Table of Contents
Cybersecurity is taking a major leap this year. With the sudden emergence of Artificial intelligence equipped applications in addition to remote working, cloud computing etc. which have been occupying digital space for quite some time.
Cyberattacks are growing rapidly, becoming more complex and destructive.
There are constant malicious attempts to access, damage, disrupt or steal data and digital infrastructure in cyber space by bad actors. Hackers, disgruntled employees, criminal groups, workers, and nation-states are also sponsoring cyber terrorism.
Some of the common sources of cybersecurity threats are phishing attacks, ransomware, distributed denial of service (DDoS), insider threats, Zero-day exploits and man-in-the-middle (MITM) attacks.
In this article we will look at top 10 emerging cyber security threats of the year.
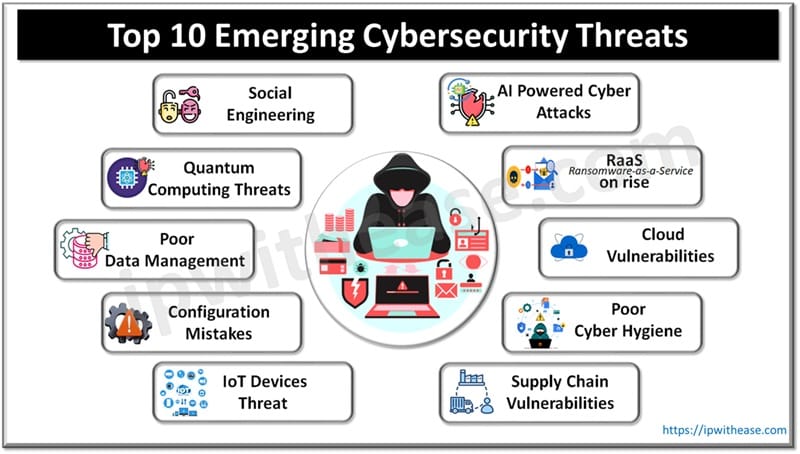
List of Top Emerging Cybersecurity Threats
Social Engineering
The most widely used and easier way to penetrate is to exploit human error. Hackers understand breaking security posture is difficult guarded by sophisticated tools but it is easier to target humans as they are the weakest link in the security. In most of the statistics globally on security breaches, human factors played a big role. Usually, such attacks could use different mediums; one of the most common is an email. Employees often use weak passwords, do not ensure security of their physical devices or mishandle sensitive information, unintentional download of malicious software’s. It is important to raise security awareness among employees and educate them on the latest cybersecurity threats.
AI Powered Cyber Attacks
Attackers are using AI to automate cyber attacks such as phishing, evading conventional security measures, and discovering vulnerabilities faster compared to organizations. Hackers are leveraging AI to write phishing emails, finding vulnerabilities into systems and even hacking them. Educating employees on identification of fake videos, audio or images is pivotal and should be included in regular security awareness programs.
Quantum Computing Threats
With the advancement and use of quantum computing there is a new threat on rise the failing of current encryption algorithms. The quantum apocalypse will make existing cryptography techniques useless as per the prediction done by Gartner by year 2030.
The research is going on to find out quantum resistant algorithms.
Ransomware-as-a-Service (RaaS) on rise
The cyber attackers send phishing emails to its targets, and compromised systems were encrypted due to which legitimate users cannot access the data. To decrypt data huge ransom is demanded else they threaten to put data on the dark web. Employees need to be educated on not opening or clicking malicious emails or links. Applying advanced filtering tools also detect ransomware attempts to system and block them.
Poor Data Management
Increase in risk of cyber-attacks is often attributed to poor data management practices. Storage of data and its handling in the proper way is a crucial step towards handling risk of data breaches. A robust and effective data management policy is crucial to avoid such threats.
Cloud Vulnerabilities
Cloud vulnerabilities are on rise as more enterprises are adopting cloud technology and rely on their service providers for the security of hosted data. The Gartner projects that by 2027 expenditure on cloud services will exceed $1 trillion. Incorrect cloud setup, shadow IT, weak access controls in cloud make it a lucrative field to target.
Managing and maintaining the right cloud security posture is of paramount importance. Implementation of real time threat detection and prevention tools can help in containing or neutralizing these threats.
Configuration Mistakes
Misconfigurations during installation of cyber security tools introduce vulnerabilities. Using weaker passwords, not patching systems, not upgrading systems in the right way, using default passwords for firewalls, databases or installed devices help hackers to run scripted attacks and try different combinations of passwords and usernames on systems, databases, and servers.
Hardening systems in the proper way, doing the configuration in right manner, habit of changing passwords for newly installed devices immediately, establishing a strong configuration management process could help to neutralize this threat to an extent.

Poor Cyber Hygiene
Maintaining good cyber hygiene is essential to avoid cyber threats. Using unprotected wi-fi connections, poor data access policies, lack of multifactor authentication (MFA) increased risk of data breaches. Remote working added exponentially to this threat as risk is increased when the workforce is working from home and using insecure home networks.
IoT Devices Threat
As per Gartner prediction by year 2025 we have 30.9 billion IoT linked devices. IoT devices are often at the high risk of compromise due to lack of strong security features.
Supply Chain Vulnerabilities
All organizations use a lot of vendors or service providers to deliver their services to end customers. At times hackers infiltrate company networks via partner space such as software, hardware, and hosting platforms.
It is crucial that you are aware of the security and compliance posture of your partners. Seek from them relevant security and compliance reports to assess their security posture periodically.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj