Table of Contents
In today’s topic we will learn about Zscaler web security platform, Zscaler working, architecture and features.
The movement of IT landscape from closed door physical data centers to cloud ecosystems challenged security organizations to offer a more resilient, stronger and viable web security solution which can provide secure internet and application access.
As the cyberattacks become more and more sophisticated and hackers are deploying advanced techniques to steal data, organizations are also trying to adopt advanced tools and measures to stay ahead of bad actors. Modern day threat landscape can’t be managed with a traditional firewall sitting at the periphery and scanning and filtering all traffic incoming on the basis of IP addresses and ports.
What is Zscaler Web Security?
Organizations rely on Zscaler cloud-based web security platform to protect their organization networks and provides a unified platform for internet security, threat protection and web filtering. Multiplayer security measures are used to mitigate cyber threats in real time such as malware, phishing etc. Zscaler operates on the principle of zero trust which means ‘Never trust, always verify’. It creates a secure, cloud native environment which allows users to connect directly to applications to minimize risks and gain faster access to applications.
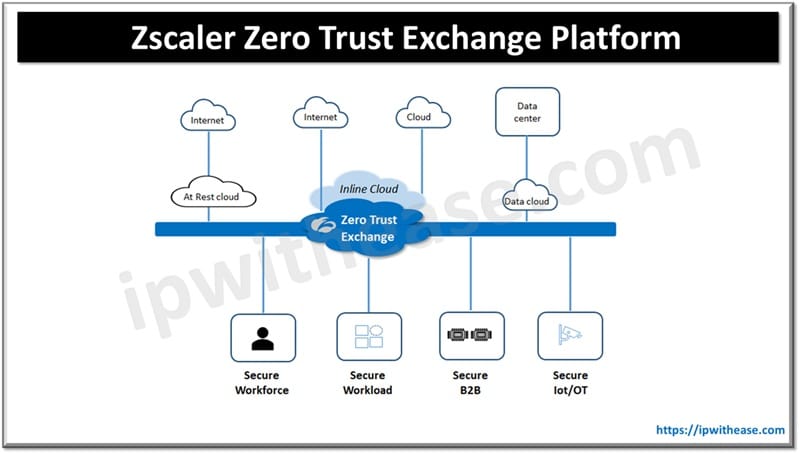
Organizations need to route user traffic to the Zscaler platform to prevent malware, advanced threats, browser exploits, phishing and malicious URLs and subnets. Zscaler web security is cloud native and meant for speed and scalability. It eliminates interruptions arising due to conventional application models, reduction in MPLS and network costs and security.
Unified cloud services include online security and cloud application management, sandbox, data leakage prevention, firewall and filtering. It also scans SSL data.
How does Zscaler security work?
It uses a four step process for risk management and gives protection for network, applications , users and devices.
- The platform has integration with third party providers for identity verification of who and what is accessing the system
- It identifies the connection destination such as website, SaaS application and private applications
- AI is used to assess risk-based factors such as user behaviour, posture of device, content and third-party intelligence
- Platform to enforce policy on per session basis and each connection is individually assessed against security policies in real-time
Zscaler Web Security Characteristics
- Latency reduction and speed up cloud services
- Traffic redirection to most reliable paths
- Reduction in load times with caching frequency
- Vital applications have necessary bandwidth
- Restrict and keep track of worker access to web sites with URL filtering
- Secure running of questionable files in sandbox environment in order to stop malware outbreaks
- Real time threat protection for new cyber threats
- Monitoring all incoming and outgoing web traffic in real-time to detect data breaches and security events
- Analyze encrypted traffic and stop the data theft
- Reporting and analytics capabilities to get insight into online security posture
Traditional Security vs Zscaler Web Security
| Parameter | Zscaler Web Security | Traditional Web Security |
|---|---|---|
| Deployment Model | Cloud-based (Security-as-a-Service) | On-premises (physical/virtual appliances) |
| Architecture | Distributed, cloud-native | Centralized, perimeter-based |
| Scalability | Easily scales globally via cloud infrastructure | Limited by hardware capacity |
| Remote Access | Native support for remote users | Requires VPN and backhauling |
| SSL/TLS Inspection | Cloud-based, scalable SSL inspection | Hardware-limited and resource-intensive |
| User Location Flexibility | Any location, any device | Best for users within the corporate network |
| Maintenance | Handled by Zscaler (automatic updates) | Requires manual updates and patching |
| CapEx/OpEx | Low CapEx, predictable OpEx (subscription-based) | High CapEx and OpEx (hardware, support, upgrades) |
| Security Model | Zero Trust, identity-aware | Trusts everything inside the perimeter |
| Threat Protection | Real-time cloud-based threat intelligence | Depends on local threat database and signatures |
| Latency | Low (uses nearest Zscaler node) | Potentially high due to traffic backhauling |
| Application Visibility | Deep visibility into cloud apps and web traffic | Limited visibility, especially for cloud apps |
| Deployment Time | Fast (days or weeks) | Slow (weeks or months depending on hardware) |
| Policy Management | Centralized, cloud-managed | Managed per appliance or location |
| Resilience / High Availability | Built-in redundancy in the cloud | Requires local HA setup (more cost and config) |
Download the comparison table: Traditional Security vs Zscaler Web Security
If you’re moving toward cloud apps like Office 365, Salesforce, or remote/hybrid work, Zscaler or similar SSE (Security Service Edge) platforms are much more efficient and modern.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj