Table of Contents
Cybersecurity is a hot topic these days, with many cyberattacks targeting both organizations and individuals. One of the main attack vectors cybercriminals use is phishing. Phishing is a type of social engineering attack where criminals send malicious emails posing as a legitimate person or organization to extract sensitive information from their targets.
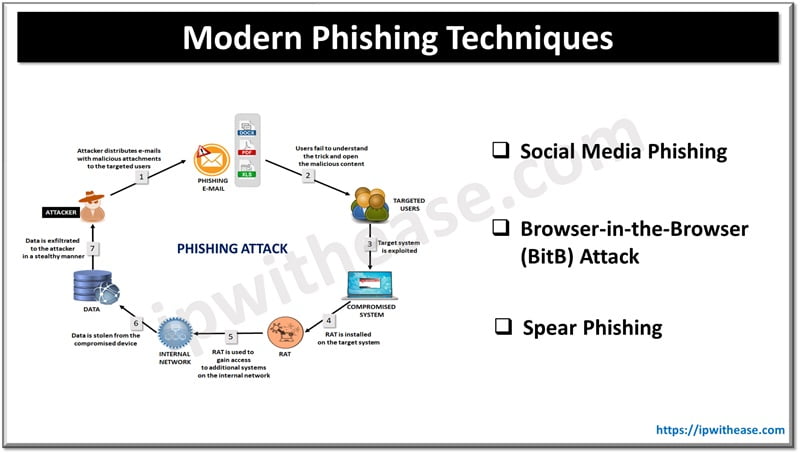
List of Modern Phishing Techniques
Phishing has evolved through the years, becoming increasingly sophisticated and hard to detect. Here are the main modern phishing techniques you should know how to recognize:
Social Media Phishing
While traditionally, most phishing campaigns have been executed via email, there’s been a recent surge in phishing through popular social media networks. Attackers create fake accounts on platforms like Instagram and Facebook, building them up to seem more legitimate over time. Then, they use these accounts to run their typical schemes.
One popular way attackers use social media phishing is by posing as investing gurus, typically in crypto and forex. They get fake followers and likes to appear legitimate and successful, making it easier for unsuspecting victims to fall for their promises. Treat any message request asking you to invest in a financial opportunity with skepticism, especially if it promises high returns with little to no risk.
Browser-in-the-Browser (BitB) Attack
Third-party logins are a convenient feature for users, allowing them to access various online services quickly using their existing social media or email accounts. Unfortunately, this login method has also resulted in the birth of a relatively new phishing method – Browser-in-the-Browser.
With this technique, cybercriminals fake the login pages of popular sites like Google, Facebook, or Microsoft. So, when you enter your login credentials, they will go directly to the criminal who created the fake login page.
One way to combat this threat is a password manager, which will check the authenticity of the URL you’re on and won’t let you use your credentials unless they’re legitimate. Whether you use iOS or Windows, password managers are available for you to benefit from. Other advantages of a password manager include the ability to generate strong passwords and store them securely and quickly.
Spear Phishing
Phishing is mainly associated with mass email campaigns targeting millions of users simultaneously. While this isn’t an untrue assessment, it overlooks another form of phishing that’s a bit scarier. Spear phishing is a more sophisticated attack where the cybercriminals target specific organizations, groups, and individuals. Reconnaissance is a big part of this attack, with the criminals spending days, if not months, researching their victim and polishing their approach.
This personalized approach makes it more difficult to spot the scam, as the attackers will typically know information about you that isn’t readily available.
How to Protect Yourself?
At the end of the day, all phishing scams are the same. While the way they’re executed can vary, the fundamental characteristics stay the same:
- Unusual sense of urgency
- Attempts to invoke panic in victims, causing them to act rashly
- Spelling or grammar mistakes
- Requests for sensitive information that isn’t typically disclosed via phone or email
- URLs that don’t match the legitimate site they claim to represent
- Imitation of legitimate logos and branding to appear authentic
Remembering and recognizing these signs will prevent 99% of phishing attempts. Another crucial step is enabling Two-Factor Authentication (2FA) for all your main accounts. This way, even if hackers obtain your login credentials, they won’t be able to access your accounts without confirming their identity.
Using a VPN to Prevent Phishing
A Virtual Private Network (VPN) is an effective tool in your cybersecurity arsenal to prevent phishing. It provides an extra layer of security by encrypting your internet connection and masking your IP address. This makes it harder for cybercriminals to track your online activities or target you with tailored phishing attempts based on your location or browsing history.
Additionally, some VPN services offer built-in security features such as phishing filters and malicious site blocking, which can proactively warn you about and prevent access to known phishing websites.
Final Thoughts
Several new phishing scams have dominated the world of cybercrime in recent years. Hackers have discovered that humans are typically the weakest link and far easier to exploit than writing sophisticated malware code.
Keep in mind that these techniques are constantly evolving. The best defense is to stay updated on the latest threats and adjust your cybersecurity stance accordingly.
Continue Reading:
5-Step Ransomware Incident Response Plan
Top 5 Data Breaches in Cyber Security and Possible Preventative Measures
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.