Table of Contents
Introduction to Cymulate
The term “Cymulate” can be defined as a SaaS based breach & cyber-attack simulation platform. With “Cymulate” it is a very simple process to identify and optimize any security posture. ”Cymulate” also empowers organizations to safeguard their business critical assets.
The improved interface in “Cymulate” provides, with a few clicks, a technological challenge in all kinds of security controls by initiating thousands of attack simulations. Cymulate platform, has also the advantage to display on screen, the location of the user’s vulnerability and how to fix it in a few minutes.
Cymulate was initially created by an elite team of former IDF intelligence officers. The main reason for creation was the identification of malicious inefficiencies during their cyber security operations. Therefore IDF intelligence officers dedicated their services on how to empower organizations worldwide and make cyber security as simple as sending an email. Nowadays, Cymulate platform solutions are trusted by thousands of companies worldwide, including banks and financial services.
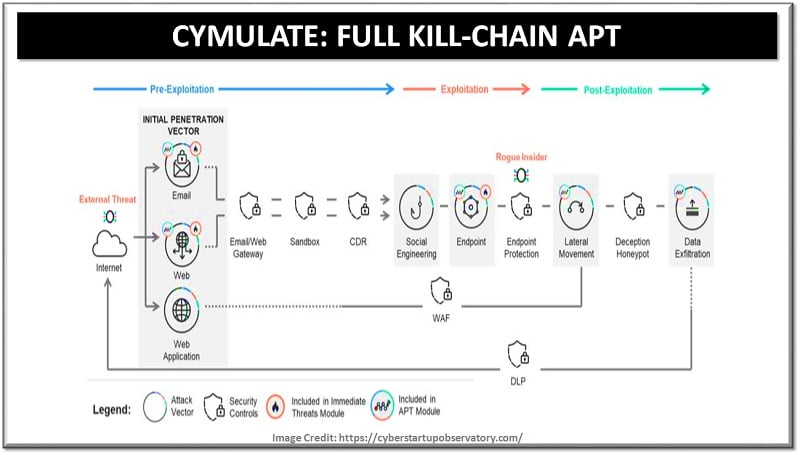
How Cymulate Works?
The main services that Cymulate’s Platform provides are described briefly below:
- Cyber Attacks Simulation: Cymulate platform tests how strong is customer security infrastructure, by simulating real cyber-attacks across all the vectors based on MITRE ATT&CK™. This technique provides a way you can protect yourself from threats before they ever show up.
- Evaluate Controls to Identify Gaps: Cymulate platform provides a “Cymulate Risk Score” and a clear report of the online details of your security posture. Cymulate platform also uses proven technologies, in order to evaluate advanced cyber risks such as NIST, CVSS V3, and DREAD.
- Remediate with Actionable Insights: Cymulate helps the organization staying one step ahead by embracing the cyber-attack strategy proactively. Cymulate platform provides you with direct instructions on how to reduce your area of attack, making it easier to prioritize which gaps to fill in first.
Advantages of Cymulate Platform Implementation
The main advantages in every day’s tasks inside an organization are presented below:
- Email Assessment: Many email filters, email getaways security and sandboxes are used without real security effects. Still the majority of cyber-attacks will originate via email. Poor configuration or setup implementation of security products might also lead to the false assumption that you are secure. Cumulate’s Email Assessment service enables organizations to challenge this significant cyber-attack vector and tests the results.
- Browsing Assessment: Another major advantage in the everyday working process of an organization is the legitimate browsing of streaming websites. Many malware is delivered through internet explorer add-ons. Also dangerous malicious scripts can use Flash, Java and Silverlight plugins. Cymulate’s Browsing Assessment platform is aware of the above threats, and enables assessment of outbound exposure using HTTP and HTTPS protocols.
- Web Application Firewall Assessment (WAF): Web applications are becoming the central business methodology for organizations. Therefore huge amounts of money and efforts are spent for protection. Although in the past, IT security teams tried to defend them, with a few number of enterprise web apps, now they must protect a large variation of web back ends of mobile apps, SaaS apps and other cloud based solutions. Cymulate Platform WAF helps to test your WAF configuration, implementation and services, ensuring that it is able to block payloads.
Conclusion
As we mentioned above, Cymulate platform was created by a special team of previous Israel Defense Forces intelligence officers and leading cyber engineers with world class experience and reputation in defensive cyber solutions.
The combination of operational expertise in cyber technology, with extensive field experience to simulate the latest and most sophisticated cyber-attacks, Cymulate Platform employs Software as a Service applications to simulate the thousands of tactics and strategies employed by hackers to attack network and endpoint security infrastructures.
Cymulate is helping organizations to prevent cyber attackers with a unique breach and attack simulation platform that empowers organizations with advanced security solutions made easy to protect their digital assets and maintain business targets.
With Cymulate, organizations can assess their true information to handle cyber security threats effectively. The future is now becoming more secure w.r.t people’s privacy and information.
Continue Reading:
Managed Detection and Response (MDR)
Managed Security Service Provider (MSSP)
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj