Google ADs
 ANSWERS @https://ipwithease.com/shop/
ANSWERS @https://ipwithease.com/shop/
- What is VPN?
- Which functions can be performed with the “packet-tracer” command in ASA?
- What does Cisco ISE stands for?
- When configuring policy-based NAT, which type of access control list should be configured to match both the source and destination IP addresses?
- Which command encrypts all the password on a Cisco device?
- What are the pre-requisites for configuring IP SSH version 2 on a Cisco device?
- What is DMZ?
- Describe the functionality of product Cisco ISE?
- What are the three Violation Actions?
- What are the two modes in which Cisco ASA can be configured?
- Which command is the first that you enter to check whether or not ASDM is installed on the ASA?
- Which two features does Cisco Security Manager provide?
- Your company is replacing a high-availability pair of Cisco ASA 5550 firewalls with the newer Cisco ASA 5555X models. Due to budget constraints, one Cisco ASA 5550 will be replaced at a time. Can 5550 and 5555x firewall be setup in failover mode?
- Which kind of Layer 2 attack targets the STP root bridge election process and allows an attacker to control the flow of traffic?
- A switch is being configured at a new location that uses statically assigned IP addresses. Which will feature ensure that ARP inspection works as expected?
- At which level does firewall severity level will debugs appear on a Cisco ASA?
- A network printer has a DHCP server service that cannot be disabled. How can a layer 2 switch be configured to prevent the printer from causing network issues?
- You have installed a web server on a private network. Which type of NAT must you implement to enable access to the web server for public Internet users?
- What happens when violation mode is set to Shutdown?
- Which ISE feature is used to facilitate a BY0D deployment?
- Which RADIUS attribute is used primarily to differentiate an IEEE 802.1x request from a Cisco MAB request?
- After an endpoint has completed authentication with MAB, a security violation is triggered because a different MAC address was is detected. Which host mode must be active on the port?
- Which CLI command is used to register a Cisco FirePOWER sensor to Firepower Management Center?
- What is penetration attack?
- What are stateful inspection firewalls?
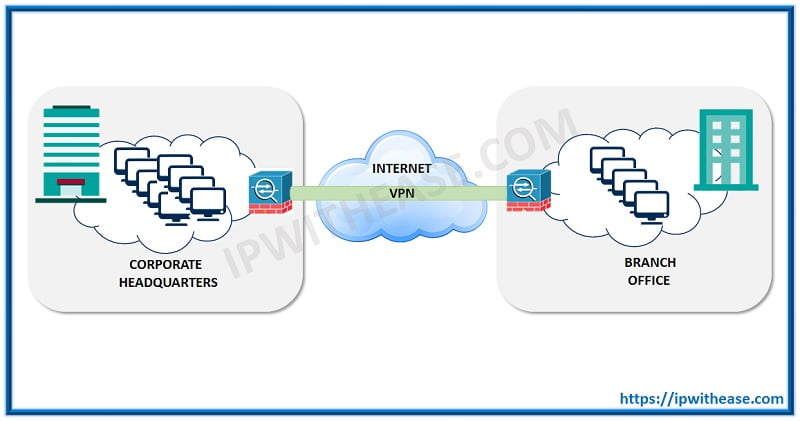
- What is Site-to-Site VPN?
- What is Remote-Access VPN?
- What is Signature Based Detection?
- Which Switchport security violation occurs if it comes to MAC address?
- What is Half Open TCP Connection?
- Which VPN would be established in below mentioned diagram?

- What happens when violation mode is set to protect?
- What is EtherType ACL?
- What are Time-based ACLs?
- What are the two different type of time restrictions in time-based ACLs?
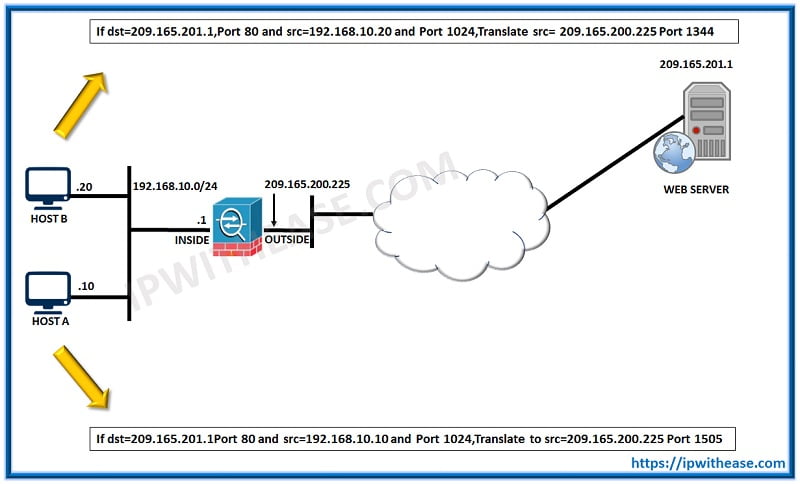
- Which NAT/PAT type example is implemented in below diagram?

- What NAT/PAT type example is implemented in below diagram?

- Explain Anomaly-based Intrusion Detection System?
- Which devices can be managed by Cisco Security Manager?
- What are the two modes in which Cisco ASA Firewall can be configured?
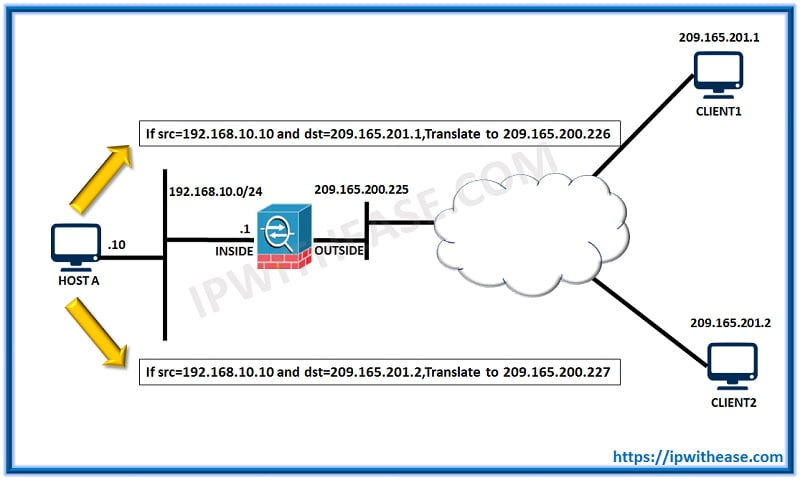
- In what scenario would you configure twice NAT?
- Which command can you use to verify access-list implemented on all interfaces in Cisco ASA?
- What can be configured to mitigate ARP poisoning attacks?
- The Cisco ASA 5500-X Series Next-Generation Firewalls provide four main remote access protocols to access the adaptive security appliance management functions. Name them?
- What does AAA stands for?
- Define the usage and purpose of AAA?
- What are Security Contexts in ASA?
- What is the System Execution Space in ASA when it comes to multiple contexts?
- Which command enables the multiple-context mode on the Cisco ASA?
- What is the difference between Site-to-Site VPN and Remote-Access VPN?
ANSWERS @https://ipwithease.com/shop/
Check our new website https://networkinterview.com For Free Video Courses, TechBlog, Mindmaps, Cheatsheets and much more.
Related – Top CCNP R&S Interview Questions
ABOUT THE AUTHOR

Founder of AAR TECHNOSOLUTIONS, Rashmi is an evangelist for IT and technology. With more than 12 years in the IT ecosystem, she has been supporting multi domain functions across IT & consultancy services, in addition to Technical content making.
You can learn more about her on her linkedin profile – Rashmi Bhardwaj

 ANSWERS @
ANSWERS @