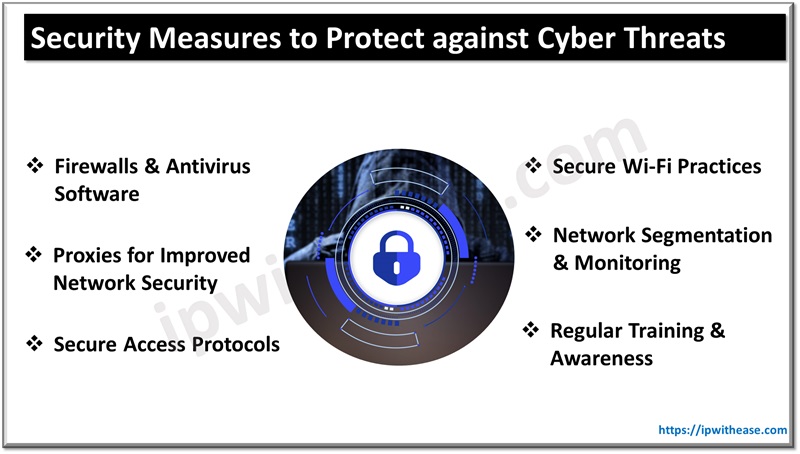
Fundamental Network Security Measures
To address such common hazards highlighted above, numerous basic security measures must be implemented. They form a foundation that prevents unauthorized access and data breaches while keeping up with emerging risks.
Use Firewalls & Antivirus Software
The firewall is one of the first lines of defense in network security. A firewall acts as a barrier between potentially unsafe external networks and the internal network. Firewalls can help block unauthorized or potentially dangerous traffic by monitoring both incoming and outgoing traffic through pre-configured security rules. To eliminate the risk of malware entering the system, whether intentionally or inadvertently, it would be advisable to use a comprehensive antivirus software program that is supported by a firewall.
Implementing Secure Wi-Fi Practices
Unsecured Wi-Fi networks are the most susceptible to cyber-attacks. Securing a Wi-Fi network can be achieved by strong encryption such as WPA3, hiding the network SSID, and setting strong passwords. Also, guest networks can be configured separately from main networks to keep away sensitive data while allowing visitors internet access.
Using Proxies for Improved Network Security
Proxies are intermediaries between a user’s device and the internet, improving network security and privacy. By using proxy servers to route traffic, organizations can conceal their actual IP addresses thereby safeguarding them from attacks and unauthorized usage.
Network Segmentation and Monitoring
Dividing a network into smaller manageable parts does not only improve performance but also improves its security features. With segmentation, however, one is able to control the flow of traffic more effectively and isolate issues where they occur so that they cannot spread out across the entire system inadvertently, among other things, like firewalls running on your computer within your office premises that have already been configured properly for proper functionality. Continuous monitoring of network traffic allows for potential threats to be recognized early on so that the company is able to respond quickly to unusual activities that could signify possible intrusions.
Secure Access Protocols
It is important that only authorized individuals gain access to vital information. When applying secure access protocols, such as Virtual Private Networks (VPNs), data transmission can be encrypted and provide secure remote access to the network. For internal access, technologies like Network Access Control (NAC) can be used to enforce security policies and prevent unauthorized devices from connecting to the network.
Regular Security Training and Awareness
However, even with essential technological advances, human factors always pose a significant threat. Regular training sessions for employees must be held regularly about basic security awareness, recognizing phishing attempts, and secure internet practices. Letting all employees know the latest security protocols can significantly reduce human errors that lead to breaches.
Conclusion
Protecting your network infrastructure has become a critical business priority in the face of cyber threats that are becoming increasingly sophisticated. Adopting a few key strategies—from using firewalls and antivirus software to employing unlimited residential proxies—can significantly improve a company’s cybersecurity situation.
The cybersecurity industry is constantly changing; thus, vigilance and adaptability are needed to stay one step ahead of various risks. By incorporating some basic measures into their systems, firms can create a safe network that will stand not only today’s challenges but tomorrow’s ones. A well-guarded computer system means safer data handling and increased viability of a firm at large; this should never be forgotten.
Follow these practices diligently and consistently to keep your company strong and secure against common risks, safeguarding your organization’s digital future.
Continue Reading:
Site to Site VPN vs Remote Access VPN
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.