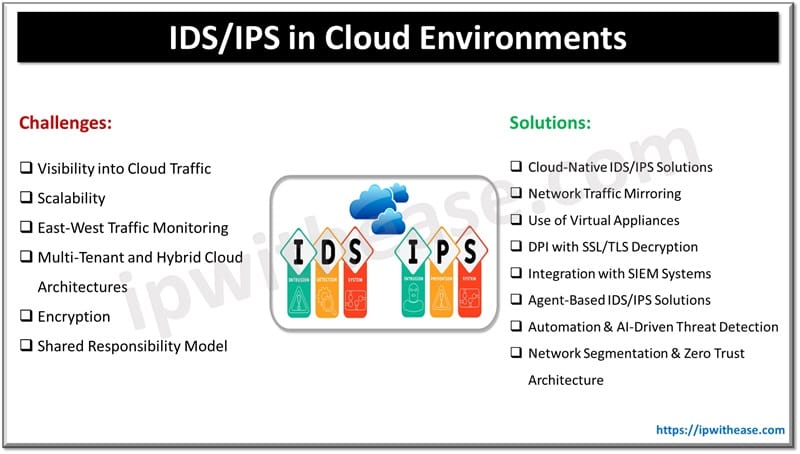
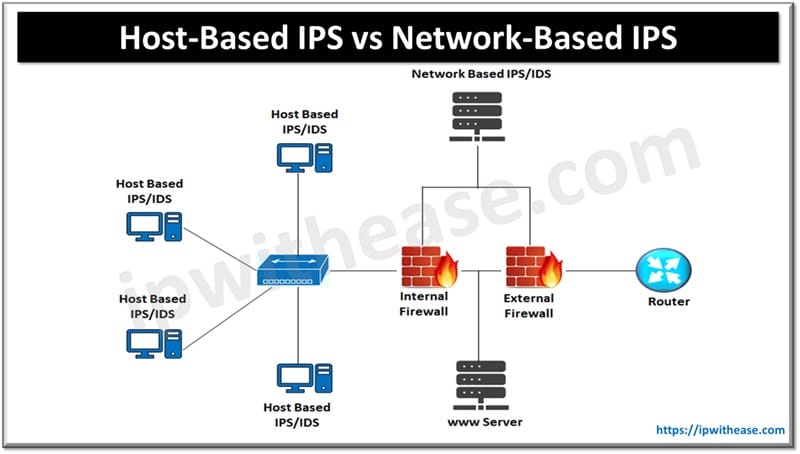
Table of Contents
The TCP SYN Flood attack is a type of cyber-attack that involves sending a large number of malicious packets to a target computer or server in order to overwhelm it with traffic. The goal of such an attack is to take down the target system or make it unresponsive. In this article, we will discuss what the TCP SYN Flood attack is, the risks associated with it, the types of attacks, and how to protect yourself. We will also provide some best practices for mitigating the threat of a TCP SYN Flood attack.
What is the TCP SYN Flood Attack?
The TCP SYN Flood attack is a form of Distributed Denial of Service (DDoS) attack. It is a type of cyber-attack in which a malicious attacker sends a large number of packets to a target computer or server in order to overwhelm it with traffic.
This will cause the target system to become unresponsive or even crash. The attacker is typically able to accomplish this by sending a large number of TCP SYN packets (a type of packet used in the communication between two computers) to the target system.
This will cause the target system to continuously wait for the response to the SYN packets that never arrive, thus overwhelming the system with traffic. The attacker can also use spoofed IP addresses in order to make the attack more difficult to trace.

What are the Risks of a TCP SYN Flood Attack?
The risks of a TCP SYN Flood attack are numerous. For example:
- The attack can take down an entire website or service, resulting in lost revenue and customers.
- It can also cause significant disruption to business operations as well as damage to a company’s reputation.
- The attacker may be able to gain access to confidential data or even execute malicious code on the target system.
What are the Types of TCP SYN Flood Attacks?
There are several different types of TCP SYN Flood attacks.
IP spoofing attack – This type of attack involves sending packets from a spoofed IP address in order to make it difficult to trace the attack back to its source.
Reflection attack – This type of attack involves sending packets to a vulnerable server, which then sends the packets back to the intended target. This can result in an amplification of the attack, as the attacker is able to send a greater number of packets to the target.
How to Detect a TCP SYN Flood Attack?
There are several methods for detecting a TCP SYN Flood attack.
- One method is to monitor network traffic for suspicious activity. This can include monitoring for unusually high levels of traffic, as well as monitoring for traffic coming from unusual locations or sources.
- Another method is to use a Security Incident and Event Management (SIEM) system to monitor for suspicious activity. The SIEM system can be configured to detect and alert on suspicious activity, such as a sudden increase in traffic or traffic coming from unusual locations.
How to Protect Yourself from a TCP SYN Flood Attack?
The best way to protect yourself from a TCP SYN Flood attack is to implement a defense-in-depth approach. This means having multiple layers of security in place. This may include firewalls, intrusion detection systems, and other security tools.
In addition, you should ensure that your systems are regularly patched and updated to prevent attackers from exploiting known vulnerabilities.
What are the Best Practices for Preventing a TCP SYN Flood Attack?
The best practices for preventing a TCP SYN Flood attack include:
- Implementing a defense-in-depth approach to security, which includes firewalls, intrusion detection systems, and other security tools.
- Regularly patching and updating your systems to prevent attackers from exploiting known vulnerabilities.
- Monitoring network traffic for suspicious activity, such as unusually high levels of traffic or traffic coming from unusual locations.
- Implementing rate-limiting on your network to prevent attackers from sending large amounts of traffic in a short amount of time.
- Implementing anti-spoofing measures to prevent attackers from spoofing IP addresses.
- Ensuring that your systems are protected from DDoS attacks by using a cloud-based DDoS protection service.
- Implementing security policies to ensure that your systems are properly secured.
What are the Tools Available for Mitigating a TCP SYN Flood Attack?
There are several tools available for mitigating a TCP SYN Flood attack.
Firewalls – One of the most popular tools is a firewall. Firewalls can be used to block malicious traffic, such as the packets sent by a TCP SYN Flood attacker. Firewalls can also be used to monitor network traffic for suspicious activity, such as unusually high levels of traffic or traffic coming from unusual locations.
Intrusion Detection System – Another tool that can be used to mitigate a TCP SYN Flood attack is an intrusion detection system (IDS). An IDS can be used to detect malicious traffic and alert administrators to suspicious activity. This can help administrators respond quickly to a TCP SYN Flood attack and take corrective action.
Rate-limiting – can be used to limit the amount of traffic that can be sent to a system in a given period of time. This can help prevent attackers from sending large amounts of traffic in a short amount of time.
Conclusion
In this article, we discussed what the TCP SYN Flood attack is, the risks associated with it, the types of attacks, and how to protect yourself. We also provided some best practices for mitigating the threat of a TCP SYN Flood attack, as well as some of the tools available for mitigating such an attack. By following these best practices and using the available tools, you can help protect your systems from the threat of a TCP SYN Flood attack.
Continue Reading:
What is Brute Force Attack? – Cyber Security
Spear Phishing Attack: Cyber Security
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj