Google ADs
Beginning with ScreenOS 6.0.0 TACACS+ as an external authentication server for administration purposes is supported.
Below is this example scenario of TACACS server object where the TACACS server is called “AUTH“. The CLI commands required for this are as follows:
set auth-server “AUTH” id 1
set auth-server “AUTH” server-name “172.16.0.10”
set auth-server “AUTH” account-type admin
set auth-server “AUTH” type tacacs
set auth-server “AUTH” tacacs secret Screen05
set auth-server “AUTH” tacacs port 49
set auth-server “AUTH” server-name “172.16.0.10”
set auth-server “AUTH” account-type admin
set auth-server “AUTH” type tacacs
set auth-server “AUTH” tacacs secret Screen05
set auth-server “AUTH” tacacs port 49
The AUTH server will be configured as admin auth server as below –
set admin auth server “AUTH”
set admin auth remote root
set admin privilege get-external
set admin auth remote root
set admin privilege get-external
- Click Interface Configuration, and select TACACS+ (Cisco IOS)
- Add a new service called “netscreen”, and leave the protocol field blank
- Check both the user and group check box.
- Click Submit
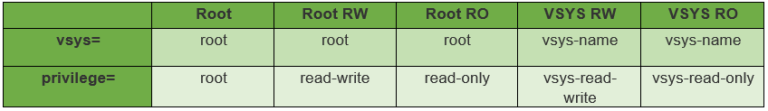
On the user configuration, scroll down to the bottom and select the netscreen (case sensitive) Custom attributes check boxes. Specify the attributes in the custom attributes field.The attributes that can be specified are as follows:
Google ADs
Related – TACACS VS TACACS+
Note: TACACS+ is not supported for use as an authentication server for xauth or policy authentication.
The verification and debug commands are –
-> get admin auth
-> get admin user login
debug admin all
debug auth all
-> get admin user login
debug admin all
debug auth all
ABOUT THE AUTHOR

Founder of AAR TECHNOSOLUTIONS, Rashmi is an evangelist for IT and technology. With more than 12 years in the IT ecosystem, she has been supporting multi domain functions across IT & consultancy services, in addition to Technical content making.
You can learn more about her on her linkedin profile – Rashmi Bhardwaj