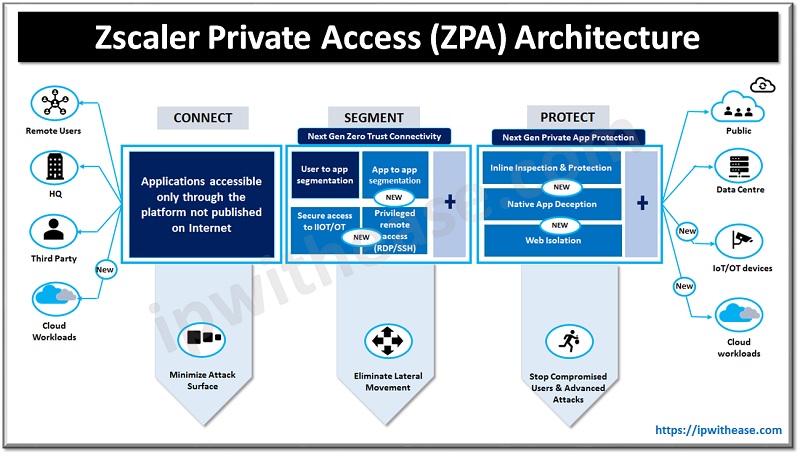
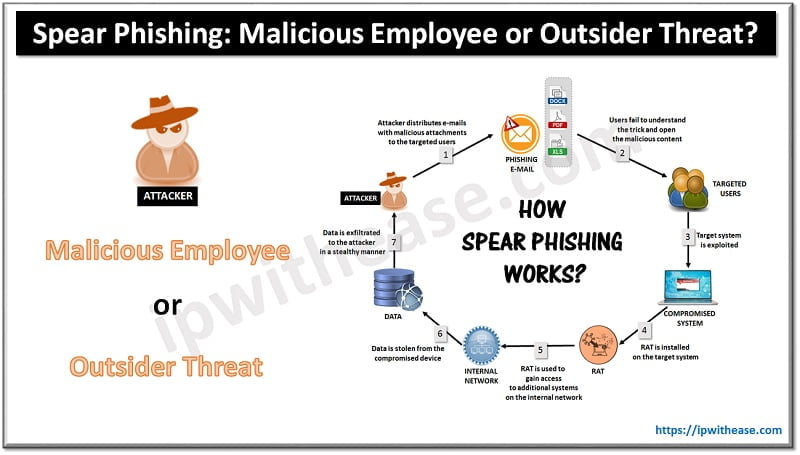
When you assess a network’s vulnerability, you’re not doing it because you think the engineers and tech specialists did a bad job at designing it. The purpose of such a process is to review and analyze a company’s network infrastructure in order to detect potential cybersecurity vulnerabilities and security loopholes.
Due to this review and analysis, you can assess the strength of your network security. It’s also a great opportunity to uncover any security vulnerabilities that have the potential to become a huge liability if not taken care of.
Furthermore, as regulations become more strict, companies must pay a lot more attention to cybersecurity and defense against cyber threats. Otherwise, you risk a data breach and a huge fine if it’s revealed your systems were not up to date.

Steps To Conduct A Network Vulnerability Assessment
Still, if you’ve never done a network vulnerability assessment before, it can be a bit intimidating. Therefore, today, we’ll walk you through the process and have a look at what happens with every step.
1. Establish the scope of the assessment
As the workplace is turning more toward a hybrid model, the inner structure of a company becomes more dynamic. And since most companies are powered by technology, the network infrastructure is getting more complex every day.
If, back in the day, management only had to care about laptops and PCs, nowadays, there’s a plethora of devices that come in and out of the workplace and the company network. As a result, a company’s network can be quite tangled and difficult to understand without taking the proper steps.
The first step is understanding what part of the network you want to assess. You can work on one segment at a time, such as mobile and/or remote connections, laptops, on-site servers, and so on.
Also, keep in mind that a vulnerability assessment is not a penetration test. A pen test is a simulation of a cyber attack performed by someone you hired for this very purpose. In reality, to comply with regulations, many businesses choose to conduct both pen tests and vulnerability assessments on an ongoing basis.
In summary, your first step is to define the network boundaries, identify assets, and define the purpose and goals of the assessment.
2. Gather information
Once you know what you want to achieve with your assessment, it’s time to start collecting data on the network architecture, hardware and software, security policies and procedures, and other relevant information.
You can do this by gathering internal documentation of the network, inspecting the work areas, discussing with the IT administrators on-site, and using specialized tools.
For instance, you can use the Intruder vulnerability assessment tool to scan a wide range of systems such as websites, servers (public and private), clouds, and devices. If you’re interested in trying it out, sign up for a free trial and see if it fits your company’s needs.
3. Analyze the data
After you’ve gathered all the data, it’s time to run an analysis.
To make sure you’re not missing anything, divide the data into categories. For instance, the information collected from documentation, discussions with the staff, and observation should be separate from the assessment report provided by your vulnerability scanning tool. Besides being in a different format, the assessment report is better organized, and it pinpoints problem areas and vulnerabilities from the start.
We recommend using the report as the basis of your analysis and building up on it using the rest of the information. This way, you’ll have a complete view of the network segment you’ve scanned, and it will be easier to assess the risk of each vulnerability.
4. Develop and implement a plan of action
The reason why cybersecurity specialists are adamant about ongoing vulnerability assessments is the clarity companies get after each round. However, this clarity and understanding of their own vulnerabilities won’t amount to anything if there’s no plan of action.
As soon as you understand your network’s weak points, you have to develop a plan to eliminate or reduce or eliminate them. Start with the most urgent ones (highlighted as severe in your report assessment) and work downwards to the less threatening ones.
5. Monitor and review
The fact that you managed to identify and eliminate a severe vulnerability in your network doesn’t mean your job is done. Cyber threats are constantly evolving, which is why companies must monitor their network’s performance and run periodical penetration tests to identify changes and ensure that the vulnerabilities remain mitigated.
Plus, it’s essential to continue running network vulnerabilities at well-established intervals, to make sure there aren’t any new threats.
Wrap Up
The best way to make sure your network and company data are secure it’s to stay vigilant and continuously work on improving your cybersecurity systems. Companies also have to run regular tests and assessments to see if what they’re doing is efficient against an attack. This is especially important in a growing company with a combination of remote and on-site workers.
Continue Reading:
Network Vulnerabilities and the OSI Model
Network Penetration Testing: What, Why, and How
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.