FTPS vs SFTP
While FTPS adds a layer to the FTP protocol, SFTP is a totally different terminology based on the SSH protocol (Secure Shell). Both are used in data file transfer. Let’s understand both the concepts in detail, benefits of each other and detailed comparison of their features / capabilities.
What is FTPS?
FTPS, also known as FTP-SSL, is secured form of FTP. FTPS is basically FTP with security added to data transfer. Special security protocols TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic and provide encryption of data to protect your information, including username/password.
FTPS is to FTP very much like HTTPS is to HTTP: an added layer of security while keeping the original protocol relatively unchanged.
How does FTPS work?
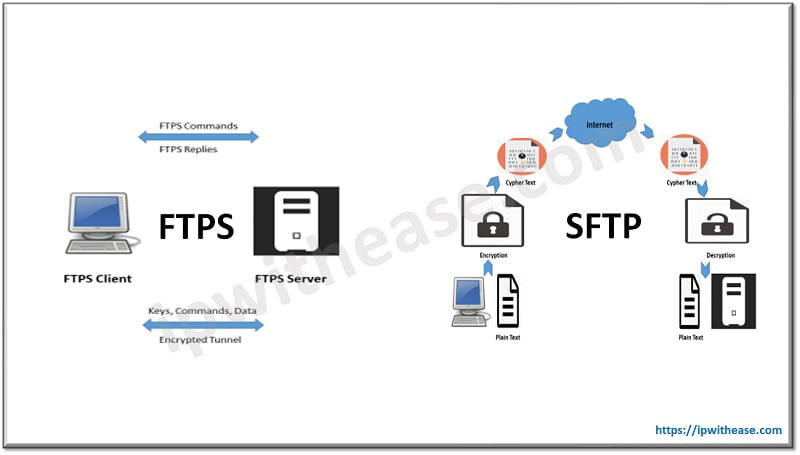
FTPS uses two connections – (1) a control channel and (2) a data channel. Either both channels will encrypt or only the data channel will perform encryption. FTPS authenticates your connection using a username and password, a trusted certificate or both. FTPS client will first check if the server’s certificate is trusted, if either the certificate was signed by a known certificate authority (CA) or if the certificate was self-signed by your partner and you have another copy of the public certificate in your trusted key store. If your certificate isn’t signed by a third-party CA, your partner may allow you to self-sign your certificate. Username authentication can be used with any combination of certificate and/or password authentication.
Pros of FTPS:
- Widely known and used.
- Communication is readable by humans.
- Provides services for server-to-server file transfer.
- SSL/TLS has good authentication mechanisms (X.509 certificate features).
- FTP and SSL/TLS support is built into many internet communications frameworks.
- FTPS is encrypted.
- Commonly understood and utilized.
- Easy to implement.
- Offers service for server to server file transfer based on SSL/TLS.
- Easily supported by mobile device.
- Works in OS that have FTP support but not SSH/SFTP client.
- Built in support in .net framework.
Cons of FTPS:
- Not all FTP servers support SSL/TLS.
- Does not have a standard way to get and change file or directory attributes.
- Can’t perform file system operations.
- Uses multiple ports, making firewall configuration more complicated.
Related – TFTP vs FTP
What is SFTP?
SFTP, also known as SSH FTP, encrypts both control and data during transmission. All data and credentials are encrypted as they pass through the internet. SSH is a protocol that allows you to remotely connect to other systems and execute commands from the command line. SFTP was created to transfer files through the secure channel (SSH). SFTP makes data transfers using the SFTP faster than other secure FTP connections.
How SFTP works?
SFTP provides two methods for authenticating connections like FTP with SFTP. Authentication method includes private and public key SSH keys. When request reaches the SFTP server, their client software will transmit public key to the server for authentication. If the public key matches the private key, along with username and password, then the authentication will be a success. Key points of SSH key authentication are:
- System generates a public-private key pair.
- You link your public key to your account on the SFTP server.
- When connection is established with the server, client will produce a signature with private key that the server can confirm with the already-stored public key.
- If the public and private keys match up, the connection is established.
Pros of SFTP:
- The connection is always secured.
- SFTP requires only one connection.
- Uses only one port, hence simple to configure firewall rules.
- SFTP is supported by Linux and Unix OS by default.
- Can perform the file system operation, file lock, permission and attribute, manipulation and symbolic link creation.
Cons of SFTP:
- SSH public and private keys are difficult to manage and validate.
- It is not human readable because of binary form.
- The protocol does not offer removal operations for the recursive directory in addition to a server-to-server copy.
- No integrated SSH/SFTP assistance in VCL and .net structure.
Comparison between FTPS and SFTP:
- FTPS establishes connection via SSL/TLS, while SFTPS establish connection via SSH channel.
- For both protocols, server authentication is via public key and Client authentication via username and password
- FTPS control channel is 990/TCP and FTPS data channel is 989/TCP. SFTP port number is 22.
- Both use the algorithm of Asymmetric, symmetric and key exchange.
- FTPS performs authentication via x.509 certificates and SFTP authentication takes place via SSH keys.
- FTPS will allow you to create custom commands and SFTP has better control of file permissions, ownership and properties.
- FTPS allows use of Trusted x.509 certificates, whereas SFTP server only requires a single port to be open on the firewall.
- FTPS supports EBCDIC transfers. SFTP allows creation of symbolic links.
- SFTP will be slower than FTPS because there are more steps to render security.
- FTPS has separate connections for command and file data transfer which is not the case of SFTP.
- Encrypted command and file data connection is supported in both SFTP and FTPS.
- Key-based authentication is supported in SFTP. On the contrary, third party signed certificate is used in FTPS.
- Both supported host identity verification.
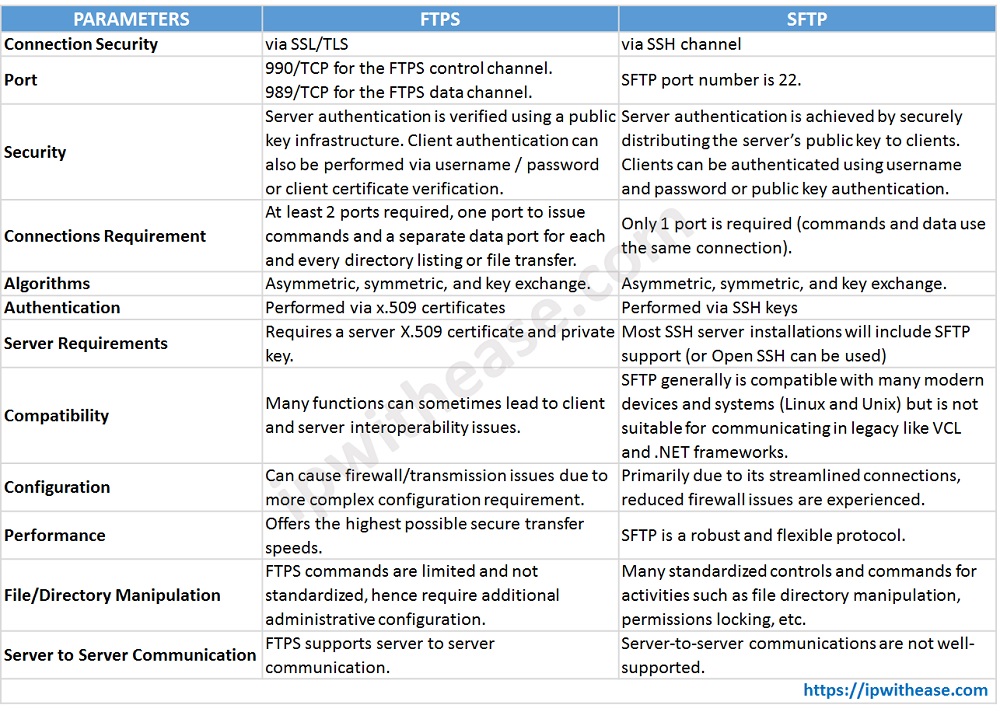
Comparison Table: FTPS vs SFTP
| PARAMETER | FTPS | SFTP |
|---|---|---|
| Connection Security | via SSL/TLS | via SSH channel |
| Port | 990/TCP for the FTPS control channel. 989/TCP for the FTPS data channel. | SFTP port number is 22. |
| Security | Server authentication is verified using a public key infrastructure. Client authentication can also be performed via username / password or client certificate verification. | Server authentication is achieved by securely distributing the server’s public key to clients. Clients can be authenticated using username and password or public key authentication. |
| Connections Requirement | At least 2 ports required, one port to issue commands and a separate data port for each and every directory listing or file transfer. | Only 1 port is required (commands and data use the same connection). |
| Algorithms | Asymmetric, symmetric, and key exchange. | Asymmetric, symmetric, and key exchange. |
| Authentication | Performed via x.509 certificates | Performed via SSH keys |
| Server Requirements | Requires a server X.509 certificate and private key. | Most SSH server installations will include SFTP support (or Open SSH can be used) |
| Compatibility | Many functions can sometimes lead to client and server interoperability issues. | SFTP generally is compatible with many modern devices and systems (Linux and Unix) but is not suitable for communicating in legacy like VCL and .NET frameworks. |
| Configuration | Can cause firewall/transmission issues due to more complex configuration requirement. | Primarily due to its streamlined connections, reduced firewall issues are experienced. |
| Performance | Offers the highest possible secure transfer speeds. | SFTP is a robust and flexible protocol. |
| File/Directory Manipulation | FTPS commands are limited and not standardized, hence require additional administrative configuration. | Many standardized controls and commands for activities such as file directory manipulation, permissions locking, etc. |
| Server to Server Communication | FTPS supports server to server communication. | Server-to-server communications are not well-supported. |
![]()
Download the comparison table here.
Conclusion
FTPS was created as an enhanced version of FTP to add security framework, while SFTP is an enhanced version of SSH that adds easy file transfer capabilities to the already secure SSH. FTPS uses two channels to facilitate control communications and data transfer, while SFTP only uses one. FTPS transfers data in a human readable format, while SFTP transfers data in binary format. While FTPS is widely known globally, SFTP has the advantage of being more secure.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj