TTL security in BGP
While forming eBGP neighborship via Service provider network, there is security risk involved on probable attack from unsecured Internet Service provider domain to secured customer environment. A drawback to eBGP multihop is that by spoofing legitimate packets towards a BGP router at high volume a DOS attack may be accomplished.
Cisco has devised method to address the threat on BGP communication to meet clean communication between customer and provider BGP interlock.
By default the Cisco IOS send eBGP messages with a TTL value of 1.We can however modify this value using the eBGP multi-hop feature. If the TTL value of 1 is sent it requires the BGP neighbors to be directly connected else the neighbourship won’t be established.
Using eBGP multihop we can form neighbourship with peers at some hops away rather than being directly connected.
TTL-Security is a mechanism we use to protect our eBGP session against such DOS attacks. BGP TTL Security check can only be used with eBGP sessions and not with iBGP sessions.TTL Security and eBGP multihop are mutually exclusive and only one can be configured to form directly connected or multihop peering sessions.eBGP
Related- DOS vs DDOS Attack
We can configure the TTL-Security feature against an eBGP neighbor using a simple command:
BGP by default sends packets to external neighbours with a TTL of 1 and accepts packets from external neighbours with a TTL of 0 or higher (as measured after the local router has decremented the TTL of the incoming packet).
The TTL-Security changes the default behavior of originating by having BGP originate packets with a TTL of 255.
BGP Messages acceptance criteria in case TTL Security is configured:
TTL of the IP Packet should be greater than or equal to 255 – (Hop Count Configured)
Related – What is TTL?
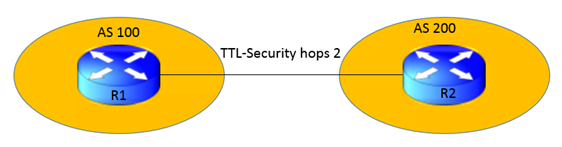
TOPOLOGY: TTL in Network Security
In this topology we will form neighborship over the R1 and R2’s loopback interface with ttl-security hop as 2.
R1 will accept only those packets from R2 that have the IP TTL value of 253 at least.
CONFIGURATIONS:
R1:
ip address 1.1.1.1 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.12.1 255.255.255.0
ip ospf 1 area 0
!
router bgp 100
bgp log-neighbor-changes
neighbor 2.2.2.2 remote-as 200
neighbor 2.2.2.2 ttl-security hops 2
neighbor 2.2.2.2 update-source Loopback0
ip address 2.2.2.2 255.255.255.255
ip ospf 1 area 0
!
interface FastEthernet0/0
ip address 9.9.12.2 255.255.255.0
ip ospf 1 area 0
!
router bgp 200
bgp log-neighbor-changes
neighbor 1.1.1.1 remote-as 100
neighbor 1.1.1.1 ttl-security hops 2
neighbor 1.1.1.1 update-source Loopback0
VERIFICATION:
We see the TTL value minimum required is 253 which is 255 (Hop-Count Configured)
R1# sh ip bgp neighbors 2.2.2.2
BGP version 4, remote router ID 2.2.2.2
BGP state = Established, up for 00:02:12
Last read 00:00:22, last write 00:00:19, hold time is 180, keepalive interval is 60 seconds
Neighbor sessions:
1 active, is not multisession capable (disabled)
Neighbor capabilities:
Route refresh: advertised and received(new)
Four-octets ASN Capability: advertised and received
Address family IPv4 Unicast: advertised and received
Enhanced Refresh Capability: advertised and received
Multisession Capability:
Stateful switchover support enabled: NO for session 1
Message statistics:
InQ depth is 0
OutQ depth is 0
Sent Rcvd
Opens: 1 1
Notifications: 0 0
Updates: 1 1
Keepalives: 3 3
Route Refresh: 0 0
Total: 5 5
Default minimum time between advertisement runs is 30 seconds
For address family: IPv4 Unicast
Session: 2.2.2.2
BGP table version 1, neighbor version 1/0
Output queue size : 0
Index 1, Advertise bit 0
1 update-group member
Slow-peer detection is disabled
Slow-peer split-update-group dynamic is disabled
Sent Rcvd
Prefix activity: —- —-
Prefixes Current: 0 0
Prefixes Total: 0 0
Implicit Withdraw: 0 0
Explicit Withdraw: 0 0
Used as bestpath: n/a 0
Used as multipath: n/a 0
Outbound Inbound
Local Policy Denied Prefixes: ——– ——-
Total: 0 0
Number of NLRIs in the update sent: max 0, min 0
Last detected as dynamic slow peer: never
Dynamic slow peer recovered: never
Refresh Epoch: 1
Last Sent Refresh Start-of-rib: never
Last Sent Refresh End-of-rib: never
Last Received Refresh Start-of-rib: never
Last Received Refresh End-of-rib: never
Sent Rcvd
Refresh activity: —- —-
Refresh Start-of-RIB 0 0
Refresh End-of-RIB 0 0
Address tracking is enabled, the RIB does have a route to 2.2.2.2
Connections established 1; dropped 0
Last reset never
External BGP neighbor may be up to 2 hops away.
Transport(tcp) path-mtu-discovery is enabled
Graceful-Restart is disabled
Connection state is ESTAB, I/O status: 1, unread input bytes: 0
Connection is ECN Disabled
Minimum incoming TTL 253, Outgoing TTL 255
Local host: 1.1.1.1, Local port: 179
Foreign host: 2.2.2.2, Foreign port: 22265
Connection tableid (VRF): Minimum incoming TTL 253, Outgoing TTL Enqueued packets for retransmit: 0, input: 0 mis-ordered: 0 (0 bytes)
Event Timers (current time is 0x3603C):
Timer Starts Wakeups Next
Retrans 4 0 0x0
TimeWait 0 0 0x0
AckHold 5 3 0x0
SendWnd 0 0 0x0
KeepAlive 0 0 0x0
GiveUp 0 0 0x0
PmtuAger 0 0 0x0
DeadWait 0 0 0x0
Linger 0 0 0x0
iss: 3246214154 snduna: 3246214292 sndnxt: 3246214292 sndwnd: 16247
irs: 1717271364 rcvnxt: 1717271502 rcvwnd: 16247 delrcvwnd: 137
SRTT: 125 ms, RTTO: 1414 ms, RTV: 1289 ms, KRTT: 0 ms
minRTT: 104 ms, maxRTT: 312 ms, ACK hold: 200 ms
Status Flags: passive open, gen tcbs
Option Flags: nagle, path mtu capable
Datagrams (max data segment is 1460 bytes):
Rcvd: 9 (out of order: 0), with data: 5, total data bytes: 137
Sent: 9 (retransmit: 0 fastretransmit: 0),with data: 5, total data bytes: 137
Related- BGP disable-connected-check
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.”
– Rashmi Bhardwaj (Author/Editor)