Table of Contents
IAM (Identity Access Management) and PAM (Privilege Account Management) systems are used sometimes interchangeably as they overlap each other to some extent however both handle different sets of users and systems within an organization. IAM is more towards users however PAM is more towards access controls.
Today we look at these two major terminologies and concepts – Identity access management and Privilege access management, understand their key differences and use cases.
About IAM (Identity Access Management)
IAM is a set of policies and technologies which enable IT managers to control everyday user’s access to applications and information within an organization. In early days there was manual tracking of user identities which left organizations vulnerable from both insider and outsider attacks. IAM automation helped to have high level of control over user identities and maintaining an access audit trail to corporate data and information for compliance purposes.
Leading IAM solutions available in the market both on premises or cloud based let IT managers assign access as per individual role or job responsibility and as the user role changes IAM solution will automatically add or remove access. This also strengthens the password management system with features such as Single sign-on or multi factor authentication.
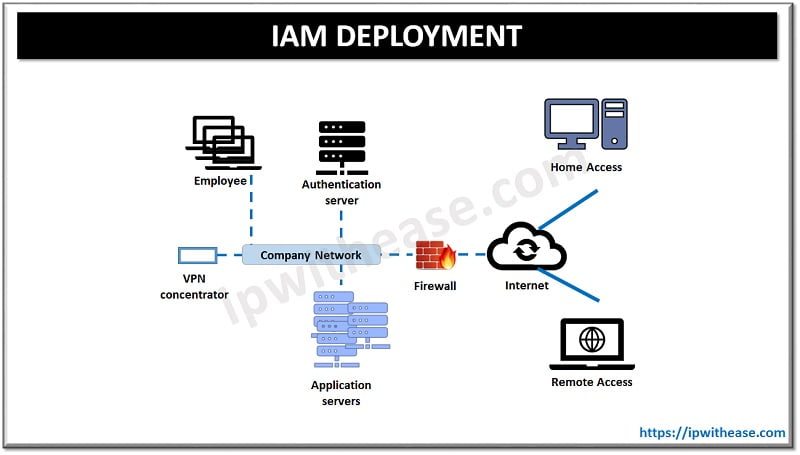
How does IAM work?
IAM Pros and Cons
PROS
- Stronger authentication for PAM password vault
- Centralized secure privilege access to sensitive resources via single sign-on
- Reduction in password management due to Single sign on
- Greater control over user access and reduction in risk of data breach
- Strengthens internal policy compliance and reduction in financials, labour, time and resources required
- OnDemand reports for audit
CONS
- Complex to deploy depending on scope and size and entities involved
- Balancing ease of use and security
- Distributed workforce and applications
- Bring your own device challenge
About PAM (Privilege Access Management)
Privilege access system is a subset of IAM and focuses on protection of privileged accounts. (Limited in number having highly sensitive information residing)
Privilege access systems define which employees, partners, vendors and applications have level of access for specific accounts or data. Implementation of PAM is a mix of software, processes, and enforcement which limits only those with privileged access can have access to most critical data and assets.
It monitors users having elevated access to ensure data and information is securely held. While implementing a PAM system, the strategy needs to be built to ensure what kind of data and assets would require PAM and establish a process that dictates which employees or departments will have what level of access to those resources.
How does PAM work?
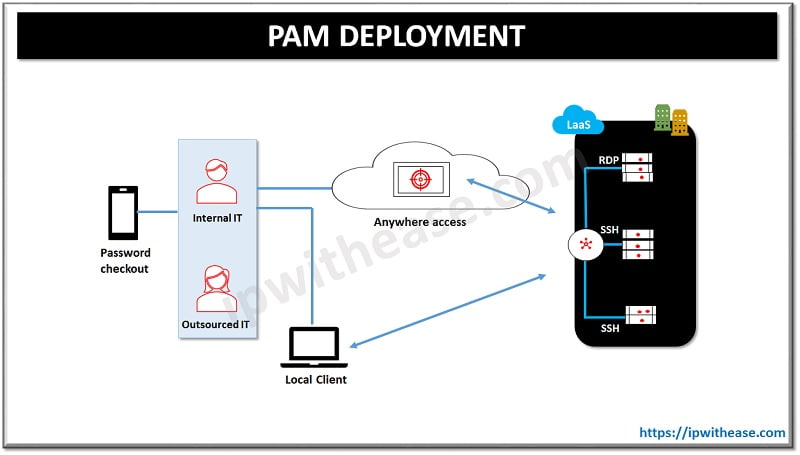
PAM Pros and Cons
PROS
- Helps to block malicious parties
- Grant access only to those who needs it and operates on principle of least privileges
- Helps to monitor suspicious activity
- Adherence to regulatory standards
- Centralized access to data and systems
- Prevention of stolen credentials
- Limited access by creating a system of privileged or non-privileged accounts
- Secure organization data and assets and reduces risk of breach or exposure
- Fewer helpdesk calls
- Simplified management of privilege requests
CONS
- Blanket access rights
- Information overload
Comparison Table: IAM vs PAM
Below table summarizes the difference between the two:
| FUNCTION | IAM | PAM |
| Definition | IAM is a set of policies and technologies which enable IT managers to control everyday user’s access to applications and information within an organization | Privilege access system is a subset of IAM and focuses on protection of privileged accounts. |
| Technology | Supports Lightweight directory access protocol (LDAP), SAML, Open ID, OAuth, Kerberos, Radius | Supports Lightweight directory access protocol (LDAP) and SAML |
| Features | •Granular controls Flexible security credential management •Supports multi factor authentication for secure access •Centralized control of users and security credentials •Permissions based on organization groups •Control over resource creation | •Session monitoring of critical credentials to manage or protect confidential information •Limit account usage based on specified time limit •Auto discovery of privileged credentials •Complete view of what happens when access is requested, approved and performed •Evidence of recording (from access performed correctly or not) |
| Applications | Idaptive, Cisco, Okta, Ping, OneLogin etc | Arcon, BeyondTrust, Centrify, CyberArk, Foxpass etc. |
| Download the comparison table: IAM vs PAM | ||
Continue Reading:
Introduction to IAM (Identity access manager) in AWS
Top 6 Identity and Access Management Companies (IAM)
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj