Unicast RPF or Unicast Reverse Path Forwarding –
Network administrators and can use Unicast Reverse Path Forwarding (aka Unicast RPF) to help limit the malicious traffic on an enterprise network. This security feature works by enabling a router to verify the reachability of the source address in packets being forwarded.
If the source IP address is not valid, the packet is discarded.
Related – Swithcport Block Unicast/Multicast
Below scenario will help understand how Unicast reverse forwarding blocks legitimate traffic due to asymmetric routing in network.
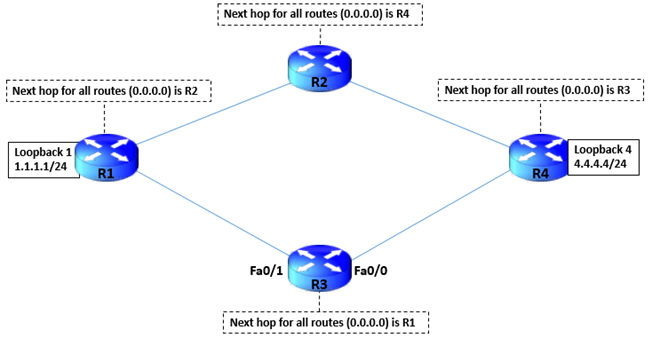
4 routers are connected to form a square in the below diagram.
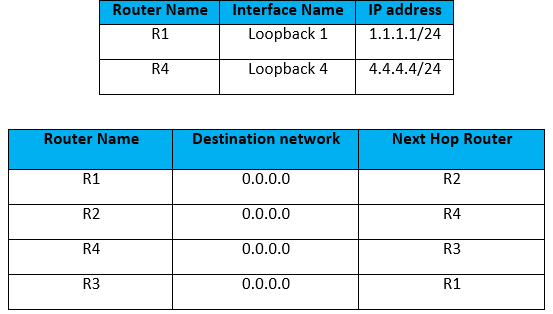
Below table detail how the Loopbacks of each Router is configured and default routes configured on each device. (Note – No routes are configured apart from the ones shown in the table) –
Below is a diagrammatic representation of connectivity to have more clear understanding –
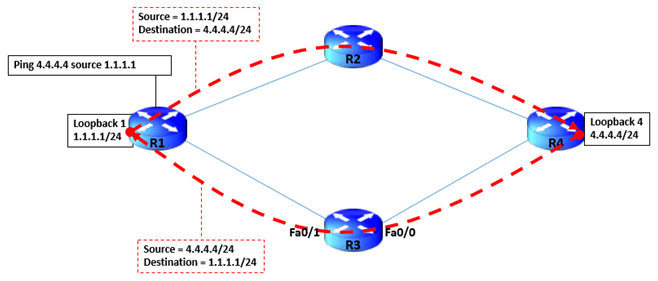
Now that all the Interfaces have been configured and routing in place , lets see how the traffic flow happens. A ping from Loopback of R1 (1.1.1.1/24) towards Loopback of R4 (4.4.4.4/24) takes the forward path R1->R2->R4 and then ICMP response back to R1 Loopback as R4-> R3 -> R1 which is clearly asymmetric routing.
Now, its time to implement unicast reverse path forwarding and to see its effect on asymmetric routing.
As shown below , an Access list “1” is configured to deny any traffic and to log the same.
Next, configure the unicast reverse path forwarding in Interface Fa0/0 of R3 and call the access list “1”. Once the configuration is done, we see that R1 starts receiving drops on ping packets sent from Source 1.1.1.1 towards destination 4.4.4.4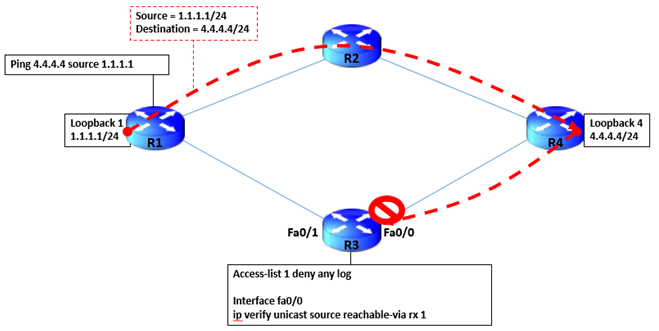
To diagnose the cause of ICMP “Request timed out”, we need to debug the IP packet. After entering the “Debug IP packet” command, logs start generating which show that traffic coming from Source 4.4.4.4 towards destination 1.1.1.1 have failed the RPF eligibility hence dropped.
This happens since the source packet i.e. 4.4.4.4 should be reachable via the same interface from where traffic is coming i.e. Fa0/0 of R3.
Since R3 default route points out towards R1 via interface fa0/1 (which also includes the route to 4.4.4.0/24 network), hence reverse path forwarding drops the packet – The incoming traffic interface and source route don’t have the same interface.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj