Table of Contents
For organizations looking to improve their network security without breaking the bank, open-source Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) offer robust alternatives to commercial products. These tools help monitor network traffic, detect suspicious activity, and sometimes block malicious actions. This beginner’s guide will walk you through some of the most popular open-source IDS/IPS tools, how they work, and how you can use them to strengthen your cybersecurity posture.
What are IDS and IPS?
- Intrusion Detection Systems (IDS): Monitors network traffic for suspicious activity or known attack patterns and alerts administrators when a potential threat is detected. IDS is a passive system; it does not actively block or prevent threats.
- Intrusion Prevention Systems (IPS): Works similarly to IDS, but with the added capability of actively blocking or preventing detected threats. IPS is a proactive defense system that automatically responds to threats in real-time.
Related: IDS vs IPS vs Firewall
Why Use Open-Source IDS/IPS Tools?
- Cost-effective: Open-source tools are free to use, making them attractive for small businesses, startups, or individuals with limited budgets.
- Customizable: Because the source code is available, open-source IDS/IPS tools can be customized to fit specific organizational needs.
- Active Community Support: Many open-source projects have active communities that contribute to the development, documentation, and troubleshooting of the software.
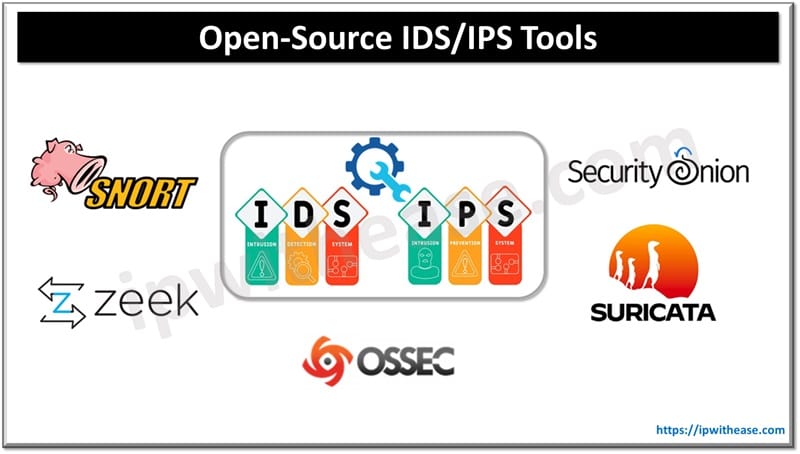
Popular Open-Source IDS/IPS Tools
1. Snort
Snort is one of the most widely-used open-source IDS/IPS tools. It operates based on signature-based detection, meaning it detects threats by comparing network traffic against a predefined set of rules or signatures.
- Features:
- Signature-based and protocol-aware traffic analysis.
- Real-time traffic monitoring and packet logging.
- Flexibility to act as either IDS (detection) or IPS (prevention).
- How to Use It:
- Install Snort on a Linux or Windows system and configure it to monitor network interfaces.
- Use predefined or custom rule sets to detect various attack types.
- Snort can be integrated with Security Information and Event Management (SIEM) tools for better alert management.
- Ideal For: Organizations looking for a highly customizable, signature-based detection system with an established reputation.
2. Suricata
Suricata is a high-performance IDS/IPS engine that supports multi-threading and is known for its efficiency in analyzing traffic. Like Snort, it uses signature-based detection but also incorporates anomaly-based detection.
- Features:
- Multi-threading support for higher performance and scalability.
- Supports deep packet inspection (DPI), HTTP, DNS, TLS, and more.
- Built-in support for IDS, IPS, and network security monitoring (NSM).
- How to Use It:
- Install Suricata on a Linux server and set it to monitor a specific network interface.
- Download and apply rule sets from the Emerging Threats open-source ruleset.
- Suricata can work in tandem with a visualization tool like Kibana to help analyze network traffic and alerts.
- Ideal For: Organizations that need scalability and high performance, particularly for monitoring large or high-traffic networks.
3. Zeek (formerly known as Bro)
Zeek is more than just an IDS. It operates as a network analysis framework that provides detailed insight into network traffic. Zeek excels at detecting anomalies rather than relying solely on signatures, making it ideal for advanced threat detection.
- Features:
- Network traffic analysis based on behavior rather than signatures.
- Extensive protocol analysis support, including HTTP, FTP, DNS, and SSL.
- Highly customizable through scripting, enabling tailored detection rules.
- How to Use It:
- Install Zeek on a Linux machine and configure it to monitor a network interface.
- Use Zeek’s built-in scripts or create custom scripts to detect and log suspicious activity.
- Zeek generates rich log files that provide detailed information on network events, which can be analyzed manually or fed into a SIEM.
- Ideal For: Advanced users who need detailed network monitoring, particularly in environments where zero-day threats and anomaly-based detection are a priority.
4. OSSEC
OSSEC is primarily a host-based IDS (HIDS) but also has network intrusion detection capabilities. It is designed to monitor and analyze log files, integrity checks, and system behavior to detect threats on individual hosts.
- Features:
- Log analysis, file integrity checking, rootkit detection, and real-time alerts.
- Supports integration with cloud environments and hybrid infrastructures.
- Cross-platform support (Linux, Windows, macOS).
- How to Use It:
- Install OSSEC on a server or endpoint to monitor file systems and logs for suspicious activity.
- Configure alerting rules to notify admins when a potential security event occurs.
- OSSEC can be integrated with third-party tools for centralized logging and monitoring.
- Ideal For: Organizations seeking host-level security with real-time monitoring and system integrity checks, especially in multi-platform environments.
5. Security Onion
Security Onion is a Linux distribution designed for IDS/IPS, network security monitoring, and log management. It integrates multiple tools, including Snort, Suricata, Zeek, and OSSEC, into a unified platform.
- Features:
- Full packet capture, intrusion detection, and network security monitoring.
- Pre-configured with tools like Kibana and ElasticSearch for data visualization and analysis.
- Integrated solution for detecting, investigating, and responding to security incidents.
- How to Use It:
- Install Security Onion as a standalone system or in a distributed deployment across multiple sensors.
- Use its pre-configured tools to monitor, detect, and analyze network traffic.
- Security Onion’s dashboard provides a centralized view for managing alerts and analyzing network events.
- Ideal For: Teams that need a comprehensive, all-in-one IDS/IPS and network security solution with built-in analysis and monitoring tools.
Steps to Get Started with Open-Source IDS/IPS Tools
- Identify Your Needs: Determine whether you need host-based detection, network-based detection, or a combination of both. Also, consider whether you need real-time blocking (IPS) or just detection (IDS).
- Choose a Tool: Based on your needs, choose an open-source IDS/IPS tool. For example, Snort and Suricata are great for real-time traffic monitoring, while Zeek excels at deep network analysis. OSSEC is ideal for host-based detection.
- Install and Configure: Install the selected tool on your network. Configuration typically involves setting up rules or policies to define what constitutes suspicious activity. Many tools come with predefined rules, but you can also customize them.
- Monitor and Analyze Alerts: Once deployed, monitor the alerts generated by the IDS/IPS. Use visualization and logging tools to track suspicious activities and respond to potential threats. This is where tools like Kibana (for log visualization) or SIEM integrations come into play.
- Regularly Update Rules: Keep your IDS/IPS tool’s rule sets up-to-date. Many open-source tools like Snort and Suricata rely on community-maintained rules, which are regularly updated to handle new threats.
Conclusion
Open-source IDS/IPS tools provide a flexible, cost-effective way to monitor and protect your network from cyberattacks. Whether you’re using Snort for signature-based detection, Zeek for network analysis, or Security Onion for a comprehensive solution, these tools can offer powerful protection without the financial burden of commercial products. By following this guide, you can start deploying open-source IDS/IPS in your environment, enhancing your organization’s overall security strategy.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj