Safeguarding digital communications has become paramount in the interconnected world with over 5.16 billion users. Amid this bustling online activity, conventional Internet Service Provider (ISP) assigned IP addresses need to be improved to meet the escalating demand. It’s within this context that the combination of PGP (Pretty Good Privacy) encryption and private proxies emerges as a robust strategy to enhance digital security and privacy.
The Power of PGP Encryption
PGP encryption, renowned for its formidable data protection capabilities, ensures the confidentiality and integrity of digital messages. By transforming plain text into complex code, only the intended recipients can decipher the content. This cryptographic method serves as a barrier against unauthorized access, thwarting any attempts by malicious actors to intercept sensitive conversations.
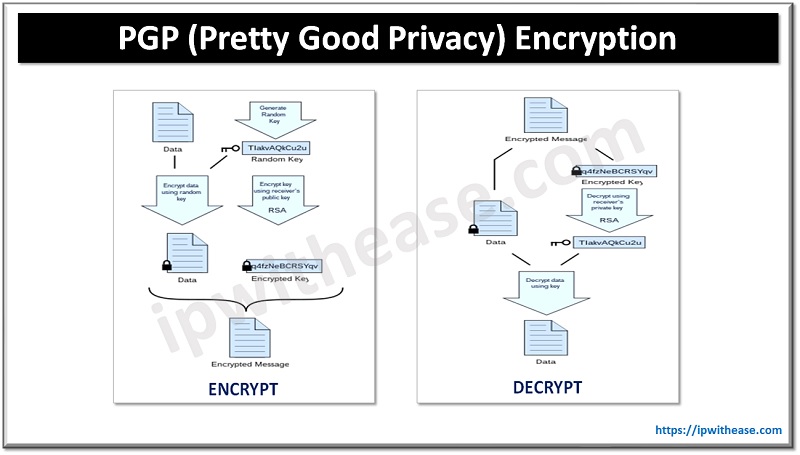
Amplifying Security with Private Proxies
These, on the other hand, are instrumental in masking users’ original IP addresses. By routing internet traffic through proxy servers, individuals and businesses can maintain online anonymity and prevent websites from tracking their digital footprints. This feature is precious in scenarios where anonymity is crucial, such as accessing restricted content or evading geolocation-based barriers.
The Convergence: PGP Encryption and the Proxies
A formidable shield against digital threats is forged when PGP encryption and these proxies unite. Here’s how this collaboration enhances digital security:
- Secure Communication Channels: PGP-encrypted messages transmitted through these channels offer a robust shield against unauthorized access. Such a method ensures that only the intended recipient, with the correct decryption key, can read the message. Even if someone manages to intercept the communication, the encryption renders the content indecipherable. Furthermore, hiding the sender’s IP address effectively reduces the chances of traceability. Consequently, not only is the message content protected, but there is also an added safeguard against potential identity compromise for both the sender and receiver.
- Evading Eavesdropping Attempts: Hackers and cybercriminals often attempt to intercept unencrypted communications. When these are integrated, the interception path becomes convoluted due to the involvement of proxy servers. This significantly reduces the likelihood of successful eavesdropping, preserving the confidentiality of messages.
- Enhanced Anonymity: Combining PGP encryption with these amplifies the cloak of anonymity. Encrypted messages, transmitted through proxy servers, become virtually untraceable to their senders. This synergy ensures that communicators’ content and identities remain shrouded in secrecy.
- Overcoming Geographical Barriers: Certain websites and platforms restrict access based on geographical location. PGP-encrypted messages transmitted through these proxies from different locations can bypass such barriers. This allows users to enjoy unfettered access to online content that might otherwise be inaccessible.
- Defending Against Cyber Threats: Malicious entities often target specific IP addresses for cyberattacks. Some providers that offer private proxies are NewIPNow, BrightData, and Webshare, which shield the original IP address from direct exposure, thus reducing the risk of targeted attacks. With PGP encryption layered atop, intercepted data remains unintelligible even if breached.
Conclusion: A Safer Approach to Digital Security
The amalgamation of PGP encryption and private proxies offers a holistic approach to digital security and privacy. Whether securing sensitive conversations, evading eavesdropping attempts, enhancing anonymity, overcoming geographical restrictions, or safeguarding against cyber threats, this dynamic duo proves its efficacy. By leveraging the strengths of encryption and proxies, individuals and organizations alike can navigate the digital landscape with increased confidence in their data protection and privacy measures
Continue Reading:
Zero Knowledge Proof Protocol: A Comprehensive Guide to ZKP
What Is Privacy Enhancing Technology? And How It Protects Your Data
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.