Hashing is a powerful cryptographic technique used to store and secure data. It’s an essential part of many digital security systems, from digital wallets to online banking. But what is hashing, and how can you use it in your applications? This guide will introduce you to the basics of hashing and explain how to use it to protect your data. You’ll learn the different types of hashing algorithms, how they work, and the advantages and disadvantages of each. You’ll also get tips on how to apply hashing to keep your data safe. By the end, you’ll have a better understanding of how hashing works and how to use it in your applications.
What is Hashing?
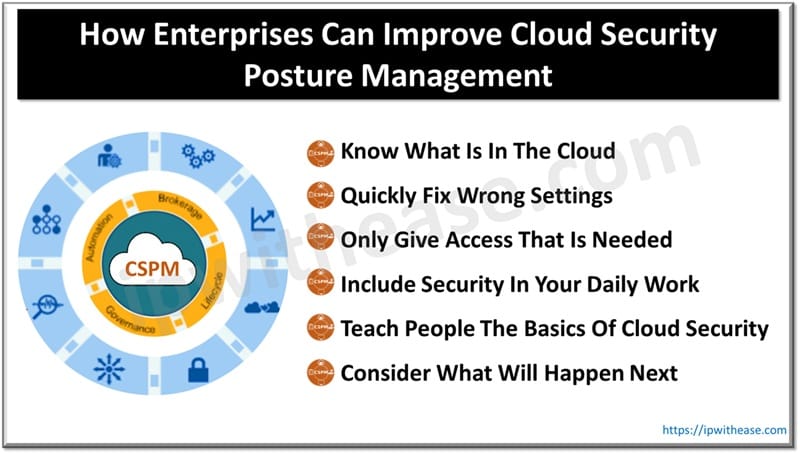
Hashing is a technique used to process and store data. It’s used in many applications, from creating digital signatures to generating unique identifiers for images. Hashing is one-way — once you’ve hashed data, there’s no way to get that data back again. It’s a function that takes any amount of data as an input and produces a fixed-length string as the output.
There are many different types of hashing algorithms, which have different properties and security levels. Hashing is often used together with encryption methods like cryptography or digital signatures.
Uses of Hashing
Hashing has a number of uses, including:
- Creating digital signatures – Hashing is used to sign data in digital signatures. This allows anyone to verify the authenticity of a document or message while keeping the contents of that data private.
- Uniquely identifying data – Hashing can be used to generate a unique identifier for any kind of data, like images or documents.
- Protecting sensitive data – Hashing can also be used to protect sensitive data.
- Protecting passwords – You can use hashing to store passwords in databases or other systems. Anyone accessing the data will not be able to see the actual passwords.
- Efficient data storage – Hashing can also be used to store data more efficiently.
Types of Hashing Algorithms
Hashing algorithms are one-way mathematical functions that take any amount of data as input and produce a fixed-length string as the output. There are many different types of hashing algorithms, each with different properties and security levels. The main types of hashing algorithms are:
- Hash functions – Hash functions have weaker security than other types of hashing algorithms, but they have other advantages. They’re very fast and easy to implement in software.
- Message Authentication Codes (MACs) – MACs are stronger than hash functions, but they’re also slower and more difficult to implement. –
- Secure Hashing Algorithms (SHA) – SHA algorithms are designed to generate a secure hash value, but they’re slower than MACs.
- Randomized Hashing Algorithms – These algorithms are designed to produce a hash value that’s both secure and random so that two pieces of data that are highly similar wouldn’t produce the same hash value.
How Hashing Algorithms work?
To understand how hashing algorithms work, let’s take a look at a simple example. Imagine you want to hash the word “kick.” To do this, you’d use a hashing algorithm to convert the word to numbers and letters. In this example, you’d convert “kick” to “9824”. The first number (in this case, “9”) is the hash value, while the second number (“9824”) is an identifier.
When you hash “kick,” the output will always be “9824” — even if you replace the word “kick” with another word, the output will stay the same.
Advantages & Disadvantages of different Hashing Algorithms
- Hash functions are the weakest hashing algorithms. However, they also have certain advantages, such as requiring very little processing power and being easy to implement.
- MACs are stronger than hash functions, but they’re slower and more difficult to implement.
- SHA algorithms are designed to generate a secure hash value, but they’re slower than MACs.
- Randomized hashing algorithms are designed to produce a hash value that’s both secure and random so that two pieces of data that are highly similar wouldn’t produce the same hash value.
- Since all hashing algorithms produce a fixed-length string, they’re great for storing data. You can use hashing to uniquely identify data, protect it, or store it more efficiently.
- Hashing is also a great way to sign documents or authenticate users.
Best Practices for using Hashing
Hashing is a powerful technique, but it’s only effective if you use it correctly. To make the most of hashing, follow these best practices:
- Use the right hashing algorithm – Each hashing algorithm has different properties, so make sure you choose the right one for your application.
- Use the right length for the hash value – Hashing algorithms produce a fixed-length output. Make sure you choose an output length that’s appropriate for your application.
- Choose a secure hashing algorithm – Some hashing algorithms are more secure than others. Make sure you choose a secure algorithm that’s appropriate for your application.
- Store the hashed data in addition to the hash value – Storing only the hash value isn’t secure. Make sure you store the hashed data in addition to the hash value.
- Store the hashing algorithm and input data – If someone figures out how you’re hashing data, they’ll know how to reverse the process. Make sure you store the hashing algorithm and input data.
- Use multiple hashes – Hashing provides a high level of security, but it’s not impregnable. Make sure you use multiple hashes to protect sensitive data.
How to use hashing in your code?
Python

Hashing vs Encryption
Hashing and encryption are both cryptographic techniques.
- Hashing is one-way, while encryption is two-way — this means that data can be converted back and forth between its original form and the encrypted form.
- Hashing algorithms only produce a fixed-length output, while encryption algorithms produce variable-length output. This means that data encrypted with a certain key will always be the same length.
- Hashing and encryption both protect data, but they work in different ways. Hashing protects by producing a fixed-length output that cannot be converted back to its original form. Encryption, on the other hand, uses a secret key to convert data back and forth between its original form and encrypted form.
How to use Hashing in your Applications?
- To use hashing in your application, you first need to choose the right hashing algorithm for your needs.
- Once you’ve determined which algorithm you want to use, you can easily implement it in your code.
- When you implement hashing in your code, you need to choose the right algorithm and length for the hash value.
- Next, you’ll need to store the hashed data in addition to the hash value.
- Finally, you need to store the hashing algorithm and input data. With these steps, you can protect sensitive data, store data more efficiently, and sign documents with digital signatures.
Continue Reading:
What is Encryption? Detailed Explanation
P2P Authentication: PAP and CHAP Protocols
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj