Table of Contents
Introduction to Rainbow Table
A Rainbow table is called any pre-computed table that is used for caching many outputs of cryptographic hash functions. They are used mainly from hackers in order to crack password hashes and for recovering key derivation functions such as (credit card data etc).
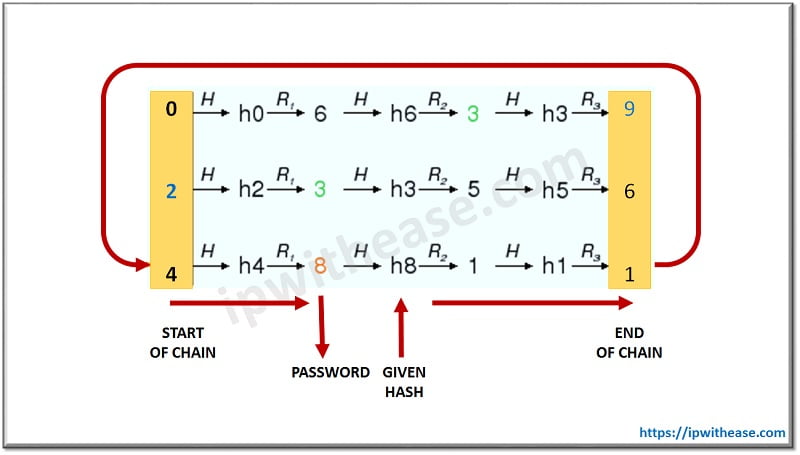
A common specification of a Rainbow Table is the ability to invert the disintegration of the function in order to determine what the possible access code is in simple text. It is possible to have two different access passwords to contain the same hash, giving the advantage to the hacker to ignore what the initial access password was.
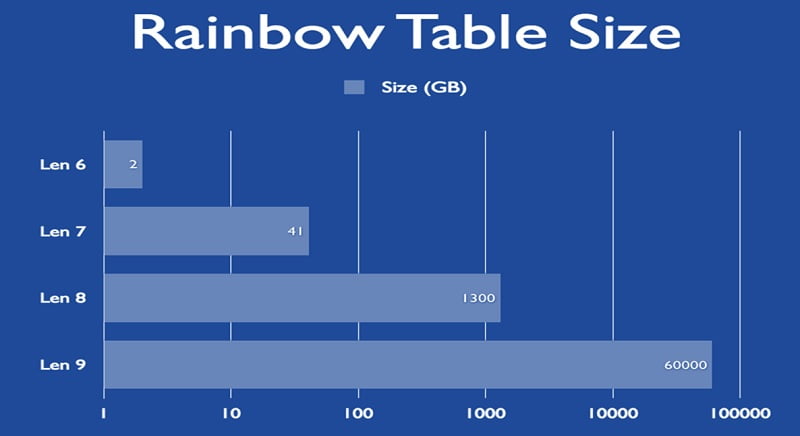
Rainbow Tables can crack access passwords in a very short period of time compared to other methods (Brute Force Attack, etc). On the other hand, this kind of process needs a huge amount of storage capacity (Terabytes), which is not very difficult to find nowadays.
How does Rainbow Table Attack Work
The main functionality behind Rainbow Tables is the ability to perform cryptanalysis rapidly and effectively, also known as crypto-algorithms. Below we will analyze the most common types:
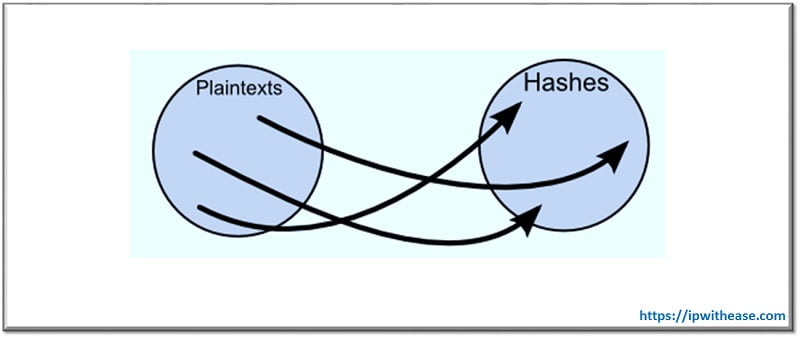
- Direct Mapping: In this method, hash functions map plaintexts to hashes so that you can’t find a plain text from its original hash, as described in the diagram.
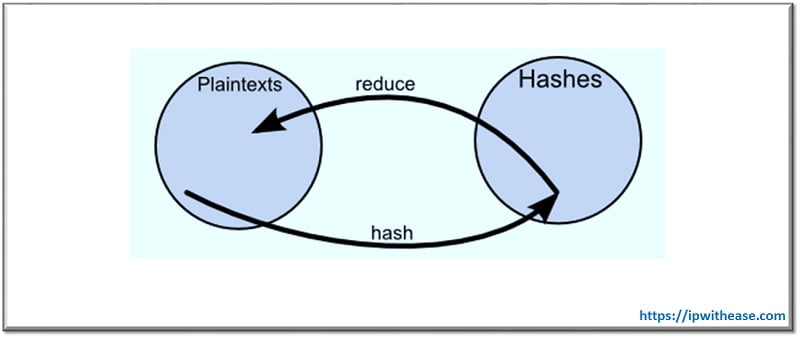
- Reduced Mapping: In this method, when you ask the hash of a plaintext, and take the reduction of the hash, the outcome will not give you the original plain text.
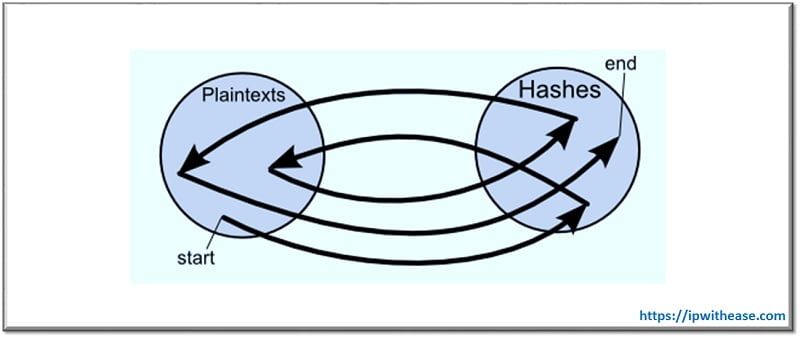
- Crossway Mapping: In this method, chains in a rainbow table start with an arbitrary plain text, then it hashes and reduces the hash to another plain text. The Rainbow Table stores the starting plain text, and the final hash end with millions of hashes.
Advantages and Disadvantages of Rainbow Table Attacks
Advantages:
- Hacker attacks using Rainbow Tables have the advantage of most data being pre-computed, resulting in an easy hack access. Therefore the whole process is just a simple search and compare operation on the table unlike the Brute Force Attacks.
- Another crucial advantage using of Rainbow Tables is the ability of authentication without serious obstacles. This occurs because the exact password string does not have to be known or estimated. If a hash match occurs, then it is enough for the attack to be performed.
Disadvantages:
- One main and most common problem when dealing with Rainbow Table Attacks is the fact that these tables need to be stored in a huge memory (Hard Disks). Sometimes Terabytes are needed, resulting in an increased maintenance cost.
- Another disadvantage of Rainbow Tables is the fact that If the hash the hacker is trying to break is not in his table, then he will be unable to find the resultant password in a short period of time. This gives the limitation of the table in use.
Mitigation from Rainbow Table Attacks
Cybersecurity community has addressed the Rainbow Table attacks all these years and have invented very effective ways of dealing with them. Some of the most effective and widely preferred methods are enlisted as under:
- Salt Technique: The most commonly used method to prevent a Rainbow Table Attack nowadays is called “Salt”. In this method random data are passed in to the hash function along with the plain text. The result of this method is the creation of a unique hash for every password preventing duplicated values.
- Key Stretching: This is another very effective method to prevent a Rainbow Table Attack and is used against hackers. The main concept of this method is to insert intermediate hash key values in between the plain text and the password, in order to increase the computation time required by the attack. The result is the obvious time expiration and failure of the attack.
Conclusion
Rainbow Table Attack is used from hackers nowadays for the main advantage of an extremely high speed technique to crack passwords. In minimum time, security Scientists have addressed this hacking activity and invented sophisticated techniques to resolve it, the most well-known is “Salt” and “Key Stretching”.
Unlike other techniques, huge storage is needed for Rainbow Table Attacks and sadly the decreasing price per Mbyte for storage solutions nowadays doesn’t help our safety. In order to avoid being a victim of Rainbow Table Attack, it is strongly advised to perform frequent password changes.
Continue Reading:
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj