Table of Contents
Due to technology advancements and wide exposure to the Internet many services are getting digital. Digitization has brought with itself a lot of benefits but at the same time there is a flip side to it. Cyberattacks are on rise. They have become more sophisticated and cyber criminals are equipped with modern techniques and tools which could lead to personal data compromise. The cyber criminals are finding new ways and means to get your personal data and information.
In today’s topic we will learn about SIM swapping attacks, how does SIM swapping attack work? Why do SIM attacks take place, techniques to prevent SIM swapping attacks.
What is SIM Swapping?
In SIM swapping attacks, hackers take control of your mobile phone number and inform the mobile telecom provider to link the mobile number to the SIM card which is with the attacker. SIM Swapping procedures are meant to address issues related to SIM card loss or SIM card damage. SIM swapping is required at times to connect mobile phones having embedded SIM or e-SIMS which are quite common nowadays.
Each SIM card has a unique identifier, which tells how a mobile network will verify subscription to service providers and how to deliver phone calls and text messages to the right mobile number. This is also known as ‘Simjacking’ or ‘sim card hacking’. It is a form of identity theft which is often the result of cyber criminals getting hold of your personal information.
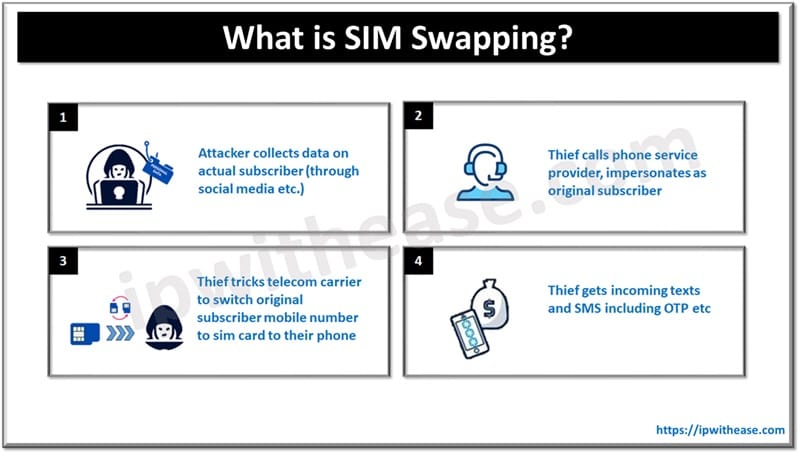
How does SIM Swapping Attack work?
A SIM swapping attack begins with cybercriminals gathering personal information of mobile subscribers. There are various ways and techniques used to gather personal information such as social engineering, phishing, malware, exploiting information by doing research on social media or it could be gathered via a data breach.
Post acquiring all information of the subscriber, the hacker would be able to convince the mobile operator that he is a legit subscriber of that number and request transfer of subscriber mobile number to the new SIM card under their control. Hacker takes over account and all details – SMS and voice calls received on this new SIM. Using this technique hackers can perform online banking frauds and also bypass Multi factor authentication (MFA).
Causes of SIM Swapping Attacks
- Weaker customer authentication mechanism
- Lack of cyber training or hygiene
- Poor level of risk awareness
Protection and Prevention Against SIM Swapping
The alarming rise in SIM swapping incidents and sophisticated techniques employed by hacker calls for proactive measure’s individuals, telecom operators, organizations and government entities need to take from failing being victim to this cyber threat. Let’s look at strategies which could help in protecting and prevent against SIM swapping:
- Training and Awareness – Employees need to be educated on risks of SIM swapping and trained to identify social engineering attempts. Potential consequences of divulging personal information risks need to be understood and communicated via effective trainings and awareness programs.
- Stronger Authentication Protocols – employees need to use multifactor authentication and use authenticator apps instead of SMS
- Securing Communication Channels – use of secure communication channels is important for information exchange which is sensitive in nature. Ensure that employees make the right choice by picking security first instead of using insecure channels for communication.
- Ongoing Security Audits – regular security audits help to identify vulnerabilities and weaknesses in systems proactively and fix them to strengthen cyber security measures. Address issues related to potential data breaches promptly.
- Comprehensive Incident Response Plans – Comprehensive incident response plan should include all kinds of attack scenarios and how to deal with them including SIM swapping attacks. Engagement with law enforcement and relevant agencies handling and cooperation with them should be part of the incident response plan.
- Account Activity Monitoring – implement systems to monitor activities of accounts for any unusual and suspicious behaviours which could help in detection of potential SIM swapping attempts immediately.
How do I know if I was SIM Swapped?
If you’ve been SIM swapped, you may notice the following warning signs:
1. Sudden Loss of Cellular Service
- Your phone unexpectedly loses the ability to make calls, send texts, or use mobile data (but Wi-Fi still works).
- Your phone shows “No Service” or “Emergency Calls Only” despite being in a coverage area.
2. Unusual Account Activity
- You receive emails about password reset requests that you didn’t initiate.
- You get locked out of your email, bank, or social media accounts.
- Unauthorized transactions appear on your financial accounts.
3. You Stop Receiving Calls or Texts
- Friends, family, or colleagues say they tried to call or text you, but you didn’t receive anything.
- Two-factor authentication (2FA) codes no longer reach your phone.
4. Your Mobile Carrier Contacts You About a SIM Change
- You receive a notification from your carrier confirming a SIM card swap or a request to change your account details that you didn’t initiate.
5. Unfamiliar Devices Appear on Your Accounts
- When checking account login history (e.g., Google, Facebook, or bank accounts), you notice logins from unknown devices or locations.
What to Do If You Suspect a SIM Swap Attack
1. Contact Your Mobile Carrier Immediately
- Report the unauthorized SIM swap and ask them to restore your phone number to your original SIM.
- Set up additional security measures, like a PIN or passcode, for your carrier account.
2. Change Passwords & Enable Multi-Factor Authentication (MFA)
- Secure all critical accounts (email, bank, social media) by changing passwords and enabling app-based MFA instead of SMS-based authentication.
3. Check for Unauthorized Transactions
- Review your bank statements, PayPal, crypto wallets, and other financial accounts for any suspicious transactions.
4. Alert Your Bank & Credit Card Providers
- Inform them about the potential fraud so they can monitor your accounts for suspicious activity.
5. Report the Incident
- File a report with your local authorities or cybersecurity agencies such as the FBI’s IC3 (if in the U.S.).
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj