Table of Contents
Modern day IT infrastructure and applications rely heavily on cloud services for its working. Security is of paramount importance for cloud ecosystems and applications hosted on them. Continuous security posture assessments of infrastructure and web applications are equally important to ascertain that they are secure and provide adequate protection to organization data hosted or managed by them along with upbeat performance to support business objectives.
In today’s article we understand the key differences between Web application security tool and web application firewall, their purposes and uses.
Web Application Security Tool (WAS)
Web application security process ensures protection of websites and online services against security threats which exploit vulnerabilities in application code. Common targets of web application attacks are SaaS applications. The web applications become a lucrative target for attacks due to:
- Complexity in source code increases likelihood of unattended or never discovered vulnerabilities or manipulation of malicious code
- Attacks can be easily automated and launched indiscriminately against a large scale
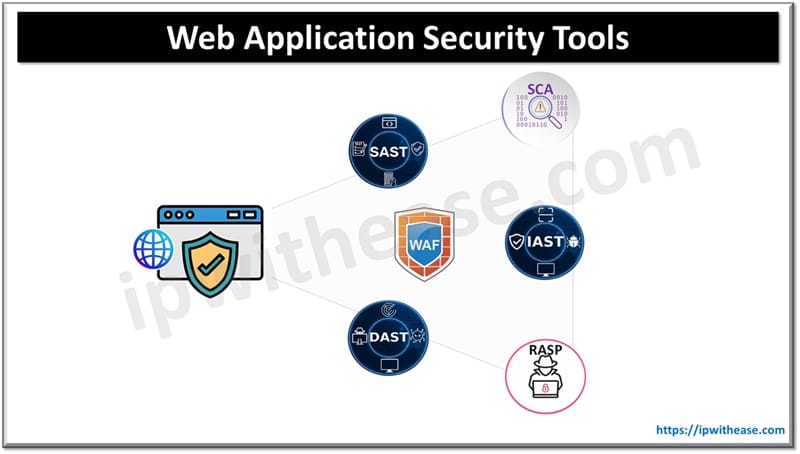
Web application security tools discover vulnerabilities in web applications and analyze various attack scenarios and software components for weaknesses which could lead to potential exploitation by malicious actors. Some commonly used and popular web application security tools are Burp suite, Sqlmap, W3af, OWASP zap, SonarQube etc.
Web Application Firewall (WAF)
Web application firewalls (WAF) are software-based filtering solutions used for protection of cloud resources from security threats. The WAF examines incoming traffic from the internet and blocks attempts of attacks. WAF secure data from manipulation and theft. WAF do not make any changes in application configurations but they simply sit at the network entry/ edge point and act as a gateway to all incoming traffic, blocking malicious requests before they reach the web applications and compensate for any deficiencies in code sanitization.
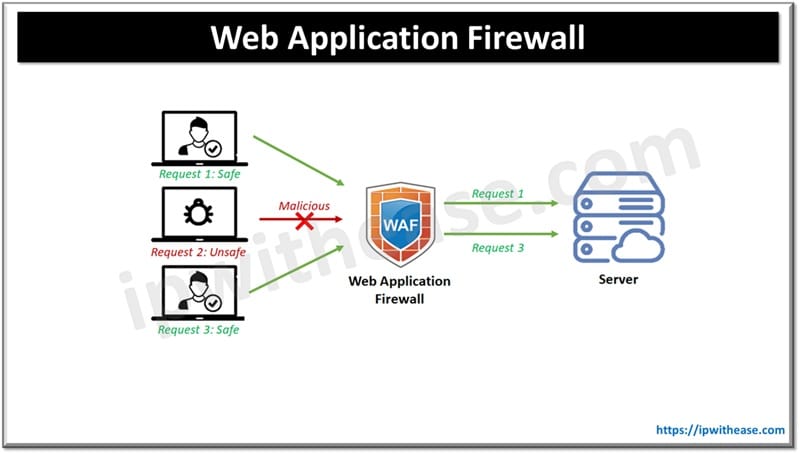
WAF uses heuristics to determine which traffic requires to be granted access to application or which needs to be kept out. WAF signatures and rules are constantly updated so as to enable them to identify bad actors and know attack vectors. WAFs are configurable for specific security policies and use cases to address emerging zero-day attacks. And typically integrated with other security solutions such as distributed denial of service (DDOS) to block high volume attacks.
Web Application Security Tool vs Web Application Firewall
Lets explore the differences between the two:
Definition
- Web application security tools are used to scan and identify vulnerabilities in web applications. These tools analyze various attack scenarios and software components weaknesses in the system which can be exploited by bad actors.
- Web application firewalls protect web applications from a variety of application layer security attacks such as cross site scripting (XSS), SQL injection, Cookie poisoning, automated bot attacks etc.
Working
- Web application security tools could be web based / URL based tools or license-based tools. There could be Web application tools to perform static application security testing (SAST) or white box testing, Dynamic application security testing (DAST) or black box testing, software composition analysis (SCA) , database security scans etc.
- WAF filters, monitors and blocks malicious HTTP/S traffic going to hit web application and prevent unauthorized data leaving the web application.
Layered Defense
- Web application tool operated at layer 7 of OSI.
- WAF operate at layer 7 (application layer).
Deployment
- Web application tools can be web based / URL based tools.
- WAFs are deployed behind the load balancer.
Architecture
- Web application tools like any other applications have three tier architecture – presentation, application and database layer.
- WAF works on signature, anomaly based and heuristics-based intrusion system.
Tools
- WAS Tools – Burp suite, Sqlmap, W3af, OWASP zap, SonarQube.
- WAF Tools – Azure WAF, AWS WAF
WAS vs WAF: Comparison Table
Below table summarizes the difference between the two:
| Feature | Web Application Security Tool | Web Application Firewall (WAF) |
| Purpose | Identifies vulnerabilities and security weaknesses in web applications | Protects web applications from threats in real time |
| Functionality | Scans for security flaws, misconfigurations, and coding vulnerabilities | Filters, monitors, and blocks malicious traffic based on security rules |
| Prevention vs Detection | Focuses on detection and prevention by identifying security risks before exploitation | Primarily focuses on prevention by blocking attacks as they occur |
| Deployment | Installed as software or cloud-based scanning service | Implemented as hardware, software, or cloud-based firewall |
| Protection Against | SQL injection, XSS, CSRF, insecure authentication, and other coding vulnerabilities | SQL injection, XSS, DDoS, zero-day exploits, and malicious traffic |
| Real-Time Protection | No, primarily used for testing and assessments | Yes, actively blocks threats in real-time |
| Common Examples | OWASP ZAP, Burp Suite, Acunetix, Nessus | AWS WAF, Cloudflare WAF, Imperva WAF, F5 BIG-IP ASM |
| Usage | Used by security teams and developers for vulnerability assessments | Used by IT and security teams to enforce security policies and prevent attacks |
| Compliance Support | Helps in identifying compliance issues | Helps in meeting security compliance (e.g., PCI DSS, GDPR) |
| Limitations | Does not actively block threats; only reports vulnerabilities | May not detect business logic flaws or internal vulnerabilities |
Download the comparison table: WAS vs WAF
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj