Table of Contents
As businesses increasingly adopt cloud infrastructure, the role of Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) has become more critical. In traditional on-premises environments, IDS/IPS provide a clear line of defense against cyber threats, but the transition to the cloud introduces unique challenges. This blog post will delve into these challenges and provide solutions to enhance the effectiveness of IDS/IPS in cloud environments.
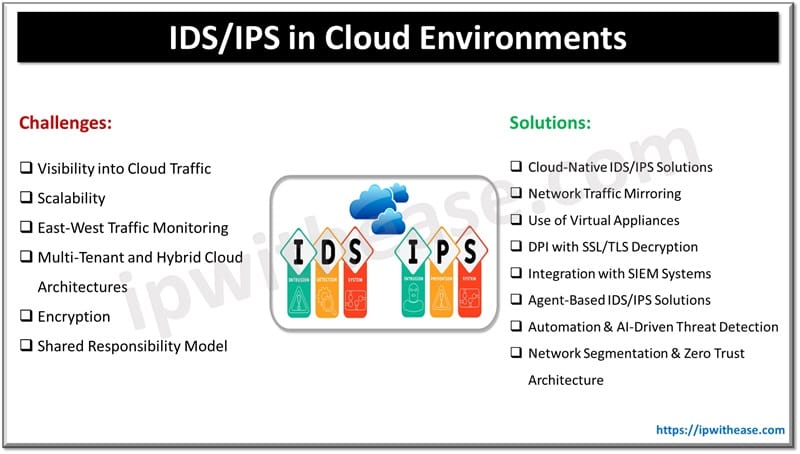
Key Challenges of IDS/IPS in Cloud Environments
Visibility into Cloud Traffic
- One of the primary challenges in cloud environments is the lack of visibility into network traffic. Unlike traditional networks where all traffic flows through a centralized point, cloud architectures are often distributed, with resources and services scattered across different regions and data centers.
- Additionally, encrypted traffic and virtual private clouds (VPCs) can further obscure network activity, making it difficult for IDS/IPS to detect and analyze malicious traffic.
Scalability
- Cloud environments are highly dynamic, with resources frequently scaled up or down based on demand. This makes it challenging for traditional IDS IPS systems, which are often deployed in static network locations. IDS IPS must scale in tandem with the cloud infrastructure to ensure consistent protection.
East-West Traffic Monitoring
- While traditional IDS IPS are good at monitoring north-south traffic (external traffic coming into the network), cloud environments often have significant east-west traffic (internal traffic between cloud services). Monitoring this internal communication is difficult, as much of it occurs within the cloud provider’s infrastructure.
Multi-Tenant and Hybrid Cloud Architectures
- Many organizations use a combination of public and private clouds (hybrid cloud) or operate in multi-tenant cloud environments. This adds complexity when it comes to deploying IDS IPS, as the security needs differ across environments, and it’s difficult to monitor traffic across various cloud providers.
Encryption
- Increasing use of encryption, both in transit (SSL/TLS) and at rest, is a significant challenge for IDS/IPS. Without the ability to inspect encrypted traffic, IDS IPS may miss sophisticated attacks embedded within encrypted communications.
Shared Responsibility Model
- In the cloud, security responsibilities are shared between the cloud provider and the customer. While cloud providers offer some built-in security measures, customers are still responsible for securing their applications and data. This division of responsibilities can lead to gaps in coverage if organizations assume the provider is handling all aspects of security.
Solutions to Enhance IDS/IPS in Cloud Environments
Cloud-Native IDS/IPS Solutions
- Many cloud providers now offer their own cloud-native IDS IPS solutions that are optimized for their infrastructure. Examples include AWS GuardDuty and Azure Security Center. These solutions are designed to integrate directly with the cloud provider’s services, providing better visibility and control over cloud traffic.
- Cloud-native IDS/IPS tools can scale dynamically with cloud workloads, ensuring continuous protection even as resources are added or removed.
Network Traffic Mirroring
- Cloud providers like AWS offer traffic mirroring services (e.g., AWS VPC Traffic Mirroring) that allow organizations to capture and inspect network traffic within the cloud. By mirroring traffic, organizations can send it to an IDS IPS for analysis without interrupting the flow of data.
- This solution is particularly useful for monitoring east-west traffic between cloud resources.
Use of Virtual Appliances
- Many traditional IDS/IPS vendors, such as Cisco, Palo Alto Networks, and Snort, offer virtual appliances that can be deployed in cloud environments. These virtual IDS IPS appliances provide similar functionality to on-premises solutions but are optimized for cloud infrastructure.
- Virtual appliances can monitor traffic between virtual machines, containers, and other cloud resources, helping to overcome some of the visibility challenges in cloud environments.
Deep Packet Inspection (DPI) with SSL/TLS Decryption
- To handle encrypted traffic, organizations can implement SSL/TLS decryption at key points within the cloud infrastructure. This allows the IDS/IPS to inspect decrypted traffic for signs of intrusion.
- Solutions like AWS Network Load Balancers or dedicated security appliances can perform SSL/TLS termination, enabling traffic inspection before it’s re-encrypted and sent to its destination.
Integration with Security Information and Event Management (SIEM) Systems
- A SIEM solution can aggregate data from various sources, including IDS/IPS, and correlate security events across the entire cloud infrastructure. This improves threat detection accuracy and reduces false positives.
- By integrating IDS/IPS with a SIEM, organizations can gain better visibility into threats and streamline incident response processes.
Agent-Based IDS/IPS Solutions
- Some IDS/IPS vendors offer agent-based solutions that can be deployed directly on cloud workloads (e.g., virtual machines, containers). These agents monitor activity on individual workloads, providing granular visibility into what’s happening within the cloud environment.
- Agent-based IDS/IPS can detect malicious activity on specific resources and provide detailed forensic data for threat analysis.
Automation and AI-Driven Threat Detection
- Modern IDS/IPS systems leverage machine learning (ML) and artificial intelligence (AI) to improve threat detection capabilities. In cloud environments, AI-driven systems can adapt to new threats faster by analyzing vast amounts of data and identifying patterns that traditional systems might miss.
- Automation also enables rapid scaling of IDS/IPS systems in response to changes in the cloud environment, ensuring that security keeps pace with demand.
Network Segmentation and Zero Trust Architecture
- Implementing network segmentation in cloud environments can help reduce the attack surface. By isolating critical resources and restricting communication between different segments, organizations can limit the spread of an intrusion and reduce the amount of traffic IDS/IPS need to monitor.
- Zero Trust architecture, which assumes no implicit trust between services, can further enhance cloud security by requiring continuous authentication and validation of all traffic.
Conclusion
Deploying IDS/IPS in cloud environments presents unique challenges, but these can be overcome by leveraging cloud-native solutions, virtual appliances, and advanced technologies like AI and machine learning. By implementing solutions such as traffic mirroring, SSL decryption, and SIEM integration, organizations can regain visibility and control over their cloud infrastructure while enhancing threat detection and prevention.
As the cloud landscape continues to evolve, IDS/IPS systems must adapt to new attack vectors and growing complexities. Proactive strategies, combined with ongoing monitoring and tuning, are essential to ensuring cloud environments remain secure from both known and emerging threats.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj