Table of Contents
In this blog, we look more in detail about Zscaler Private Access (ZPA) Architecture, how it helps to provide secure access to private applications running over cloud and On Premises, its features, advantages, use cases etc.
Decentralized over a decade of data, assets, applications, services, use of DAAS , across multiple environments and cloud services have made traditional castle and moat security strategy somewhat ineffective and the security of the network is no longer confined to physical boundaries of devices or users or location. The traditional firewalls, VPNs, and private applications are a massive attack surface and network security approach allows lateral movement.
Zscaler Private Access (ZPA) Architecture
Zscaler Private access is a cloud service which provides zero trust, secure remote access to internal applications running on cloud or in-prem data center. With Zscaler Private access applications are never exposed to the internet, thus making them completely invisible to unauthorized users. The service enables applications to connect to users via inside out connectivity instead of extending internal network to them.
Key Principles
Zero trust access is based on four key principles:
- Applications access no longer need access to network or use VPN
- Applications are not visible to unauthorized users via inside out connections
- Segmentation at application level and not at network level limit user access to application hence limit lateral movement
- Internet is redefined as new secure network via end-to-end encrypted TLS tunnels
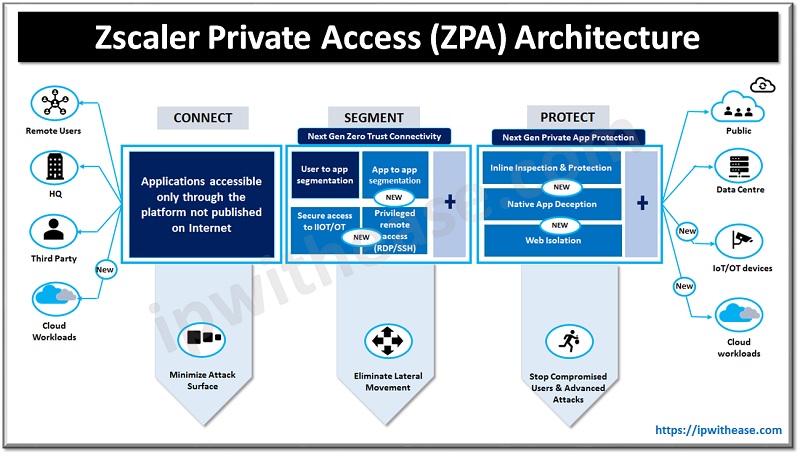
Components of Zscaler Private Access (ZPA) Architecture
Zscaler private access provides a simple, secure and effective way to connect to internal applications. Access is based on policies created by administrators within the ZPA admin portal hosted on Zscaler cloud. On the endpoint a small piece of Zscaler is installed which ensures that the user device posture and extends the secure micro tunnel out to the Zscaler cloud when the user tries to access the application.
ZPA places a small software called App connector which is deployed as a Virtual machine which is used to extend a micro tunnel out to Zscaler cloud and establishes an outbound connection to cloud and does not entertain any inbound requests to prevent DDoS attacks. It is 100% software defined and does not require any device or appliance.
- Zscaler enforcement Node (ZEN)
- Establish a secure connection between Zscaler app and App connector
- Hosted over cloud
- Provides authentication
- Customizable by administrator
- Zscaler App
- Mobile component (client) installed on endpoints
- Enables access requests to App
- App Connector
- Front end for apps in Azure, AWS and other public cloud services
- Listener for application access requests
- No inbound connections permitted
Features of Zscaler Private Access
- Consistent user experience for both cloud or on-prem applications
- Service integration with Okta and other single sign in providers
- Browser access for all web apps , allow connectivity without Zscaler app
- Customization of re-authentication timeframes
- Discovery of unknown applications and application of granular access controls
- View past and real time user activity
- View application health, servers and connectors
- Auto streaming of audit logs to SIEM
- Visibility to all devices connecting to Zscaler
- Global policies hosted on Zscaler cloud to determine user access to applications
- Standardization of security for current and newly acquired assets
Use cases for Zscaler Private Access
- Secure connectivity for private applications across any hybrid or multi cloud environments
- IT integration during merger and acquisitions without the need to converge networks and IP address
- Secure third-party access to specific application
- Alternative to VPN services
Continue Reading
Introduction to Zscaler DAS – Deployment Advisory Services
What is ZTNA (Zero Trust Network Access)
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj