Table of Contents
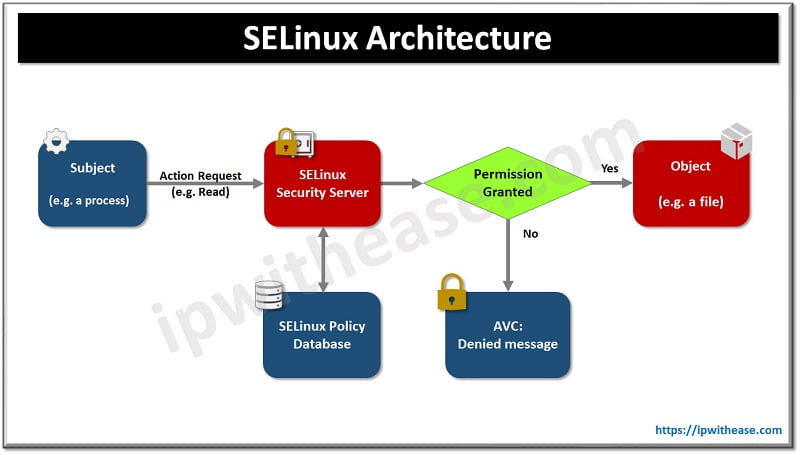
SELinux is a security architecture integrated into the 2.6.x kernel using Linux security modules (LSM). It is a project driven by the United States National Security Agency (NSA) and the SELinux community. SELinux offers a flexible mandatory access control (MAC) system built into the Linux kernel.
Running a MAC system protects the system from malicious or flawed applications which could be a potential threat to the system. SELinux defines access and transition rights of every user, application, processes, and file system.
In today’s lesson we will cover how to enable and disable SELinux permanently and temporarily, the reason for disabling SELinux, and the impact of disabling SELinux.
Enable / Disable SELinux
On some Linux distribution systems SELinux comes enabled by default. But sometimes not all applications support SELinux. Therefore, sometimes SELinux hampers execution of necessary processes or during installation of packages. In such cases it is advisable to turn off SELinux.
There are four different ways to stop or disable SELinux; we will learn about them in more detail in the upcoming section. The SELinux enforces security policies including mandatory access controls, every file and process will be tagged with specific labels which are used by SELinux. There are certain prerequisites which need to be met before disablement of SELinux.
Before disabling SELinux let’s look at command to check the status
You can use Setstatus command to verify the same
[root@localhost ~]# sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: enforcing
Mode from config file: enforcing
Policy MLS status: enabled
Policy deny_unknown status: allowed
Memory protection checking: actual (secure)
Max kernel policy version: 31
Prerequisites for disabling SELinux:
- Access to a user account with sudo privileges
- Access to a terminal/command line
- An RHEL-based system, such as CentOS 7
- A text editor, such as nano or vim
Method 1: Enable SELinux temporarily
To enable SELinux temporarily you can use setenforce command
Setenforce permissive command set SELinux status to permissive mode
setenforce enforcing command set SELinux status to enforcing mode
[root@localhost ~]# setenforce enforcing
[root@localhost ~]# sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: enforcing
Mode from config file: enforcing
Policy MLS status: enabled
Policy deny_unknown status: allowed
Memory protection checking: actual (secure)
Max kernel policy version: 31
Method 1: Disable SELinux temporarily
To disable SELinux temporarily modify SELinux/enforce file and reboot system for setting to take effect
#cat /selinux/enforce
1
#echo 0> /selinux/enforce
#cat /selinux/enforce
0
Or we can say # setenforce 0
Method 2: Enable SELinux permanently
To enable SELinux permanently you can use a configuration file. The configuration file is available in /etc/selinux path.
[root@localhost ~]# vi /etc/selinux/config
SELINUX=enforced
Press escape save and exit by using wq! And restart system using init 6 command
[root@localhost ~]# init 6
Or reboot system using reboot command
[root@localhost ~]# reboot
Method 2: Disable SELinux permanently
To disable SELinux permanently modify /etc/selinux/config and set the SELINUX= disabled
# cat /etc/selinux/config
SELINUX=disabled
SELINUXTYPE=targeted
SETLOCALDEFS=0
Possible values for SELinux variable in /etc/selinux/config file are
Enforcing – security policy is always enforced
Permissive – Simulation of enforcing policy by printing warning messages and not actually enforcing the SELinux.
Disabled – completely disable SELinux
There are 2 more additional methods to disable SELinux as described below
Method 3: Disable SELinux using Grub boot loader
You can pass disable parameter to Grub boot loader
# cat /boot/grub/grub.conf
default=0
timeout=5
splashimage=(hd0,0)/boot/grub/splash.xpm.gz
hiddenmenu
title Enterprise Linux Enterprise Linux Server (2.6.18-92.el5PAE)
root (hd0,0)
kernel /boot/vmlinuz-2.6.18-92.el5PAE ro root=LABEL=/ rhgb quiet selinux=0
initrd /boot/initrd-2.6.18-92.el5PAE.img
title Enterprise Linux Enterprise Linux Server (2.6.18-92.el5)
root (hd0,0)
kernel /boot/vmlinuz-2.6.18-92.el5 ro root=LABEL=/ rhgb quiet selinux=0
initrd /boot/initrd-2.6.18-92.el5.img
Method 4: Disable only a specific service in SELinux – HTTP/APACHE
If you do not wish to disable the whole SELinux then you can also disable it for specific service. For example, to disable SELinux for HTTP/Apache service modify the httpd_disable_trans variable in /etc/selinux/targeted/Booleans file
# grep httpd /etc/selinux/targeted/booleans
httpd_builtin_scripting=1
httpd_disable_trans=1
httpd_enable_cgi=1
httpd_enable_homedirs=1
httpd_ssi_exec=1
httpd_tty_comm=0
httpd_unified=1
Set SELinux boolean value using setsebool command
# setsebool httpd_disable_trans 1
# service httpd restart
Continue Reading:
How to Create a Permanent Bash alias on Linux/Unix?
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj