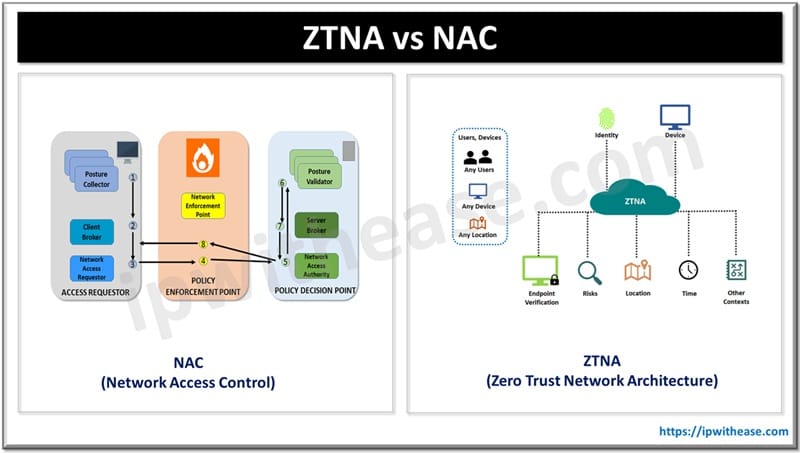
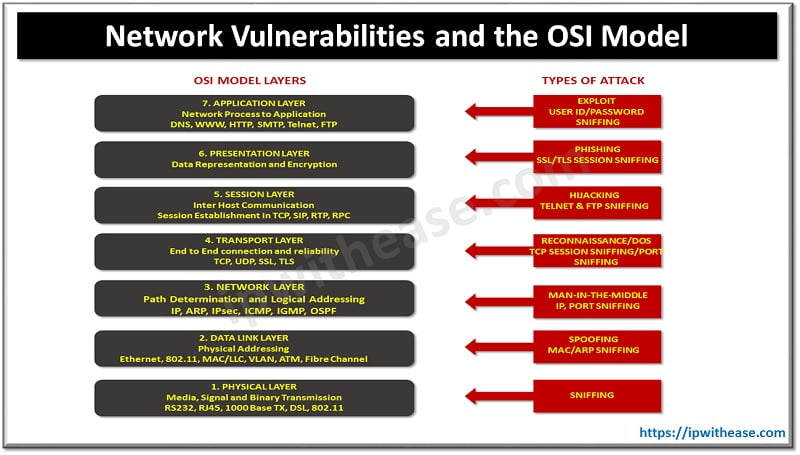
Table of Contents
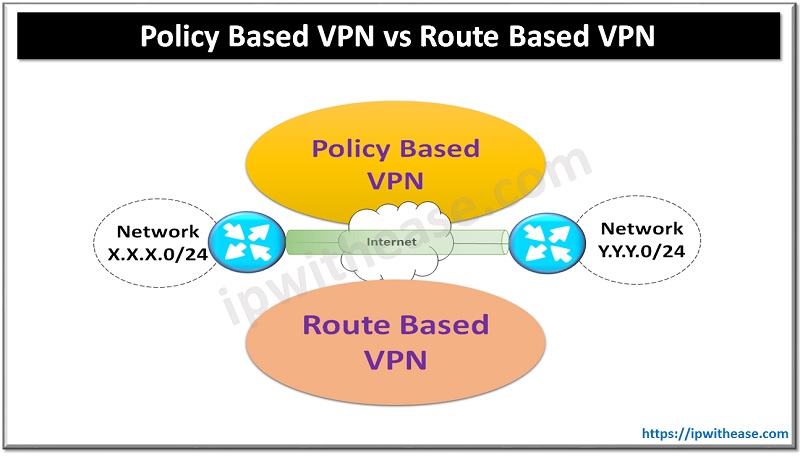
The main difference between Policy-Based VPN and Route-Based VPN lies in how traffic is selected and routed through the VPN tunnel. Policy-Based VPN is best for simple set up and Route-Based VPN is for complex topologies.
Policy-based is like giving a specific person a ticket to enter a gate. Route-based is like opening a road and letting any approved vehicle drive based on GPS routing.
While planning for VPN setup, it is imperative to have an understanding of differences between 2 VPN types – Policy based VPN and Route based VPN.
Just a brush-up on both VPN types and then we can detail how both terms differ from each other.
Policy based VPN
Policy based VPNs encrypt a subsection of traffic flowing through an interface as per configured policy in the access list. The policy dictates either some or all of the interesting traffic should traverse via VPN.
Route based VPN
In distinction to a Policy-based VPN, a Route-based VPN works on routed tunnel interfaces as the endpoints of the virtual network. All traffic passing through a tunnel interface is placed into the VPN. Rather than relying on an explicit policy to dictate which traffic enters the VPN, static and/or dynamic IP routes are formed to direct the desired traffic through the VPN tunnel interface.
Related – Top 100 VPN Interview Questions
Comparison: Policy Based VPN vs Route Based VPN
Differences
The key differences between Policy based VPN and Route based VPN are:
| PARAMETER | POLICY-BASED VPN | ROUTE-BASED VPN |
|---|---|---|
| Terminology | Policy-based VPNs encrypt and encapsulate a subset of traffic flowing through an interface according to a defined policy (an access list). | A route based VPN creates a virtual IPSec interface, and whatever traffic hits that interface is encrypted and decrypted according to the phase 1 and phase 2 IPSec settings. |
| Scalability | Numbers of VPN tunnels are limited by the number of policies specified | Numbers of VPN tunnels are limited to either route entries or number of tunnel interface specified which are supported by the device. |
| Dynamic Routing support | The exchange of dynamic routing information is not supported in policy-based VPNs. | Supports dynamic routing over the tunnel interface. |
| Policy Control | “Deny” of traffic flowing through the VPN tunnel can’t be configured. | “Deny” of traffic flowing through the VPN tunnel can’t be configured. |
| Network topology | Supports P2P network topology while Hub and Spoke topology is not supported | Supports Hub-spoke , P2P and P2MP network topologies |
| Security Association status | Forms SAs in response to interesting traffic matching policy (and will eventually tear down the SAs in the absence of such traffic). | The SAs for a route-based VPN are always maintained, till corresponding tunnel interface is up |
| Use case | Common reasons to use a Policy-based VPN: ·The remote VPN device is a non-Juniper device ·Need to access only one subnet or one network at the remote site, across the VPN. | Common Reasons to use a Route-based VPN: ·Source or Destination NAT (NAT-Src, NAT-Dst) needs to occur while it traverses the VPN. ·Overlapping Subnets/IP Addresses between the two LANs. ·Hub-and-spoke VPN topology. ·Design requires Primary and Backup VPN. ·A Dynamic Routing Protocol (that is OSPF, RIP, BGP) is running across the VPN. ·Need to access multiple subnets or networks at the remote site, across the VPN. |
| NATting of VPN traffic | Traffic flowing through the VPN tunnel can’t be NATTed | Traffic flowing through the VPN tunnel can be NATTed since it passes through either the tunnel interface or gateway IP address specified as next-hop in routing. |
| Remote Access VPN | Remote access VPN can be implemented with policy based VPN. | Remote access VPN can’t be implemented with Route based VPN |
| Vendor Agnostic | Policy based VPN might be supported by the vendors which doesn’t support the route based VPN | Route based VPN might not be supported by all the vender’s devices |
| Addition of new network | Tunnel policies are to be configured if there is added a new IP networks | Routing is to be configured for new network if there is static Route to remote location |
Related – Site to Site VPN vs Remote Access VPN
Similarities
- Encryption with IPsec: Both use IPsec (Internet Protocol Security) to encrypt and secure data traffic.
- Support for Site-to-Site VPNs: Both can be used to create site-to-site VPN tunnels connecting different networks over the internet.
- IKE Protocol Usage: Both use IKE (Internet Key Exchange) for negotiating security associations and handling key exchanges.
- Secure Data Transmission: Both provide confidentiality, integrity, and authentication for data sent across untrusted networks.
- Interoperability: Both can interoperate with standard IPsec-compliant devices and vendors.
- Tunnel Establishment: Both involve creating a logical tunnel between endpoints for protected communication.
- Firewall Integration: Both types can be implemented on firewalls, routers, or security appliances.
- Use of Security Associations (SAs): Both rely on Security Associations to define how traffic is encrypted and decrypted.
Frequently Asked Questions (FAQs)
Q.1 Do I have to set up my VPN manually?
Most VPN apps offer automatic installation, making the setup process quick and easy. You don’t usually have to configure the VPN manually.
Q.2 What is the best VPN?
The best VPN for you depends on your specific needs and requirements. Factors to consider include privacy features, server locations, connection speed, and customer support. Conduct thorough research and read reviews to find the VPN that suits you best.
Q.3 Will I have to pay for a VPN?
While there are free VPNs available, they often come with limitations and may not provide the same level of security and privacy as paid VPN services. Paid VPNs generally offer more reliable and faster connections, as well as better customer support. However, most VPN services are affordable and can range from $10 to $13 per month, depending on the subscription plan.
Q.4 Why is my internet slower after setting up my VPN?
When using a VPN, your internet speed may be slightly slower due to the encryption and routing processes. The added layer of security and privacy provided by the VPN outweighs the minor decrease in speed.
Q.5 Should I get a dedicated IP address add-on?
Depending on your usage, a dedicated IP address add-on may be beneficial. It provides you with a unique IP address that is not shared with other VPN users, reducing the risk of being affected by actions of other users. This add-on is particularly useful for business purposes.
Q.6 What can I access with a VPN?
VPNs allow you to access geographically restricted content and bypass government censorship. You can use a VPN to access region-locked websites, streaming services, and other online content that may not be available in your location.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj