Table of Contents
Control of access is the primary method for protecting digital assets. It decides who can get to certain details or resources and what they can do with them. It acts like an electronic guard, making sure only people with permission can get in. This important security layer stops wrong or harmful access to sensitive data, such as from hackers, data leaks and other online dangers.
For companies of any magnitude, it is very important to have strong access control and security, whether they are small enterprises or large multinational firms. This means clearly setting out who can use what within the company and making sure that only those with authorized permission are able to access certain areas or information systems.
Establishing and managing these rules for entrance into a business’s digital environment can effectively reduce dangers while also ensuring conformity with industry requirements – maintaining faith from customers as well as stakeholders alike.
Access control has three main models, and each one has its unique features and applications.
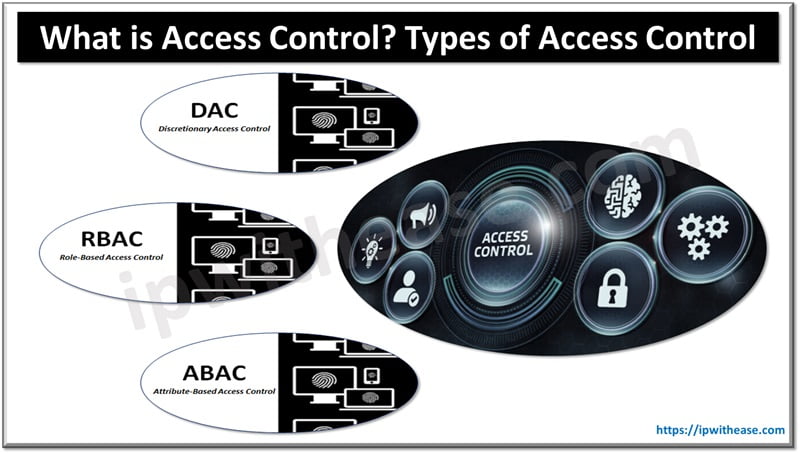
Types of Access Control
Discretionary Access Control (DAC)
Discretionary Access Control (DAC) is an access control model where the owner of data has a lot of say about deciding who can get into their information and what actions they can do. This method gives great flexibility, as it lets people set up custom access permissions for each individual according to their own requirements and choices.
Usage:
DAC is usually used in file systems and operating systems.
- Users are given the choice to decide who can access their data and resources.
- For example, someone who creates a document might choose to share it with some coworkers but not everyone.
- They could also grant different types of access like read-only or full editing permission for the recipients they select.
- This detailed control allows people to handle information sharing as per their own judgment.
Potential Risks:
- Although DAC provides flexibility and control for users, it has some dangers. Since the responsibility of deciding who can access what lies mostly with individual users, there is a chance for human mistakes, oversight or purposeful misuse.
- Depending on personal judgment might make certain sensitive information more vulnerable to being seen or used by people who shouldn’t have access to it.
Related: What is Network Access Control
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) refers to a controlled method of managing access rights within an organization. Unlike the discretionary model where users make individual decisions, RBAC assigns permissions according to a user’s predefined role. This central control grants many benefits such as better efficiency, safety and ease of scaling up.
By setting up roles that match job functions and duties, organizations are able to make the process of giving and taking away access rights easier. For example, a role called “sales manager” could be created which has permission to access customer data, sales reports as well as CRM systems. At the same time another role named “marketing analyst” might have access to market research data along with analytics tools and campaign performance metrics. This structure based on roles makes sure that users can only get the information and resources they need for their specific work tasks. This lowers the chances of wrong entry or losing data security.
Benefits:
- RBAC makes it easier to manage user permissions, which improves administrative efficiency.
- When employees change their jobs or leave the company, we can adjust who has access by changing role assignments instead of modifying permissions for each person individually.
- This method of control is in one place, promoting uniformity and lessening the chance for human mistakes.
- RBAC supports the concept of giving minimum privilege. It means users are allowed only with necessary permissions for their tasks.
- This method assists in reducing possible harm from dishonest insiders or accounts that have been compromised.
Related: Cisco TrustSec: Simplified Network Access Control Policies
Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) is the most advanced and detailed method for handling access permissions. Going beyond role-based models, ABAC considers various attributes linked to both the user and resource in order to decide on authorized access. This active, context-aware way allows organizations to establish very accurate security rules that can be adjusted easily.
Features:
- Many things can be thought of as attributes in an ABAC system, such as user roles and job functions, security clearances, where someone is located geographically or what time of day it is for them specifically.
- Other factors might include what type of device they are using like a laptop versus a mobile phone; whether they’re on the internal or external network; if there’s a good internet connection with low latency (response delay); how sensitive the data being accessed is and its classification according to policies set by organization etc.
- By matching these characteristics to certain access needs, organizations can form complicated access control policies that fit their particular security requirements.
- As an example, an ABAC system may allow entry to a very delicate document just for those workers who possess a particular security authorization, when they access the system from an assigned company network within working hours and use a device provided by the same company.
- ABAC, with its adaptability and accuracy functions, helps businesses to decrease risks, comply with rules set by regulators and maintain the security of sensitive data from unauthorized entry. A
- s the complexity and variability of present IT situations increase, ABAC turns into a robust defender for digital possessions.
Every access control model has its own strengths, so many organizations use a combination of different models to create a robust security framework. The choice depends on the size and type of organization, regulatory needs, and how critical is the data being protected.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.