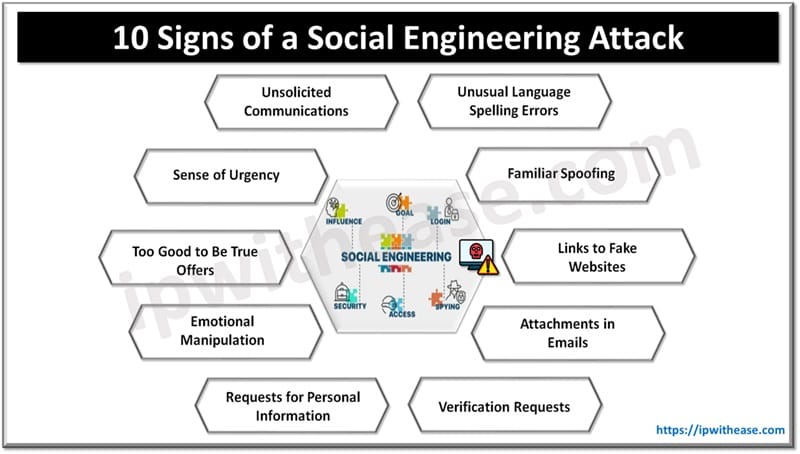
Table of Contents
ACL can be used to Mitigate IP Address Spoofing by configuring ACLs to deny traffic with source IPs that don’t match the expected internal network ranges. This blog elaborates the step by step process to mitigate IP spoofing attack using ACL.
What is Spoofing?
Spoofing is a practice used to gain unauthorized access to machines/server applications, whereby an attacker unlawfully imitates another machine by manipulating IP packets. Although IP address spoofing is not an attack, it is the starting point of many attacks prevalent in today’s networks.
Spoofing attack initiates from outside unsecured Internet and someone on the outside of the LAN network spoofs the company inside IP address to make it look like they are part of the inside of your network.
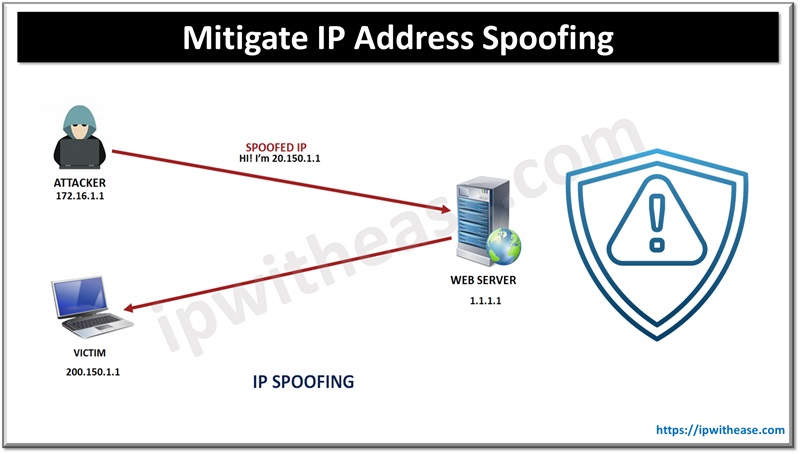
How to Mitigate IP Address Spoofing
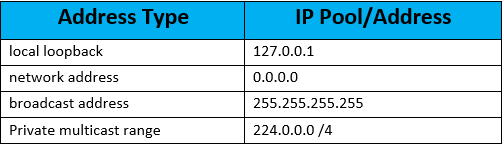
The key here is to deny RFC 1918 IP block that is coming into your network from the outside interface. In addition to RFC 1918 block of addresses, we also need to block any source coming from local loopback, Network, Broadcast address and multicast range –
RFC 1918 private address block is –
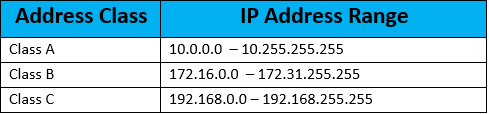
Other sources to block include –
Configuration to Mitigate IP Spoofing Attack
Step by step configuration to mitigate IP Spoofing attack is as below –
Step 1
Call RFC 1918 block in access list (here ACL is 101)
R1(config)# access-list 101 deny ip 10.0.0.0 0.255.255.255 any logR1(config)# access-list 101 deny ip 172.16.0.0 0.15.255.255 any log
R1(config)# access-list 101 deny ip 192.168.0.0 0.0.255.255 any logStep 2
Call other sources in access list (here ACL is 101)
R1(config)# access-list 101 deny ip 127.0.0.0 0.255.255.255 any logR1(config)# access-list 101 deny ip 0.0.0.0 0.255.255.255 any log
R1(config)# access-list 101 deny ip 224.0.0.0 15.255.255.255 any log
R1(config)# access-list 101 deny ip host 255.255.255.255 any log
R1(config)# access-list 101 permit ip any 192.168.5.0 0.0.0.255Traffic is permitted to the destination address 192.168.5.0 /24 which is LAN IP Address
Step 3
Apply ACL to outside Interface (Gi0/0 is outside/Internet Interface)
R1(config)# interface Gi0/0R1(config-if)# ip access-group 101 inNot only do we want to prevent people from the outside of our network ‘pretending’ they are inside our network, we also want to prevent our inside people from spoofing to a different IP address as well. The above configuration had a focus on traffic INBOUND to our network,
Below configuration will prevent outbound traffic from spoofing.
Step 4
The only range that is allowed to transmit is my internal network, in this case 192.168.5.0 /24
R1(config)# access-list 110 permit ip 192.168.5.0 0.0.0.255 anyR1(config)# access-list 110 deny ip any any logStep 5
Apply ACL to outside Interface (Gi0/0 is inside/secured Interface)
R1(config)# interface Gi0/1R1(config-if)# ip access-group 110 inRelated FAQs
1. What are the risks associated with IP address spoofing?
IP address spoofing poses significant security risks, as it can be used to conduct various types of attacks, including distributed denial of service (DDoS), session hijacking, and man-in-the-middle attacks. By masking their true identity, attackers can evade detection and launch attacks with greater anonymity.
2. How can I detect IP address spoofing?
Detecting IP address spoofing can be challenging, especially if sophisticated techniques are employed by attackers. However, some methods such as network traffic analysis, anomaly detection, and implementing ingress filtering at network borders can help in identifying spoofed packets.
3. Can IP address spoofing be used for legitimate purposes?
While IP address spoofing is predominantly associated with malicious activities, there are some legitimate use cases.
For example:
Nnetwork administrators may employ IP spoofing techniques for testing network defenses or conducting penetration testing with proper authorization and consent.
4. What measures can I take to prevent IP address spoofing?
Ingress Filtering: Implementing ingress filtering, which verifies the source IP address of incoming packets to ensure they originate from valid ranges, can help prevent IP address spoofing. A
Cryptographic Authentication: deploying cryptographic authentication mechanisms such as IPsec can enhance network security by validating the integrity and authenticity of communications.
Continue Reading
Difference b/w ACL on Router and Firewall
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj