Table of Contents:
Organizations are confronted with the daunting task of safeguarding their digital assets in opposition to an array of potential threats. One essential element of this protection strategy is penetration trying out.
Let’s delve into the fundamentals of penetration checking out, losing light on its worth, and why it’s a quintessential device inside the cybersecurity arsenal.
Defining Penetration Testing
What is Penetration Testing?
Penetration checking out, regularly abbreviated as pen checking out, is a proactive cybersecurity exercise designed to assess the safety of a system, community, or software.
It includes simulated cyber-attacks to identify vulnerabilities and weaknesses that malicious actors should make the most of.
The Purpose of Penetration Testing
The primary objective of penetration testing, or ‘pen test’, is not just to uncover security flaws before they are exploited by cybercriminals, but also to simulate potential attack scenarios against IT infrastructure and web applications. This simulation aims to determine the depth at which an attacker could penetrate a system and the extent of potential damage to a business.
By mimicking real-world attack scenarios, organizations can rigorously evaluate their defenses, identify vulnerabilities, and take proactive measures to mitigate potential risks. A pen test trial allows for a comprehensive assessment of the current information security risks, providing invaluable insights into the effectiveness of existing security measures.
Through this process, organizations can pinpoint weaknesses in their security posture, enabling them to make informed decisions about where to strengthen their defenses for optimal protection.
Types of Penetration Testing
Network Penetration Testing
Focused on figuring out vulnerabilities inside a network infrastructure, this type of trying assesses the security of servers, routers, and network additives. Its objective is to discover weaknesses that might be exploited to benefit unauthorized admission.
Web Application Penetration Testing
This shape of testing goals for web programs, evaluating their security posture. Penetration testers verify the application’s code, logic, and configurations to discover vulnerabilities that could result in records breaches or unauthorized entry.
Wireless Network Penetration Testing
As groups increasingly depend upon wireless networks, it becomes vital to assess their security. This penetration testing identifies vulnerabilities in Wi-Fi networks and different wireless communication channels.
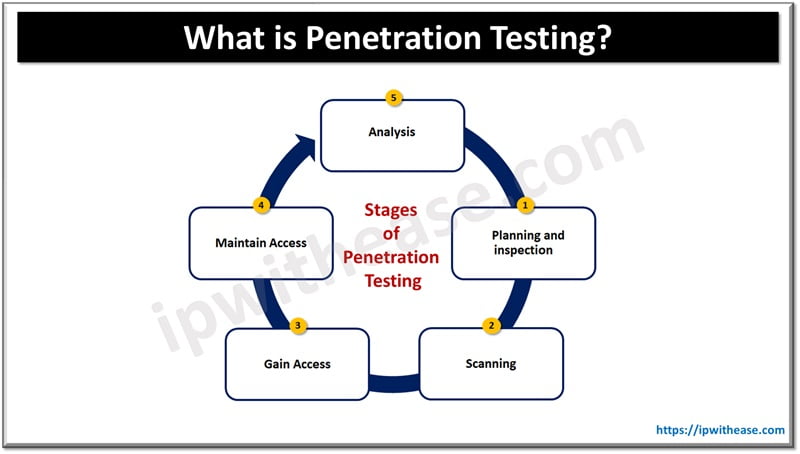
Elaborating on the Phases of the Penetration Testing Process
Thorough Planning and Comprehensive Reconnaissance
- Before starting up simulated cyber-attacks, a meticulous understanding of the target becomes paramount.
- This initial phase, Planning and Reconnaissance, includes systematically amassing information about the goal machine.
- This consists of an in-depth evaluation of its infrastructure and packages and identifying ability-vulnerable factors that might be exploited.
Strategic Scanning for Vulnerabilities
- Moving ahead inside the penetration trying out manner, the Scanning phase employs various equipment.
- Penetration testers meticulously scan the target, comparing open ports, offerings, and other capacity access points for attackers.
- This step is essential in figuring out vulnerabilities that are probably exploited at some point in the following ranges of the trying-out method.
Simulating Real Cyber Attacks – Gaining Access
- The penetration testing gaining access phase mirrors an actual cyber-assault state of affairs. Testers leverage their findings from the scanning section to strive for the exploitation of recognized vulnerabilities, looking for unauthorized entry.
- This step helps examine the energy of an enterprise’s defenses and provides insights into the capability impact of a successful breach.
Assessing Resilience – Maintaining Access
- Once access is obtained, the testing will not conclude; it evolves into the Maintaining Access phase.
- Testers assess the device’s resilience by attempting to maintain access consistently without detection.
- This stage simulates the tactics hired using continual attackers, enabling agencies to gauge their effectiveness in identifying and thwarting ongoing threats.
Thorough Analysis and Comprehensive Reporting
- The culminating segment of the penetration trying out manner involves Analysis and Reporting. Testers meticulously examine the results acquired during the checking out levels and compile a detailed record.
- This comprehensive report outlines the vulnerabilities uncovered and the capacity ramifications of exploitation and offers actionable hints for fortifying safety features.
- The insights won from this final phase empower corporations to make informed decisions and enhance their typical cybersecurity posture.
Comprehensive Advantages of Penetration Testing
Identifying Vulnerabilities Ahead of Cyber Threats
- One of the number one merits of penetration testing lies in its proactive approach to cybersecurity.
- By actively looking for and mitigating vulnerabilities, groups benefit from a strategic gain in decreasing the risk of falling prey to malicious cyber-assaults.
- Unlike conventional protection tests, penetration testing can unearth subtle weaknesses that might elude ordinary evaluations.
Compliance Adherence and Regulatory Alignment
- In the dynamic panorama of numerous industries, adherence to compliance and regulatory standards is non-negotiable.
- Numerous sectors and regulatory bodies mandate everyday protection tests to ensure the robustness of digital defenses.
- Penetration testing serves as a cornerstone in meeting those compulsory requirements, simultaneously elevating an organization’s security posture to new heights.
Heightened Incident Response Preparedness
- A frequently underestimated thing of penetration trying out is its position in refining incident reaction preparedness.
- Businesses can exceptional-track their incident reaction plans by comprehending the complex methods by which structures can be breached.
- This proactive method is instrumental in improving an agency’s capability to rapidly come across, respond to, and get over ability security incidents. It ensures a well-coordinated and decisive response to rising cyber threats.
Conclusion
In the ever-gift threat panorama of cybersecurity, penetration testing is an important protection mechanism. By actively searching for vulnerabilities, companies can enhance their virtual defenses, reduce the risk of breaches, and enhance typical cybersecurity resilience. As generation keeps improving, penetration checking stays paramount in the ongoing warfare against cyber threats.
Continue Reading:
What is PtaaS and How Does It Compare to Legacy Penetration Services?
Introduction to Zenmap (NMAP): Network Mapper
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.