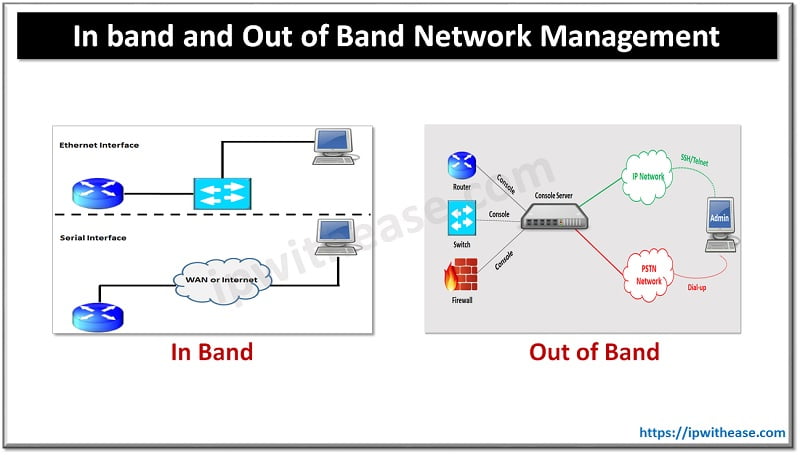
Earlier we used SPAN sessions to capture the real time traffic on the Cisco devices. Starting from CISCO IOS 12.4.20 onwards there is a new feature available called the Embedded Packet Capture. With the EPC we can save the packets traversing the router on flash disk and later pull them out using TFTP or FTP on your machine for further analysis.
Let us use the below topology to understand how the Embedded Packet Capture feature is configured:
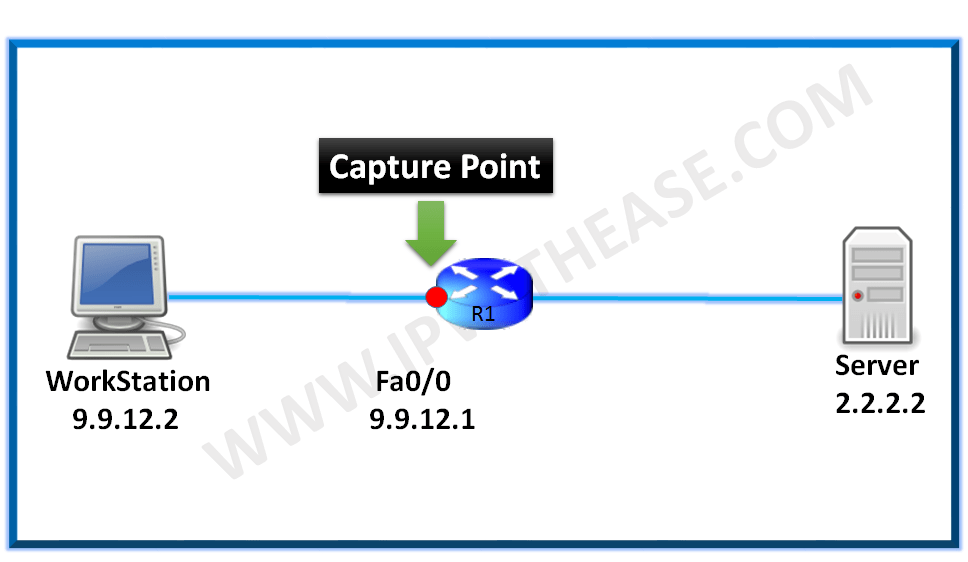
We will capture ingress & egress traffic on Fa0/0 port of the router.
Steps to configure Embedded Packet Capture:
Step 1 –
- Linear: Stops capture when buffer is full.
- Circular: Overwrites the old data when buffer is full.
Configuration on R1:
R1#monitor capture buffer pcap size 1024 circular
Step 2 –
ip access-list extended epc
permit ip host 9.9.12.2 host 2.2.2.2
permit ip host 2.2.2.2 host 9.9.12.2
Associate the ACL with monitor capture:
R1#monitor capture buffer pcap filter access-list epc
Filter Association succeeded
Step 3 –
Our ACL is configured to capture traffic both ingress and egress on interface Fa0/0 on R1.
We also need to enable ‘ip cef’ on router to minimize the cpu utilization on the router.
R1(config)#ip cef
R1#monitor capture point ip cef Fa0/0_Capture fa0/0 both
Step 4 –
R1#monitor capture point associate Fa0/0_Capture pcap
R1#monitor capture point ip cef Fa0/0_Capture fa0/0 both
R1#
*Apr 23 13:22:32.887: %BUFCAP-6-CREATE: Capture Point Fa0/0_Capture created.
Step 5 –
R1#monitor capture point start Fa0/0_Capture
R1#
*Apr 23 13:24:34.587: %BUFCAP-6-ENABLE: Capture Point Fa0/0_Capture enabled.
Verification
As of now we don’t see any packets in the capture buffer as below:
R1#sh monitor capture buffer all parameters
Buffer Size : 1048576 bytes, Max Element Size : 68 bytes, Packets : 0
Allow-nth-pak : 0, Duration : 0 (seconds), Max packets : 0, pps : 0
Associated Capture Points:
Name : Fa0/0_Capture, Status : Active
Configuration:
monitor capture buffer pcap size 1024 circular
monitor capture point associate Fa0/0_Capture pcap
monitor capture buffer pcap filter access-list epc
Now we ping from workstation to the server and then check again the output:
R2#ping 2.2.2.2 source 9.9.12.2 re 100
Sending 100, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 9.9.12.2
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (100/100), round-trip min/avg/max = 16/22/44 ms
R1#sh monitor capture buffer all parameters
Buffer Size : 1048576 bytes, Max Element Size : 68 bytes, Packets : 200
Allow-nth-pak : 0, Duration : 0 (seconds), Max packets : 0, pps : 0
Associated Capture Points:
Name : Fa0/0_Capture, Status : Active
Configuration:
monitor capture buffer pcap size 1024 circular
monitor capture point associate Fa0/0_Capture pcap
monitor capture buffer pcap filter access-list epc
R1#sh monitor capture buffer pcap
13:34:10.691 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa1/0 Fa0/0
13:34:10.711 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa0/0 None
13:34:10.727 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa1/0 Fa0/0
13:34:10.751 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa0/0 None
13:34:10.763 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa1/0 Fa0/0
13:34:10.783 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa0/0 None
13:34:10.795 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa1/0 Fa0/0
13:34:10.811 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa0/0 None
13:34:10.819 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa1/0 Fa0/0
13:34:10.843 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa0/0 None
13:34:10.851 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa1/0 Fa0/0
13:34:10.859 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa0/0 None
13:34:10.875 UTC Apr 23 2018 : IPv4 CEF Turbo : Fa1/0 Fa0/0
We see above the packets have been captured.
Now to stop the capture use below:
R1#monitor capture point stop Fa0/0_Capture
*Apr 23 13:37:53.719: %BUFCAP-6-DISABLE: Capture Point Fa0/0_Capture disabled.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj