Table of Contents
A data breach is something no one wants to hear in their lives. However, it’s something that hits the headlines once in a while, and it attracts everyone’s attention. Cybercriminals are always busy exposing essential information from individuals and organizations.
Yes, it’s a real threat, but the question is, what can we do about it? There are billions of records that are publicly exposed. According to Forbes, the first six months of 2019 had more than 4 billion record breaches.
That is inclusive of passwords, emails, and other personal and organization data. While we wonder how they do, cybercriminals tap the basic requirements needed for a successful hack.
Impact of Data Breaches
First, it hurts the victims, and that includes both companies, businesses, and individuals. The next thing that follows is the heartbreaks, headaches, and wondering if it will happen again. That is when you ponder everything from changing passwords to talking to professionals.
We cannot forget that there is the cost involved in bringing things back to normalcy. Depending on the data breach, companies are the ones that suffer most. They also need to alert victims of the data breach as they advise them on what to do.
Later, it’s all about placing more protection measures as the need to change routine arises. In general, people go through much, and it’s expensive to manage a data security issue. Apart from the finances, trust in the company or organization reduces, which is never good for business.
On an individual level, data breaches make you feel insecure. If you intercept a phone to check someone’s call history online, it’ll not be a good idea if they know. It will lead to changing passwords and even the phone itself.
So, whether it’s an organization or individual affected, the repercussions are always graver. With that, let’s explore the various measures you can take when you face a data breach.
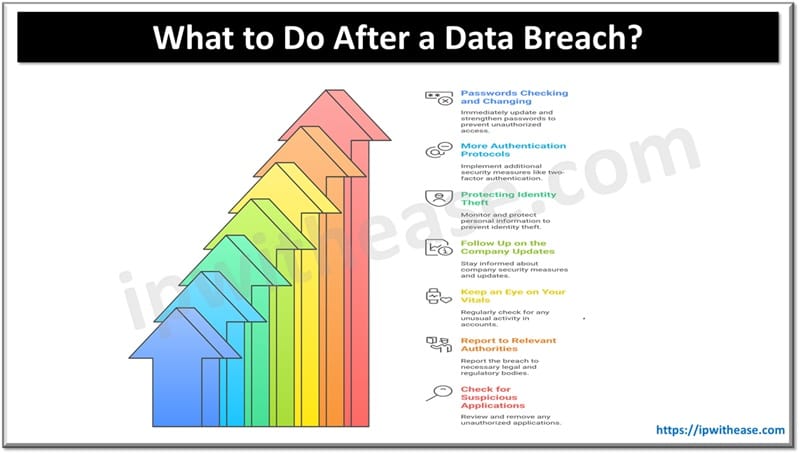
What to Do After a Data Breach?
Passwords Checking and Changing
This is the first thing you do when a data breach occurs. It’s essential to keep changing your passwords once in a while. To make it harder for the hacker, don’t use the same password in multiple accounts.
An OK password should have six characters and above, but strong ones consider eight to be the minimum. Create a good mixture of letters, numbers, and symbols. If you have many accounts to deal with, write them down somewhere safe or use a password manager.
Using password generators is another way to create strong passwords.
More Authentication Protocols
These days, we have protocols like two-step verification, and it helps verify that you are the one accessing the account. You may also know it as the two-factor verification. That’s an additional security layer, and you will find it in your Google account as a start.
Online banking services also have the same. There are other ways to allow more authentication, such as face recognition and fingerprints where possible. It mostly applies to device logins, but apps have also come up with ways to accommodate such.
With another way to verify your way in, hackers will never be able to get through. Even the recovery options will fail too.
Protecting Identity Theft
This one is for those who want to ensure that they are entirely secure. There are identity protection services that you can register with if you want a third eye. However, you should be prepared to dig deeper into your pockets if you don’t do it yourself.
In return, such companies will offer essential services and better recovery options. In short, they will help you to compensate if there is a data breach.
Follow Up on the Company Updates
If the breached data involves a major company, there should be updates on the steps taken. Google and Facebook are some of the examples that follow up on the hacks. They send messages to customers, take necessary action, and advise the affected customers on what to do.
So, as you secure your account, make sure you get updates from the company/organization involved.
Keep an Eye on Your Vitals
Once you have taken all the necessary measures, now it’s time for the watch. Pay attention to the activities happening in your accounts and the associated companies as well. If it’s a bank involved, then check on your financial transactions.
If you notice a suspicious transaction, ensure that the bank knows as you counter it.
Report to Relevant Authorities
Data breaches also constitute crimes. So, the involved government officials should know. You can visit their premises or check online for their websites. The engaged experts help in assessing the situation.
If it’s a major threat involving others, your information will help the authorities take extra steps. There is also advice and tips given to you to reduce the use of your data elsewhere.
Check for Suspicious Applications
Data breaches are also caused by applications that come to your phone, tablet, or computer. That prompts you to check on any apps you download or the things you click on websites. If you see that what an app is asking for is something you can’t give, don’t allow it.
If you think someone is spying on you, you can dial *001# to check for any hidden apps. Advanced devices will also show the hidden apps via the settings. In extreme cases, that is where you factory reset your device but make sure you back up essential data first.
Conclusion
When the nightmare comes to you, you have a few points to help in restoring things. Data breaches are essential to the involved criminals since they fetch them a lot of money. In other cases, they can do it just to show how vulnerable a company/organization is.
You, on the other hand, need to keep your security tight. This world is full of evil, and you never know when it gets to you. Last but not least, always educate yourself on internet security and how to stay safe online.
Why? Because cybercriminals are advancing their knowledge too.
Related – Top 5 Data Breaches in Cyber Security
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.